Device trust
The Device Trust feature from BigFix Mobile prevents unmanaged devices from accessing enterprise services. It provides an extra layer of security to your organization's application access and protects against potential threats from compromised devices. This extra security helps ensure that your users access applications from a device that you know is trusted.
With the Device Trust feature, administrators can enforce device-level security policies for accessing sensitive applications. This feature uses device attributes, such as operating system, security software, and network information, to assess the trustworthiness of a device before it allows access to protected resources.
BigFix Mobile supports and integrates Okta to establish device trust for iOS and Android mobile devices. For more information on Okta Device Trust, refer to the official documentation at Okta Device Trust solutions | Okta
Application access flow
When a user tries to access a corporate app, BigFix Mobile verifies with Okta whether the device is enrolled and managed. If yes, it allows access to the corporate app. If the device is not enrolled, it is recognized as an untrusted device and prompts the user to enroll with BigFix Mobile before accessing the corporate app.
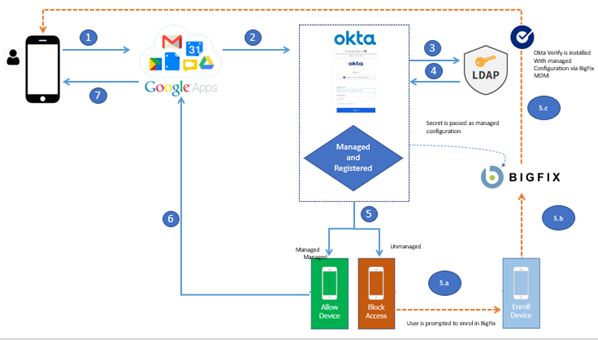
The Okta configuration enables device users to sign in once to establish trust and access all the MCM managed apps without having to sign in for subsequent executions. A typical work flow is as follows:
- A user tries to access a managed app for the first time from an MCM enrolled device.
- The user is prompted to log in to Okta, and then the user enters the organization credentials.
- The credentials are validated against the organization's identity service through Okta Verify.
- The user successfully signs in to Okta.
- The user is redirected to the managed app and accesses it.
- Later uses of the same app or a different managed app do not require the user to sign in again, as the trust relationship is established.
Supported devices
- Android devices running Android 10.0 and later versions
- iOS devices running iOS 11 and later versions
Supported apps
- iOS or Android SAML or WS-Fed cloud apps
Prerequisites
- An Okta tenant (account) must be configured to trust devices. After you
establish trust, the URL and hint are provided. These items are in MCM to
configure applications for device trust.
- Okta configuration for enabling Device Trust
- Configure Okta for BigFix Mobile
- You must add the Okta Verify app to the device during enrollment with the managed configuration
- You must install Google Chrome on the devices that you plan to use the Device Trust feature on because Okta uses Chrome as the default browser.
Okta managed app configurations
With the managed app configurations, you can enable functions that are built into Android Okta Verify and iOS Okta Verify as applicable. You can set up managed configurations for Okta through the WebUI from the App configuration page.
- Bundle ID
- This configuration is required.
- Bundle ID for Android Okta Verify:
com.okta.android.auth - Bundle ID for iOS Okta Verify:
com.okta.mobile
- Bundle ID for Android Okta Verify:
- domainName
-
This managed configuration prepopulates the First, enter your sign-in URL window with a sign-in URL. In this way, device users don't have to enter this value when they add an Okta Verify account.
- managementHint
-
This managed configuration specifies a secret key, which indicates that a device is managed.
| Managed app configuration | Key | Value | Value type | Example |
|---|---|---|---|---|
| Domain name | domainName |
<org_sign-in_URL> |
String | example.okta.com |
|
Management hint |
managementHint |
<secret_key> |
String | 3zr7Q~vw4C16FS2bH8UfS1gJ5cL6sj~x_U9PQ |
For more information, refer to the Okta documentation at Managed app configurations for Android devices | Okta