Android device security
BigFix Mobile provides various device security management features through which you can protect corporate content and devices.
-
By default, BigFix Mobile enforces certain security policies on enrolled Android devices based on the device type, without requiring IT admins to set up or customize any settings.
-
Through WebUI pages, IT admins can configure security policies.
-
IT admins can define security policies through custom policies.
-
IT admins can also prevent unauthorized access and sharing of corporate data through MDM actions.
IT admins can enforce corporate data and device security by deploying security policies on the managed Android devices. Device security policy enforcement ensures that all managed devices are compliant as per the organization’s policies. If a device is not compliant, all work apps and work data are blocked in the device unless the device becomes compliant.
Default security policy - General
By default, the following security policies are enforced on all the managed Android devices. The restrictions are effective on devices with Android version 10.0 and above.
The default policy deployed on the enrolled Android devices restricts the installation of apps from any untrusted sources even on the personal profile of the device.
Default security policies- Restrict app installation by
default
DISALLOW_INSTALL. DISALLOW_INSTALL Default - Restrict untrusted app
installation
EnumsUNTRUSTED_APPS_POLICY_UNSPECIFIED Unspecified - Restrict app installation on entire
device
ALLOW_INSTALL_IN_PERSONAL_PROFILE_ONLY - For devices with work profiles, allow untrusted app installation in device's
personal
profile
ALLOW_INSTALL_DEVICE_WIDEAllow - Debugging features are blocked by default.
Default security policy - dedicated devices
In addition to the general default security settings, BigFix Mobile enforces the following default security policies on all dedicated devices.
- Users cannot escape a locked down dedicated device to allow other actions. No other actions are allowed for a locked down dedicated device.
- Safe boot disabled: Booting into safe mode is turned off.
- Screen capture disabled
- Camera disabled
- Factory reset disabled
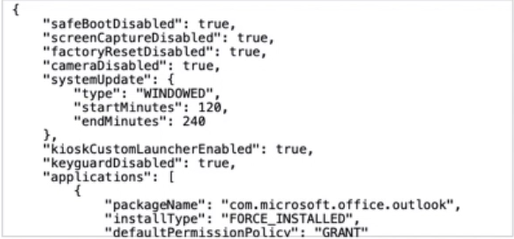
The following code snippet shows the code in the default custom JSON policy file that gets deployed onto dedicated devices on enrollment.
Device security options
| Security type | Applicable device type | Security scope |
|---|---|---|
| Device security | Company-owned devices (fully managed and dedicated Android devices) | At the device level |
| Work security | Work profile of the BYOD Android device | At work profile level |
| Wipe and lock | Company-owned devices(fully managed and dedicated Android devices) | At the device level |
| Compliance enforcement | Applicable to all managed Android devices depending on the policy configurations | At the device level or at work profile level depending on the policy configurations |
| SafetyNet support | ||
| Verify Apps enforcement | IT admins can turn on Verify Apps on
devices. Verify Apps scans apps installed on Android devices for
harmful software before and after they're installed, helping to
ensure that malicious apps can’t compromise corporate data.
Verify Apps must be turned on by default via policy (Go to
ensureVerifyAppsEnabled). |
|
| Hardware security management |
Passcode Policy
Android passcode policies can be managed from the WebUI passcode policy page. IT admin can configure and enforce a password policy to prompt device user to set a PIN/pattern/password of certain type and complexity to unlock the device or to unlock just the work profile.
- Device security
- To enforce device security, ensure that you select the Android Passcode Policy Scope as SCOPE_UNSPECIFIED or SCOPE_DEVICE. Once the user provides the password, the device is unlocked and the user can access apps and data in the device.
- Work security
- Work security policy is enforced only at the work profile level to protect work apps and data in the Android devices. This policy is useful to enforce on a BYOD device to lock only the work data without disturbing the user’s personal data.
Wipe and lock
Through WebUI, IT admins can remotely wipe or lock company-owned Android devices and ensure corporate data security. The Wipe command is used to wipe corporate content from lost or stolen device. The lock command is used to lock lost or stolen device. To learn how to wipe or lock company-owned Android devices through WebUI, see Wipe and lock device.
Compliance enforcement
- Appstore App Policy: Through
application policy, IT admins can enforce rules to protect company apps and
data. For example,
- Control sharing of work data between apps
- Prevent saving of work app data to a personal storage location
- Restrictions Policy: IT admins can enforce restrictions such as accessing a network through WiFi or Bluetooth.
- Custom policies: IT admins can define custom policies in a JSON file, add it to a policy group, and deploy onto the selected devices or onto the MDM server.