The WebUI Permissions Service
Use the WebUI Permissions service to control the amount of content operators can deploy, and the number of devices they can deploy to or query, at one time.
You can also use the Permissions service to grant unlimited targeting permissions to a role. The service will provide increasingly fine-grained control over permissions and preferences in WebUI applications. You can also grant permissions to non-master operator roles to perform various actions in patch policies. Open the Permissions service from the Settings menu.
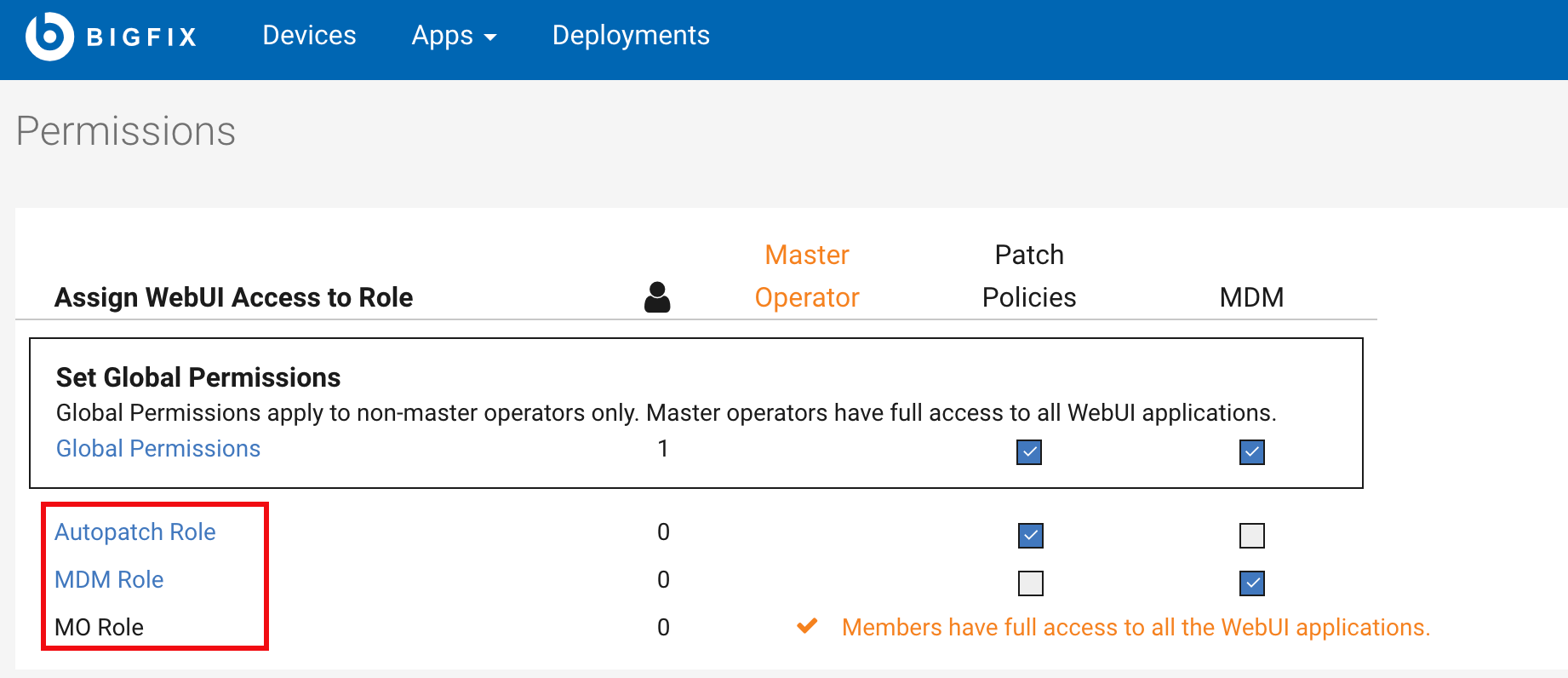
- When Patch Policies check box of Global Permissions is selected, the non-master operator roles will inherit the access to Patch Policies app from Global Permissions and master operator role will have full access to all WebUI applications by default.
- When Patch Policies check box of Global Permissions is not selected, the non-master operator roles will not have access to Patch Policies app and master operator role will have full access to all WebUI applications by default.
- When Patch Policies check box of Global Permissions is not selected, the non-master operator roles can still be granted access to Patch Policies app by selecting the patch policies check boxes of the roles manually, and master operator role will have full access to all WebUI applications by default.
Click Global Permissions to edit global target maximums and global patch policies permissions. In the Deployments tab, the administrator can set the content target limit and device limit for all non-master operators. Non-master operators cannot exceed the established limits. In case of violations, their deployment and query activities will be suspended until they fall within the acceptable range. Global target maximums apply to all non-master operators except the members of a role that has been granted unlimited target permissions. In the Patch Policies tab, the administrator can grant permissions which allow non-master operators to perform different actions.
- When Delete Policy permission is granted, non-master operators will also have permissions to Create/ Edit Policy, Delete Schedule, Create/ Edit Schedule, Add/ Remove Your Own Targets and Remove Other Operator's Targets.
- When Create/ Edit Policy permission is granted, non-master operators will also have permission to Refresh Policy.
- When Delete Schedule permission is granted, non-master operators will also have permissions to Create/ Edit Schedule, Add/ Remove Your Own Targets and Remove Other Operator's Targets.
- In the Deployments tab, administrator can set the content target limit and device limit for the selected role. Operators cannot exceed the established limits. In case of violations, their deployment and query activities are suspended until they fall within the acceptable range.
- In the Patch Policies tab, administrator can grant
permissions which allow specific role to perform different actions. Note: The Patch Policies tab is visible only if the selected role has permission to access the Patch Policies app.
