System architecture
This topic describes the system architecture for HCL Nomad for web browsers, iOS, and Android.
Web
HCL Nomad for web browsers consists of multiple components, including HTML, JS, WASM, NTF, NSF and INI files. These static files must be served by an HTTP server via HTTPS.
HCL Nomad for web browsers communicates with the HCL Domino servers via NRPC, but the only communication technically allowed from a WebAssembly container is secure WebSocket Secure (WSS). For security reasons, the WSS communication must be to the same site as the HTTPS communication. Therefore, HCL Nomad for web browsers tunnels NRPC over WSS to a Nomad server (either Nomad server on Domino or HCL SafeLinx server configured as a Nomad server) to handle both HTTPS and WSS communications.
For the NRPC traffic, HCL Nomad for web browsers wraps the NRPC request in WSS and sends the request to the Nomad server starting out as HTTPS (on port 443 by default) and using an HTTP 101 response code to upgrade the protocol to WebSockets. The Nomad server unwraps the received WSS to obtain the NRPC, identifies the target HCL Domino server, and relays the NRPC to the Domino server (on port 1352 by default). When the Nomad server receives the NRPC response, it wraps the NRPC in WSS and returns the NRPC wrapped in WSS to HCL Nomad for web browsers.
Because HCL Nomad for web browsers and Domino servers are communicating via NRPC at the end points, Domino clustering and failover functions as it does in other NRPC based clients.
In the browser, the code is all running inside a JavaScript engine. The static resources are cached locally and HCL Nomad uses an IndexedDB or Origin Private File System for local storage as needed.
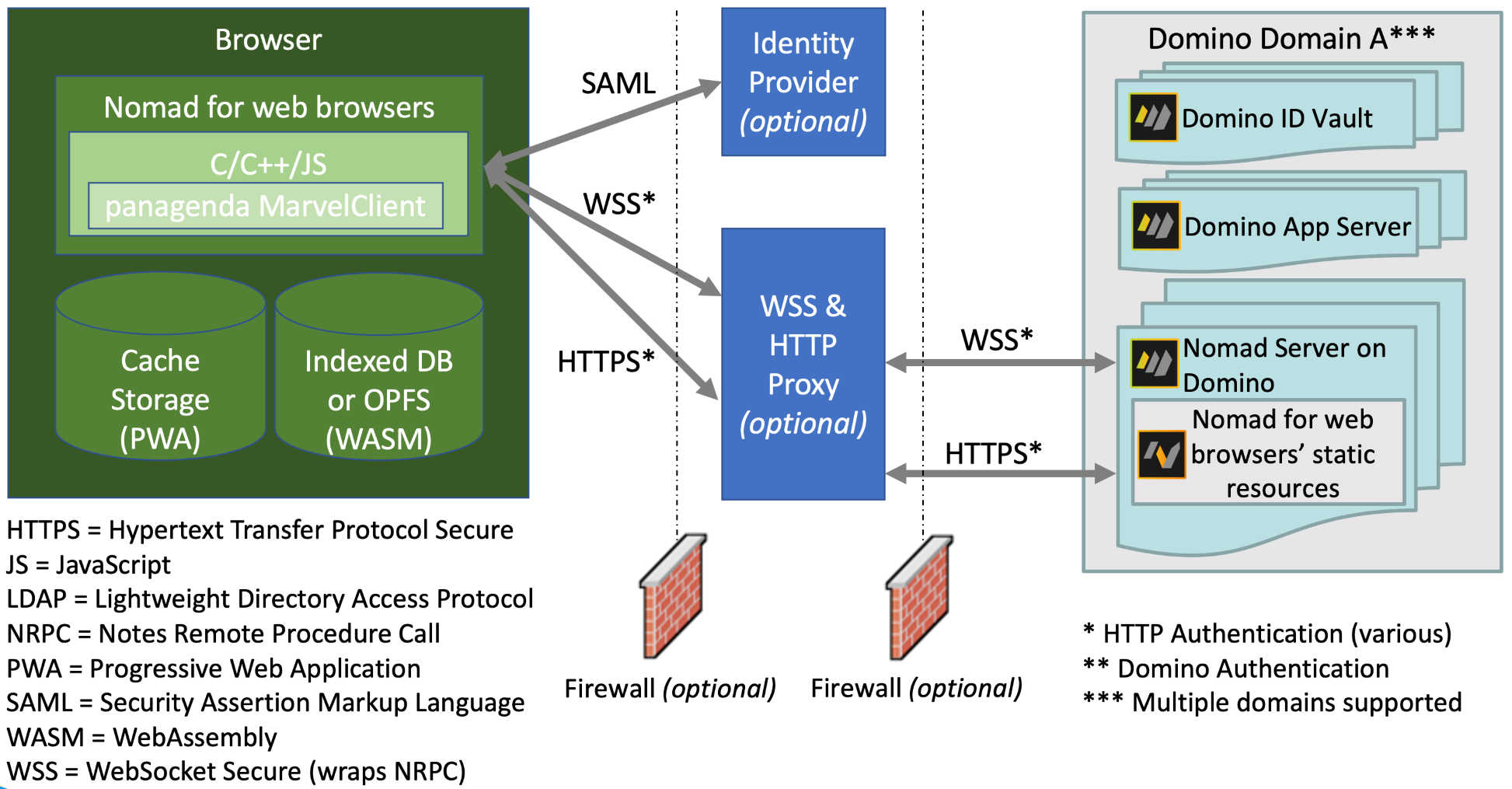
Nomad server on Domino
Static files served over HTTPS are always served locally by the Nomad server on Domino.
