Creating the authentication profile for Nomad server
The profile is used to authenticate users and to verify user access to target HCL Domino® servers.
About this task
When a user request to a server is found, SafeLinx uses the information in the authentication profile to query the requested Domino servers canonical name in the LDAP servers and use the fully-qualified domain name (FQDN) it found to establish a TCP connection.
If a server name can't be
resolved, the connection terminates. To ensure a server name can be resolved,
specify the server URL when you configure the HTTP access service.
Note: The name of the Nomad web proxy has changed to Nomad
server.
Procedure
-
From the SafeLinx Administrator, in the Tasks tab,
select :
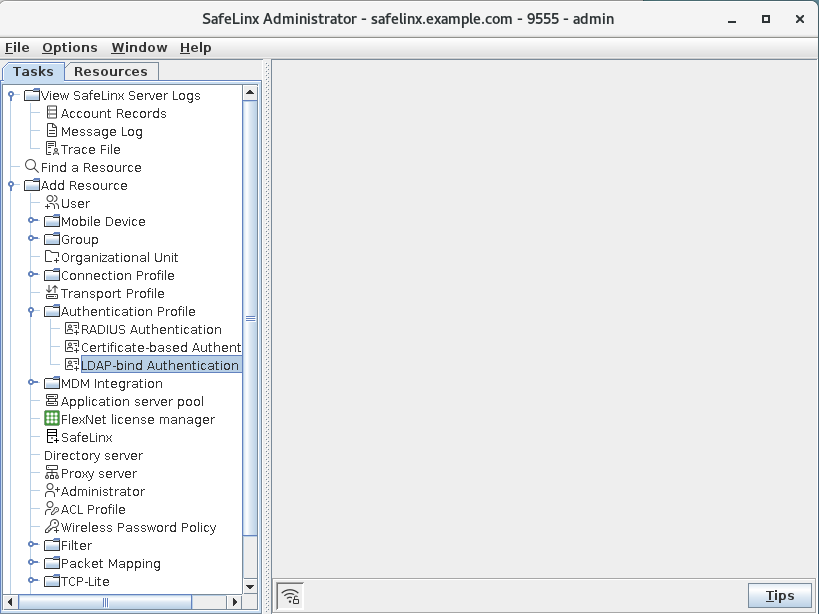
-
Define server information:
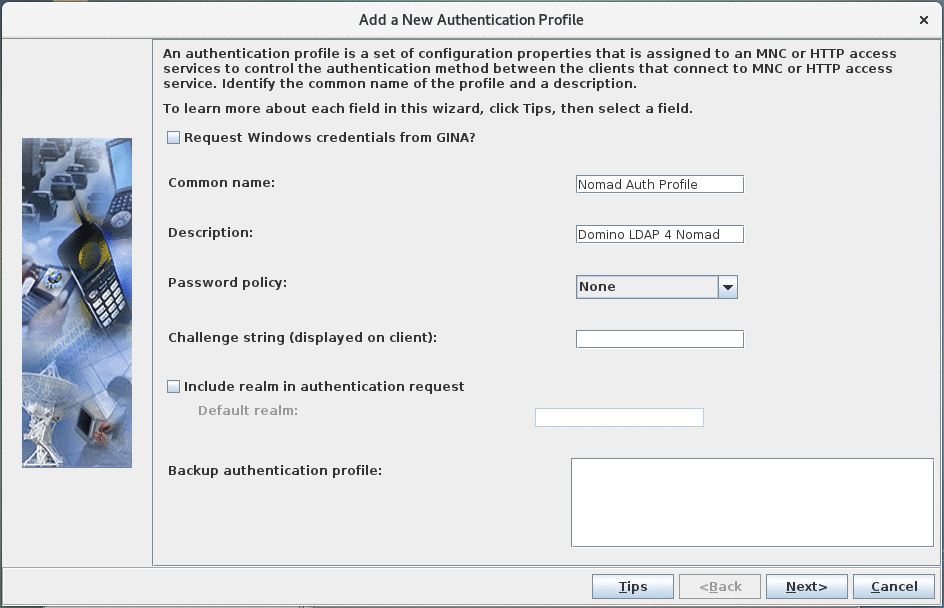
- "Request Windows credentials from GINA" has to be unchecked.