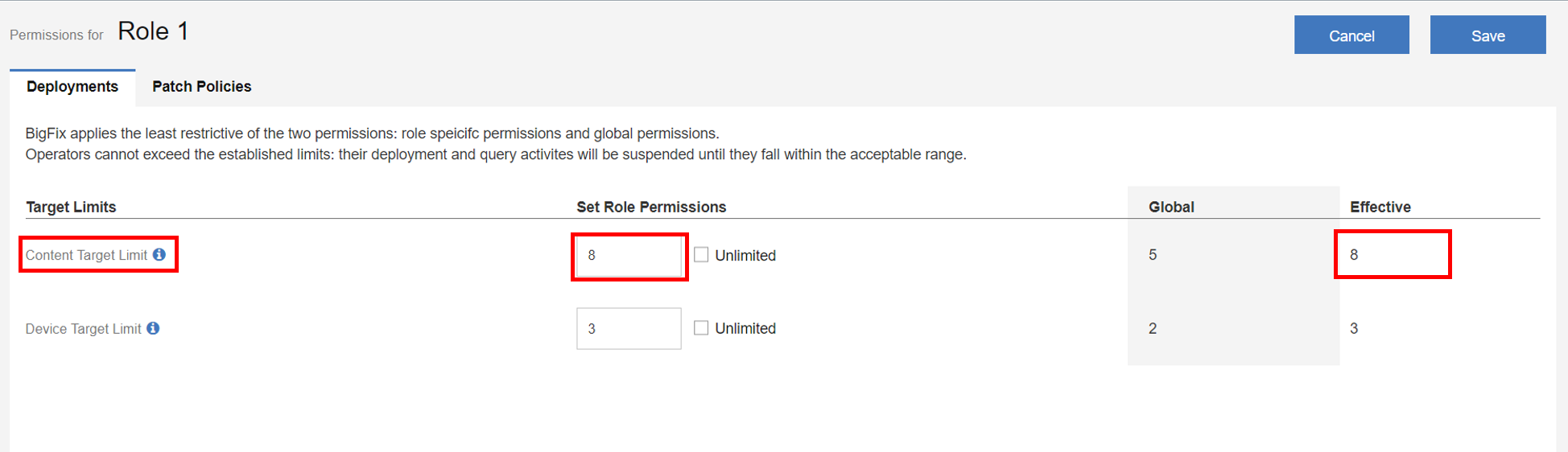
- Example: Content Target Limit
- The global permission is set to 5 and the role permission to 8 for Content Target Limit. The
least restrictive of the global permission and role permission is 8. The effective permission is set
to 8 as it is the least restrictive.
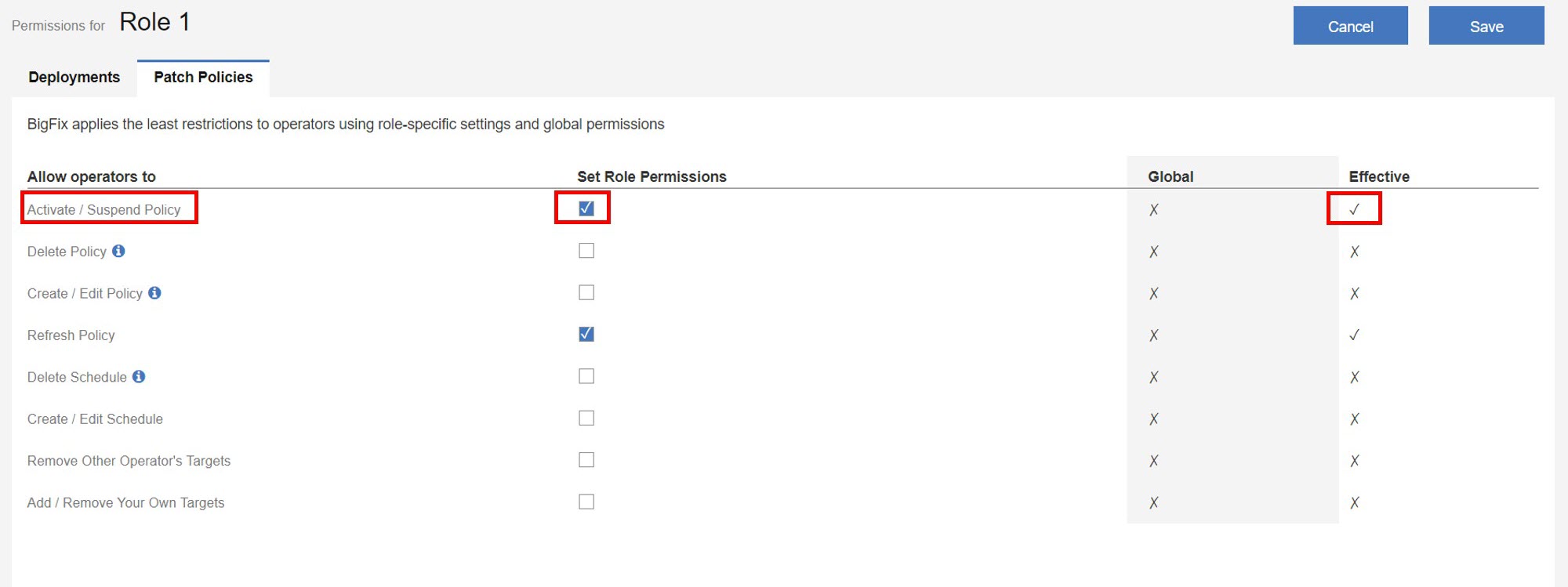
- Example: Patch Policies
- Activate/ Suspend Policy check box is not selected for global permission
and selected for role permission. The least restrictive of the global permission and role permission
in this case would be to allow operators in this role to Activate/ Suspend Policy.