Configure Behavior Monitoring Settings
About this task
Refer to the table in Event Monitoring for more information on the available policies.
Procedure
- Navigate to the Configuration > Behavior Monitoring Settings > Behavior
Monitoring Wizard screen.
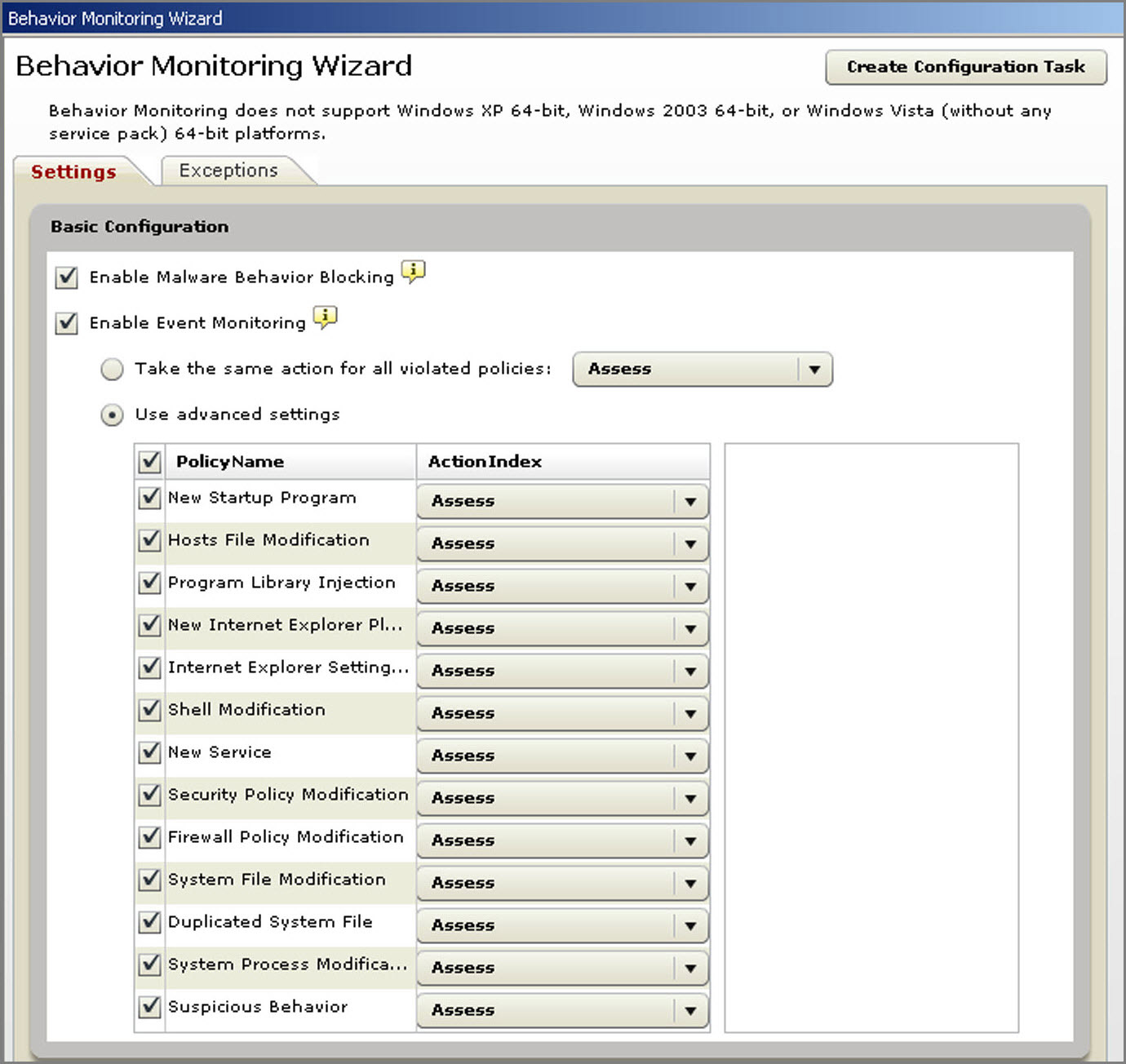
- Configure the settings as your network requires:
Note: CPM automatically enables Malware Behavior Blocking and disables Event Monitoring.
- Enable Malware Behavior Blocking: Select this option to enable program behavior monitoring for proactive detection of malware and similar threats.
- Enable
Event Monitoring: Select this option to monitor system
events that may introduce threats/security risks into the computer
and then select an action for each system event:Note: Trend Micro recommends enabling Core Protection Module - Enable Certified Safe Software Service to reduce the likelihood of false positive detections. See Enabling Certified Safe Software Service.
- Assess: Always allow processes associated with an event but record this action in the logs for assessment.
- Allow: Always allow processes associated with an event.
- Ask When Necessary: Prompts users to allow
or deny processes that may have violated Behavior Monitoring policies.Note: A prompt asking users to allow or deny the process and add to the Allowed Programs or Blocked Programs appears. If the user does not respond within the time period specified in the Behavior Monitoring Wizard screen, CPM automatically allows the process to continue.
- Deny: Always block processes associated with an event and record this action in the logs.
- Monitor newly encountered programs downloaded through
HTTP or email applications (Server platforms excluded):
Behavior Monitoring works in conjunction with Web Reputation Services
to verify the prevalence of files downloaded through HTTP and HTTPS
channels or email applications. After detecting a "newly encountered"
file, administrators can choose to prompt users before executing the
file. Trend Micro classifies a program as newly encountered based
on the number of file detections or historical age of the file as
determined by the Smart Protection Network.Select this option to scan the following file types for each channel:
- HTTP: Scans
.exefiles. - Email applications: Scans
.exe, and compressed.exefiles in unencrypted.zipand.rarfiles.
Notes:- Administrators must enable Web Reputation Services on the agent to allow CPM to scan HTTP traffic before this prompt can display.
- CPM matches the file names downloaded through email applications during the execution process. If the file name has been changed, the user does not receive a prompt.
- HTTP: Scans
- Automatically take action if the user does not respond within ___ seconds: This setting only works if Event Monitoring is enabled and the action for a monitored system event is "Ask when necessary". This action prompts a user to allow or deny programs associated with the event. If the user does not respond within a certain time period, CPM automatically allows the program to run. For details, see Event Monitoring.
