IAM roles support
With version 10.0.4, BigFix has introduced the support of IAM roles to simplify the management of AWS credentials.
In fact, BigFix can discover cloud instances based on what provider specific credentials are entitled to see or manage. This means that potentially a very large number of credentials need to be specified in the Plugin settings, with the related burden of keeping them current. Having the possibility to also use roles, this number significantly decreases since BigFix will start discovering by impersonating those roles and as such avoiding the need for multiple credentials to be managed since the discovery will be based on roles.
Of course in this case, the AWS cloud needs to be configured so that some users are given multiple roles to be able to discover the entire cloud environment. The roles must be provided to BigFix in their fully qualified name, called ARN (Amazon Resource Name). These information are usually exchanged between the Cloud administrator and the BigFix MO.
For AWS, here is how the user can specify the roles while installing the plugin or when adding / editing credentials:
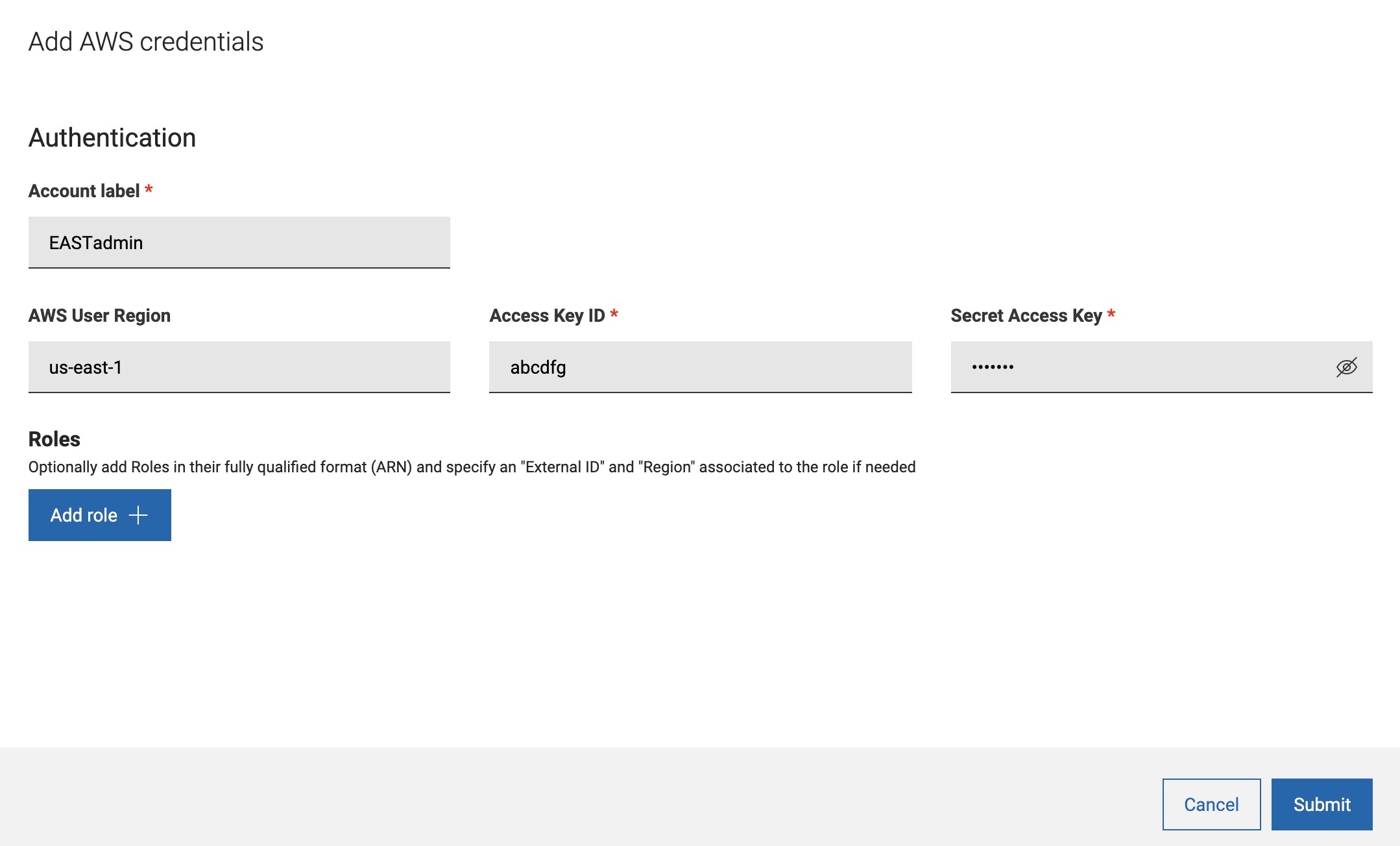
By pressing Add role, a table is displayed to include the fully qualified ARN for the role, an External ID if provided by the cloud administrator and a default region, required by the AWS APIs, to start the discovery. All of these fields are optional but if External ID or Region is specified, they must have an ARN.
