Update Apple Enrollment Certificate before expiration
To continue to manage the enrolled Apple devices without interruption, you must set up the Fixlet "Update Apple Enrollment Profile before Expiration" as a policy action.
- Apple Enrollment Certificate
- An Apple Enrollment Certificate (Device Identity Certificate) authorizes an MDM device to talk to the MDM Server. All requests from the MDM devices are signed with this Device Identity Certificate. At the time of MDM enrollment, when Apple device communicates with the MDM Server, the MDM Server generates and assigns Unique Device Identity Certificates (or SCEP certificates) to each device. The MDM Server ensures that requests coming from each device are signed by the correct Device Identity certificate; if not, the requests are ignored.
How to identify the devices with expiring Apple Identity Certificates
If you set up the Fixlet Update Apple Enrollment Profile before
Expiration as a policy action with the intended targets selected, you
can get the visibility of the expiration date of Device Identity Certificates for
the targeted Apple devices. The WebUI Modern Client Management dashboard notifies the WebUI user
about the devices with certificates nearing expiry.
The following image shows the WebUI dashboard with “Expiring Certificates” tile that
shows the number of devices with expiring certificates. Clicking on the number shows
the list of devices within 45 days of expiry. 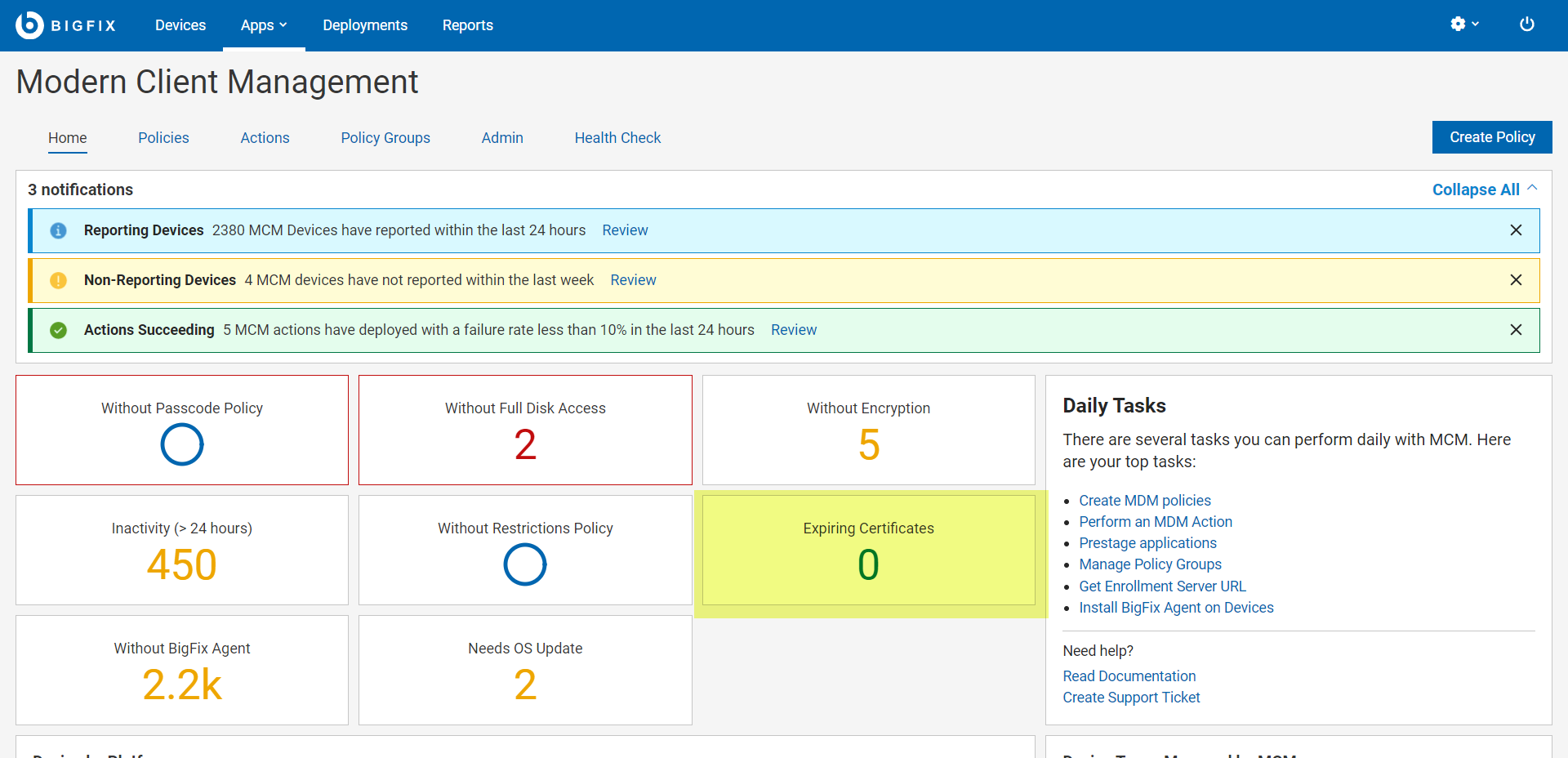
The Update Apple Enrollment Certificate before expiration Fixlet
This Fixlet is available under BESUEM site. If you have Apple Devices in your MCM deployment, you must set up this Fixlet as a policy action with the correct targets selected.- It looks for all devices where the Device Identity Certificate is within 45 days of expiry, which means it has been almost a year since the device last received an enrollment profile and any updated certificates.
- Displays devices with less than 45 days of expiration of their device identity certificates on the main MCM Dashboard in a tile showing Expiring Certificates.
- Initiates an update enrollment profile action to the relevant Apple devices.
If the devices are up and running and check in at least once a day, the
policy action deploys the latest enrollment profile (with the latest
certificates) onto those devices. This auto-renews the certificates for the
devices nearing expiry date and ensures these devices do not stay under the
tile “Expiring Certificate” for more than a day. Internally it does the
following actions:
- Provides a new Device Identity Certificate to the device which allows it to operate successfully for another year
- Pushes the latest TLS certificate’s Intermediate certificate to the device to ensure it is trusted
- Signs the enrollment profile with the latest available signing certificate to ensure the profiles remain "Verified"
How to set up the Fixlet to auto-renew the certificates
- In the BESUEM site, find the Fixlet
Update Apple Enrollment Certificate before expiration. - Select Take Action.
- Change the preset type to Policy.
- Select Dynamically target by property.
- Under the Execution tab:
- Select Reapply this action.
- Select while relevant.
- Select 1 dayThe policy is set to reapply the action once a day while relevant. There is no limit for reapplications.