How correlation (hybrid analysis) works
No single automated analysis technique can find all possible vulnerabilities; each technique has its own strengths and weaknesses. Dynamic Analysis Security Testing (DAST) tests a running web application by probing it in ways similar to what a hacker would use. Static Analysis Security Testing (SAST) examines the source code of an application for potential vulnerabilities.
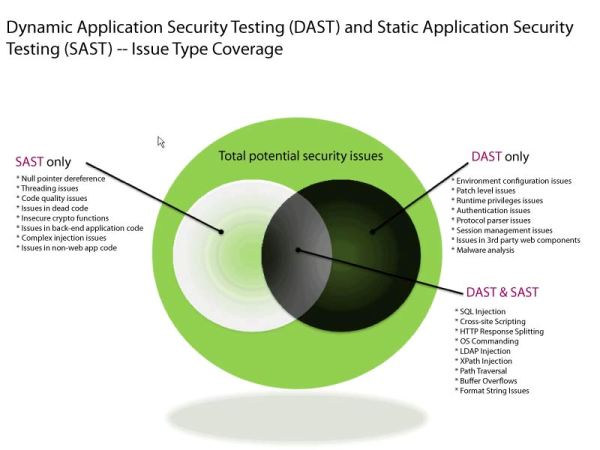
This diagram illustrates the types of vulnerabilities each technique can discover, and where they overlap for correlation purposes. The large green circle indicates the total potential security issues that could be found by DAST, SAST, and manual testing.
With dynamic analysis, it is easier to see the big picture, to connect the vulnerability with a potential exploit. DAST demonstrates the places within the application that are exploitable by the tests it sends; it automatically traverses the application and tests possible inputs by using HTTP tampering (sending requests and receiving responses reflected back in the browser). With dynamic analysis, however, the security analyst is always asking 'Did I get proper test coverage?' The challenge with DAST is to find all the pages and paths to content, and to cover all attack vectors.
Static analysis inspects data flows through the source code, and can be used earlier in the development cycle because you do not need a running web application. While DAST is limited to only seeing the data flow that is going over HTTP, SAST can see the multiple data flows that go on in the backend that are not exposed to dynamic analysis, such as backend network communications, file system access, etc. Therefore, SAST will find a lot more issues than DAST will, but not all of them will actually be a high priority to your organization, because SAST findings are normally interpreted as violations of secure coding best practices, not necessarily as 'proof of exploit'. Filtering removes issues that are not serious enough under the organization's security policy. The challenge with SAST is prioritizing issues.
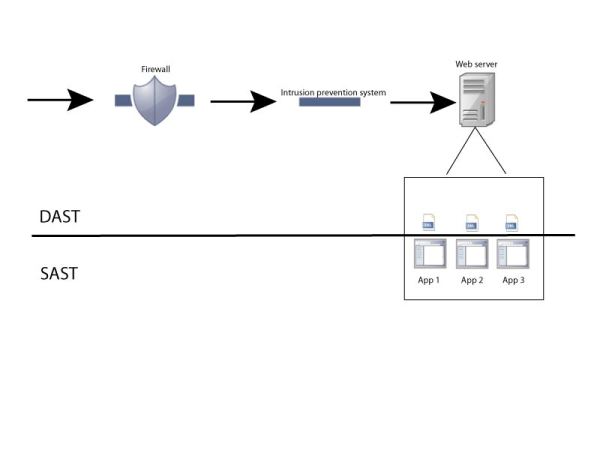
DAST looks through the network infrastructure down to the level of the web server. SAST only looks directly at the web applications.
The challenge of hybrid analysis
Hybrid Analysis (also called correlation) combines DAST and SAST to correlate and verify the results. Issues identified using dynamic analysis can be traced to the offending line of code. SAST issues can be automatically prioritized using DAST information.
The challenge with hybrid analysis is that DAST relies on data being reflected back in the browser, so if a SAST data flow is not reflected back in the browser as a DAST issue, it will not be appear in the Correlated Security Issues report of AppScan® Enterprise.
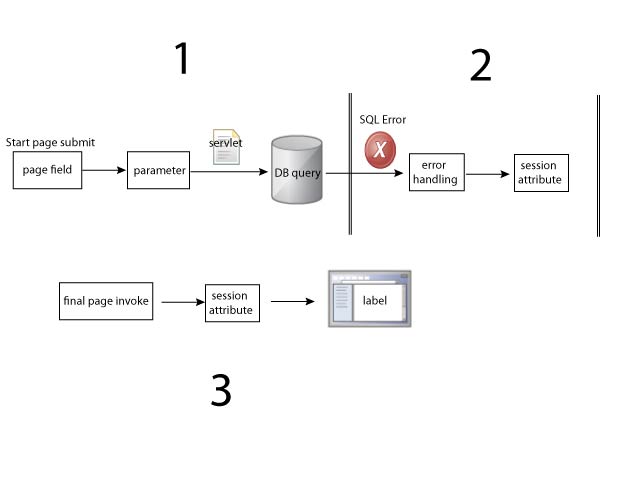
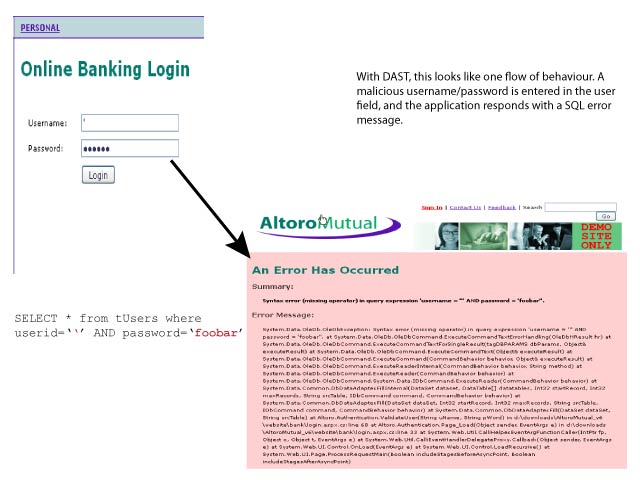
The following diagrams illustrate this challenge. This DAST diagram shows SQL injection as one data flow from the user perspective. Malicious code is entered into the user name/password fields in the web page, and an error message is displayed in the browser.
In this SAST diagram, the same SQL injection attack is actually three data flows from a back-end perspective.