Examples of hybrid analysis
Here are some examples of hybrid analysis.
In this report screen capture, both DAST and SAST discovered a Cross-Site Scripting vulnerability.
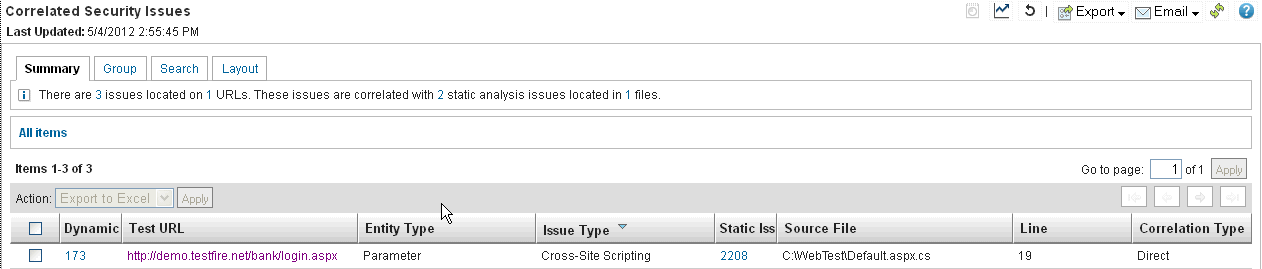
If we look at the About this Issue report for DAST, the issue was discovered in a parameter
'uid' by removing the ASP.NET_SessionID cookie and injecting
'1234"/>alert(1558)</script>' into the value of parameter 'uid'. Appscan
marked the test as vulnerable, because it has successfully embedded a script in the response, and it
will be executed once the page is loaded in the user's browser. This means the application is
vulnerable to Cross-Site Scripting on this URL: http://demo.testfire.net/bank/login.aspx.
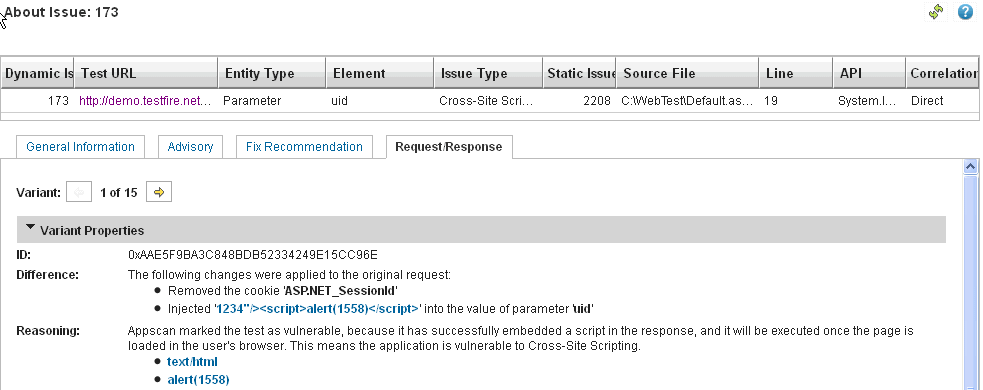
If we look at the About this Issue report for SAST, the code scan discovered the same vulnerability on C:\WebTest\Default.aspx.cs, the source code page for http://demo.testfire.net/bank/login.aspx.
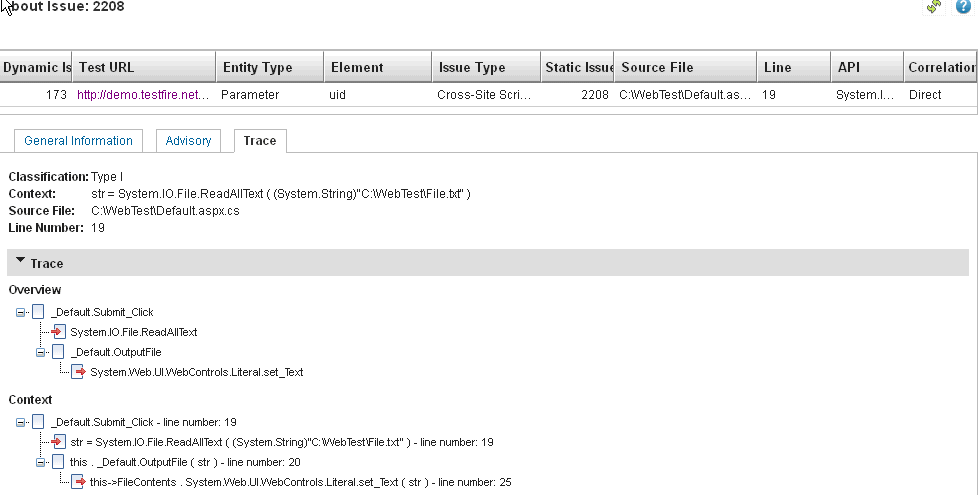
Because the URL, entity and issue type match, it is considered a direct correlation.