- "Common name" specifies the name of the authentication profile. Choose a descriptive name.
- "Description" can be left empty.
- Set "password policy" to "None" as we will use the LDAP server specified in the previous step to verify credentials.
- Leave "Challenge string" empty.
- Leave "Include realm in authentication request" unchecked
-
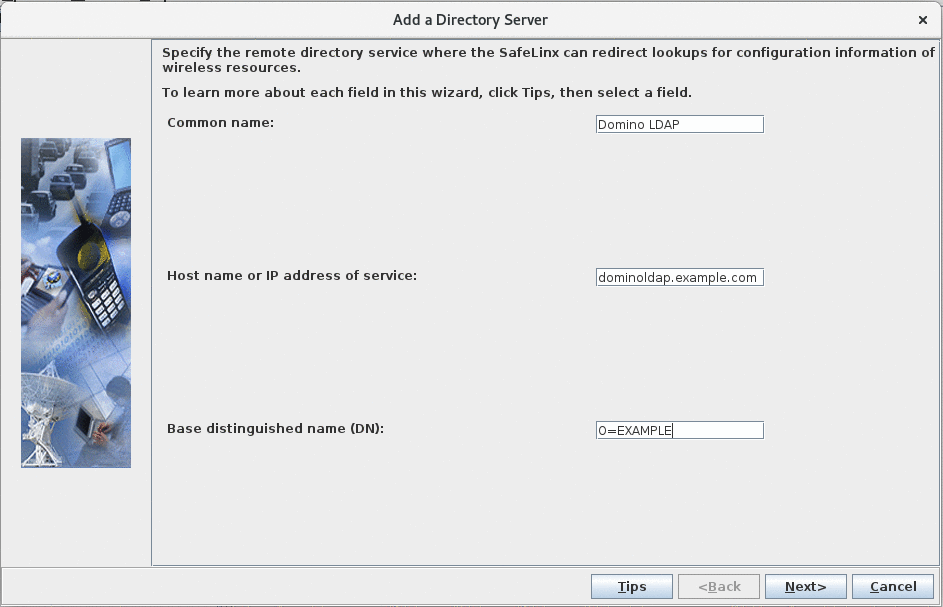