Because the Nomad server is running on Domino, the information for Nomad to be configured can be found with local lookups and LDAP calls to Domino are not necessary.
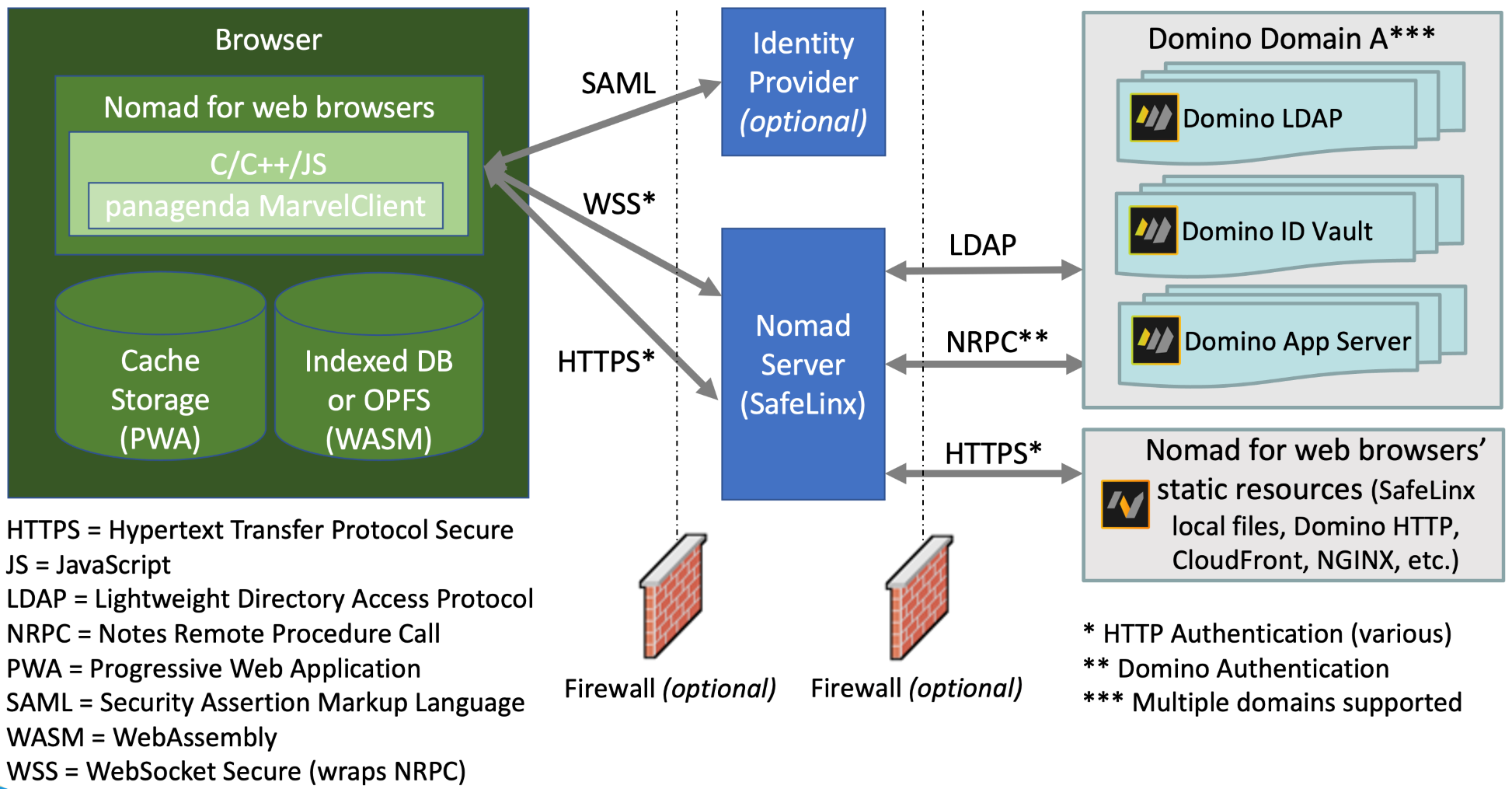
SafeLinx as the Nomad server
Static files served over HTTPS can be served locally by the Nomad server or hosted on a number of HTTP servers (Domino, CloudFront, NGINX, CDN, etc.).
SafeLinx uses LDAP calls to Domino to retrieve information necessary for Nomad to be configured (user name, server name, etc.).
Mobile
- For mobile, the client is a native application on the device and is not related to the browser.
- The NRPC communications are not restricted to WSS, so the mobile client may use either NRPC directly to the Domino servers (often requiring a VPN or other access to the Domino servers) or NRPC wrapped in WSS through the Nomad server to the Domino servers.
- The "Nomad for web browsers' static files" are not applicable to mobile.
- SAML is supported on mobile for authentication but not for Nomad Federated Login.