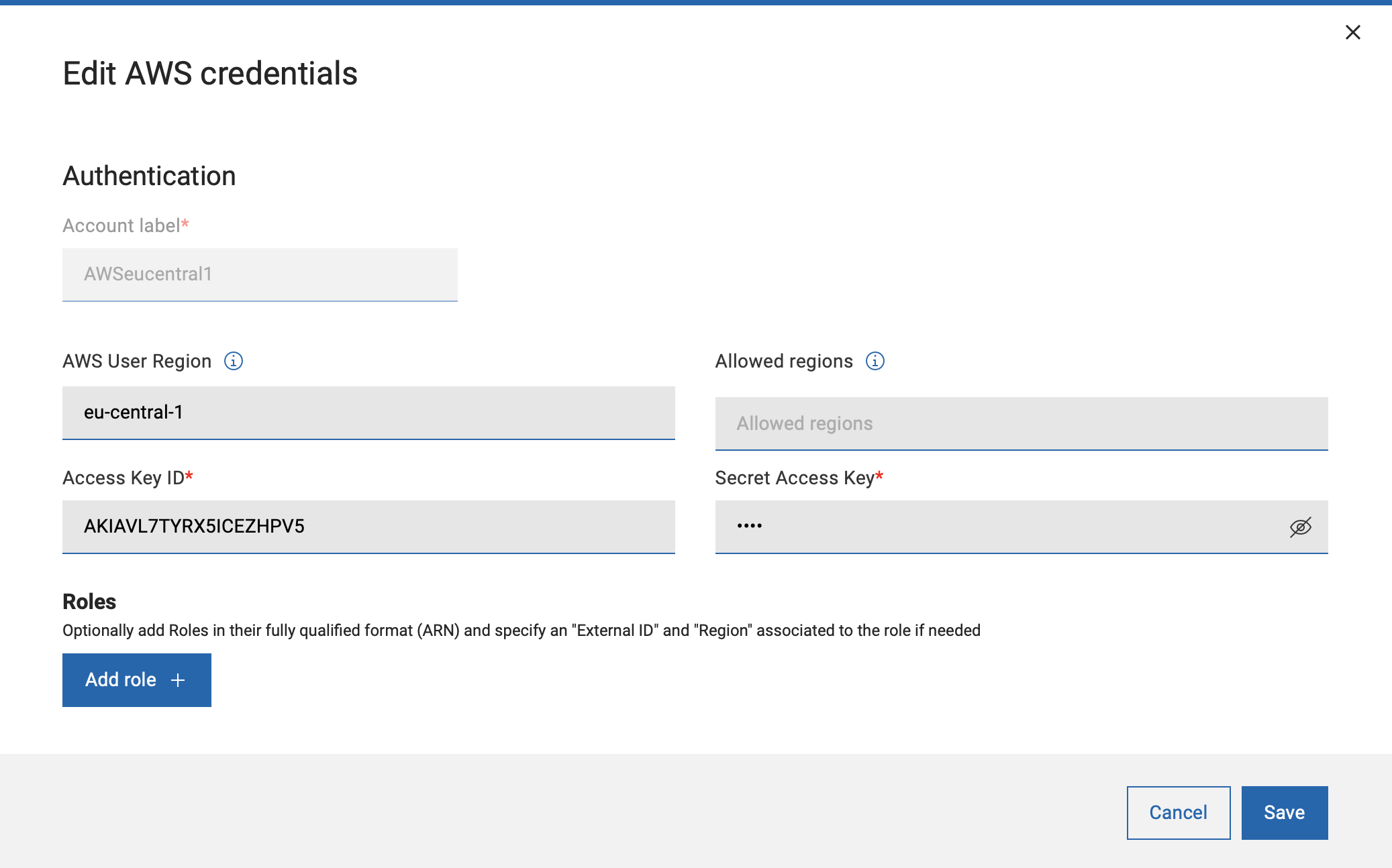
With BigFix Platform version 10.0.5, user can also limit scan at credential level.
Once the plugins are installed, the main Plugin Management page can be used to keep under control the plugins behavior.
Each provider has a dedicated horizontal tab, and once in the tab the sidebar on the left will have one entry per plugin, if in your environment there are multiple portals, therefore multiple plugins. In fact, there can be only one plugin of a specific provider installed on each portal.
The icon next to the plugin name is a quick indicator whether the plugin is working properly or not. In case there is a yellow or red icon, go to the Authentication table to spot the credential set that is causing troubles.
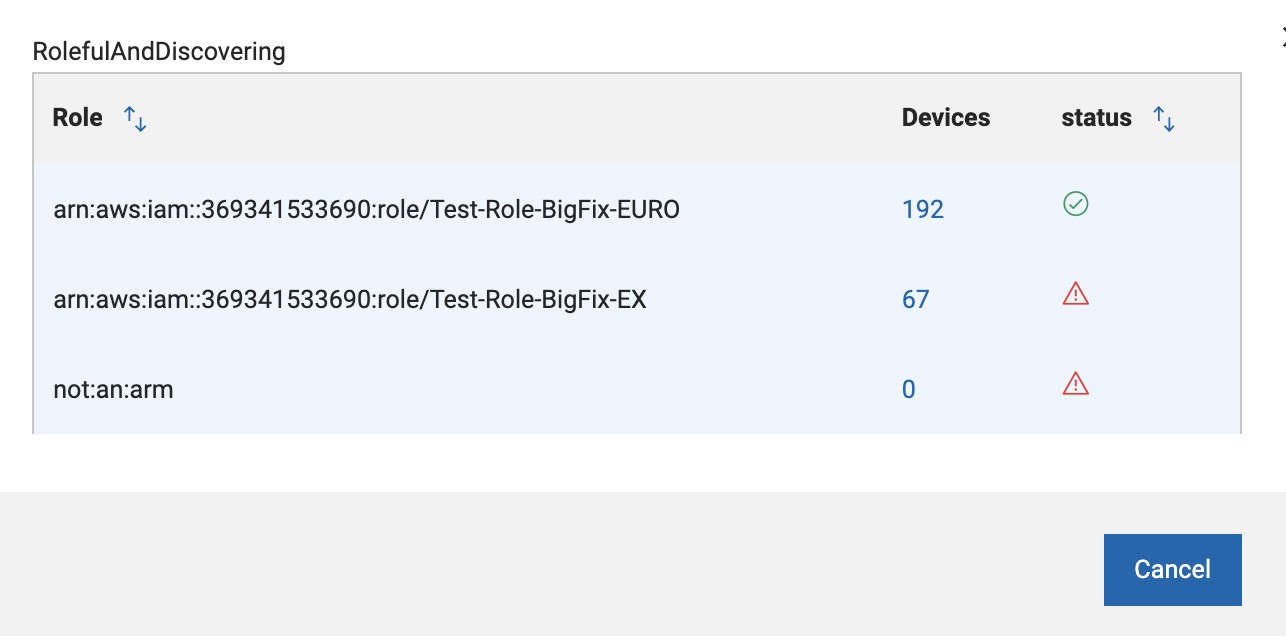
The table includes the credential information, the roles if specified, the status, number of devices discovered using the credentials, possibility to edit and to remove.
The “eye” icon opens a modal window with details on the roles.
- Last time a discovery was performed.
- The plugin version plus possibility to upgrade if a new version is available.
- Possibility to uninstall the Plugin.
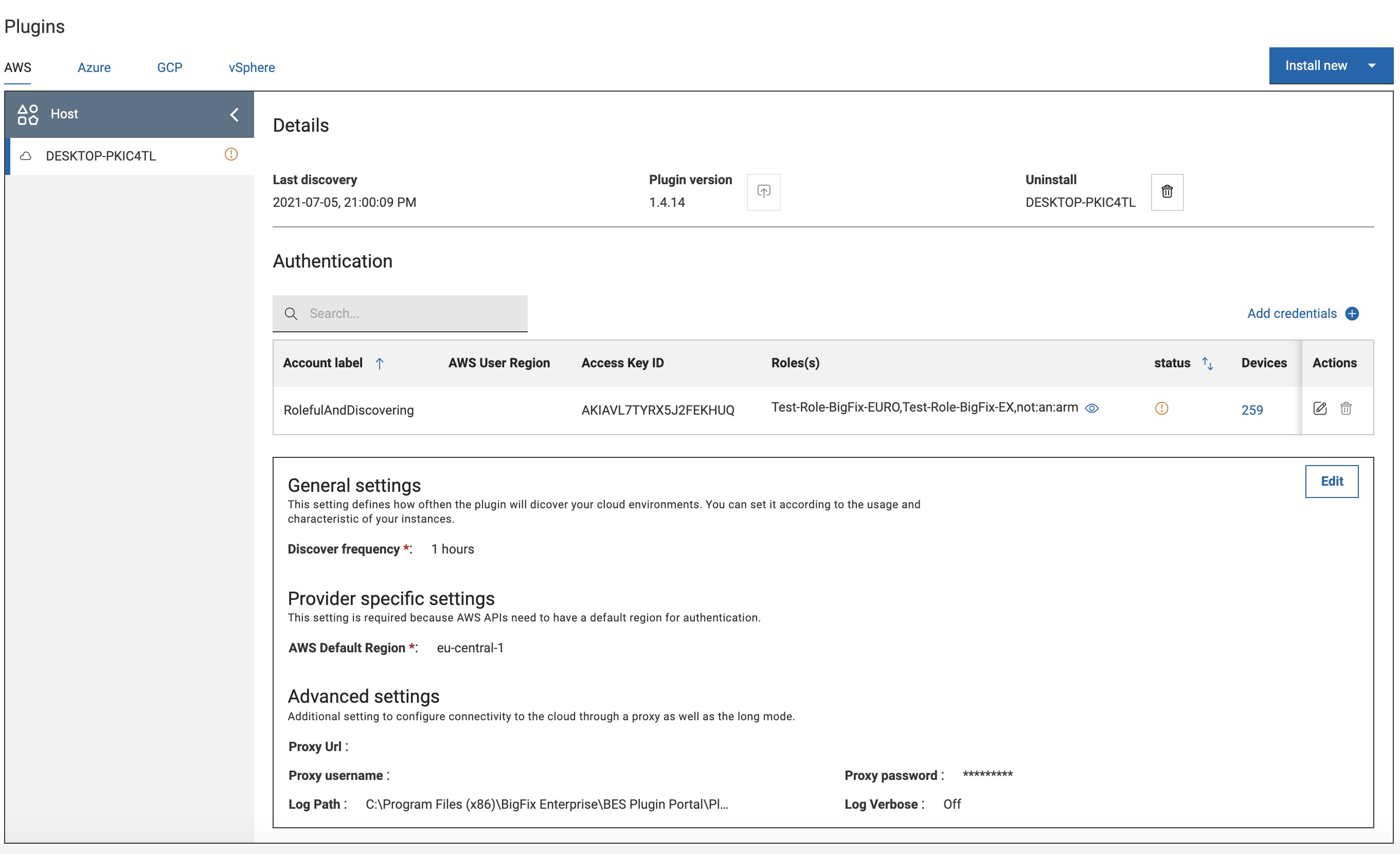
After the initial installation, more credentials can be added or existing credentials can be edited or removed. In the General settings section, provider specific information such as discovery frequency, logging and proxy can be set.