Specify directory servers:
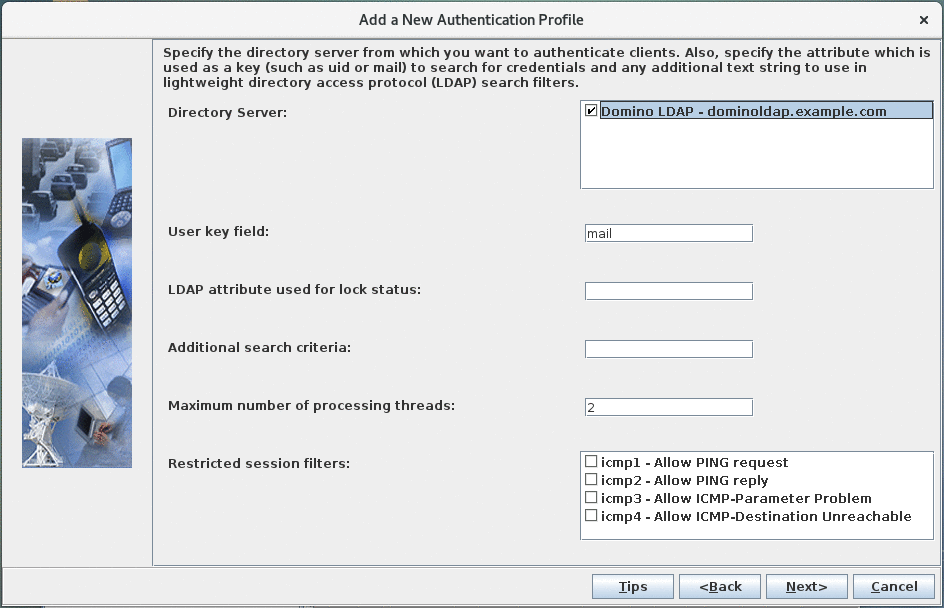
Select the "Domino LDAP" entry defined in the previous step as the "Directory Server', leave all other fields to their default value. -
LTPA configuration:
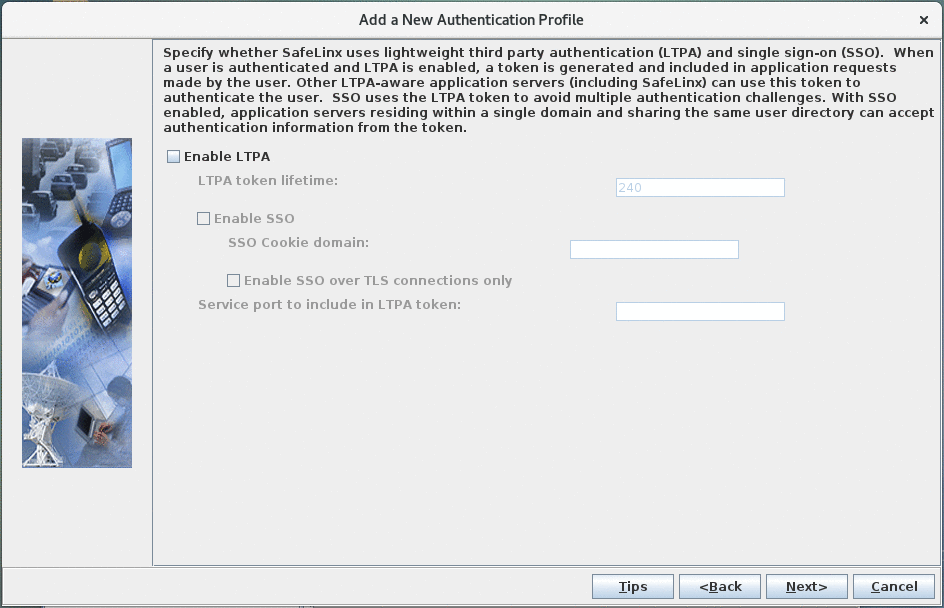
Leave the LTPA configuration disabled. -
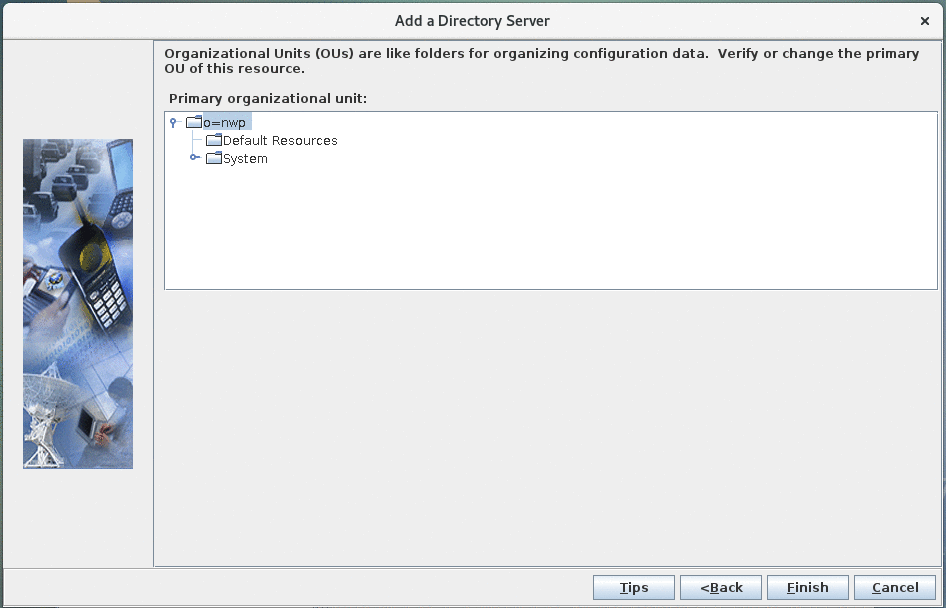
OU verification: