Environment data in Vault
Vault is supported for storing sensitive key-value pairs for Docker configuration. If you want to use this method of environment configuration, set CONFIGURE_MODE to Vault. With this setting, startup scripts fetch environment-related data from Vault when you start a Docker container.
You can have a Vault Tenant to represent your company (For example,
MyCompany), EnvironmentName (For example,
Non-production), and EnvironmentType (For example,
auth).
Storing key-value pairs in Vault
To set up Vault, see the Vault website. When you have a Vault ready for use, you can complete the following steps to store and retrieve key-value pairs.- Create a mount point based on the {Tenant}.For example,
init_json='json_data={"type":"generic","description":"description","config":{"max_lease_ttl":"876000"}}' header="X-Vault-Token:vaultToken"curl -X POST -H $header -H "Content-Type:application/json" -d '{"type":"generic","description":"description","config":{"max_lease_ttl":"876000"}}' http://vaultIP:vaultPort/v1/sys/mounts/tenant - Store key-value pair data by using the following
command.
For example, to store the value "mall" for a key name "dbName" under path MyCompany/Non-production/auth/dbName:curl -X POST -H "X-Vault-Token:vaultToken" -d '{"value":"value"}' http://vaultIP:vaultPort/v1/tenant/environmentName/enviromentType/targetKeycurl -X POST -H "X-Vault-Token:7f47efbb-b162-619b-0ced-448079d91b77" -d '{"value":"mall"}' http://myhostname.com:8200/v1/MyCompany/Non-production/auth/dbName
Retrieving key-value pairs in Vault
Retrieve key-value pair data by using the following command.curl -X GET -H "X-Vault-Token:vaultToken" http://VaultIP:VaultPort/v1/tenant/environmentName/enviromentType/targetKey | jq -r .data.valueKey-value data structure in Consul/Vault
The following tables list all of the default key-value paths on Consul/Vault.
The default EnvType values are auth and
live.
You can add your key-value paths based on your business requirements and define custom logic to fetch them.
| Vault path | Requirement | Description |
|---|---|---|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/domainName |
Optional | Specify the internal service domain name. If the deployed
environment is on a special namespace on Kubernetes, then the domain name should
be .svc.cluster.local. If no value is specified, then the
default, |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/externalDomainName |
Optional | This value specifies the store-web external
domain name, which can be recognized by your browser. For example, in the hostname store.demo4qaauth.hcl.com, hcl.com is the external domain name. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/kafkaServers |
Optional | Specify a value if you want to enable ZooKeeper and
Kafka. The format for this key-value pair
is: |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/kafkaTopicPrefix |
Optional | Specify a value if you want to config ZooKeeper and
Kafka. If no value is specified, the following default value is
applied.
|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/kafkaTopicPrefix |
Optional | The Kafka authentication user ID. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/kafkaTopicPrefix |
Optional | The Kafka authentication user password. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/zooKeeperServers Note: Deprecated and removed in HCL Commerce 9.1.12.0. Note: Deprecated and removed in HCL Commerce 9.1.12.0. |
Optional Removed in 9.1.12.0+ |
Specify a value if you want to enable ZooKeeper and
Kafka. The format for this key-value pair
is: |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/txnHost |
Optional | Specify a value if you want to set txnHost, instead of
using the default value. Note: This value is used for the
Transaction server Docker container only. The txHost value
is used for all other containers. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/txnPort |
Optional | Specify a value if you want to set txnPort, instead of
using the default value. Note: This value is used for the
Transaction server Docker container only. The txPort value
is used for all other containers. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/txHost |
Optional | Specify a value if you want to set txHost, instead of
using the default value. Note: This value is used for all
containers other than the Transaction server Docker container. To set the value
for the Transaction server Docker container, use the txnHost
value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/txPort |
Optional | Specify a value if you want to set txPort, instead of
using the default value. Note: This value is used for all
containers other than the Transaction server Docker container. To set the value
for the Transaction server Docker container, use the txnPort
value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/xcHost |
Optional | Specify a value if you want to set a host name for the Customization server, instead of using the default value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/xcPort |
Optional | Specify a value if you want to set a port number for the Customization server, instead of using the default value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/storeHost |
Optional | Specify a value if you want to set a value for the Store server Commerce Remote Store (CRS) store host, instead of
using the default value. The default value is the |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/storePort |
Optional | Specify a value if you want to set a value for the Store server Commerce Remote Store (CRS) store port, instead of
using the default value. The default value is |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/previewPort |
Specify a value if you want to set
previewPort, instead of using the default value. The
default value is |
|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/storeWebHost |
Optional | Specify a value if you want to set
storeWebHost, instead of using the default value. The default value is store.${TENANT}${ENVIRONMENT}${ENVTYPE}${EXTERNAL_DOMAIN_NAME}. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/storeWebPort |
Optional | Specify a value if you want to set
storeWebPort, instead of using the default value. The
default value is |
| Optional | Specify if you want to set the store access non-security port to NONSSLPort. | |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/searchPort |
Optional | Specify a value if you want to set searchPort, instead of using the default value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/searchScheme |
Optional | Specify a value if you want to set searchScheme, instead of using the default value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/searchMasterHost |
Optional | The Search server host name.
Note: This parameter is only required with the solr-based
search solution auth environment. The default value is the solr search master
service name. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/searchSlaveHost |
Optional | The Search server host name.
Note: This parameter is only required to be defined within
the live environment. The default value is the solr search slave service
name. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/searchRepeaterHost |
Optional | The Search server host name.
Note: This parameter is only required to be defined within
the live environment. The default value is the solr search repeater service
name. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/certs/CertName |
Optional | Specify third-party certificate
records.
|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/certsBundle |
Optional | Specify third-party certificate
records.
|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/spiUserPwd |
Mandatory | The ASCII encrypted spiuser user password. To set the password in your custom Docker containers, see Setting the spiuser password in your Docker images. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/adminSpiUserPwd |
Mandatory | The plain text spiuser user password. The ADMIN_SPIUSER_PWD must be the same value as SPIUSER_PWD but kept as plain text. To set the password in your custom Docker containers, see Setting the spiuser password in your Docker images. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/merchantKeyEncrypted |
Mandatory | The encrypted merchant key, encrypted with the key
encryption key. The merchant key was created when you or an administrator loaded
the HCL Commerce database schema. For more information, see: Important: You must specify your own merchant key and key
encryption key values for the security of your HCL Commerce installation. Do not
use the default values contained within the provided sample configuration files and
documentation examples. |
| Vault path | Requirement | Description |
|---|---|---|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbSSLEnable |
Optional | Specify whether the database connection uses SSL. Accepted
values are:
false.Note: You
can also specify datasource credentials through the start up command if you do
not want to retrieve the datasource values from Vault. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbHost |
Mandatory | The database host name for the environment. Note: This value is only mandatory in the auth environment for
WCPublishDataSource. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbName |
Mandatory | The database name. Note: This value is only
mandatory in the auth environment for
WCPublishDataSource. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbPort |
Mandatory | The database port number. Note: This value
is only mandatory in the auth environment for
WCPublishDataSource. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbUser |
Mandatory | The HCL Commerce database user name. Note: This value is only mandatory in the auth environment for
WCPublishDataSource. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbPassword |
Mandatory | The HCL Commerce database user password. Note: This value is only mandatory in the auth environment for
WCPublishDataSource. |
|
Mandatory | The encrypted HCL Commerce database user password. |
|
Mandatory | The database administrator user name. |
|
Mandatory | The encrypted database administrator user password. |
|
Optional | The database type. Accepted values are:
|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/dbSchema |
Optional | The database schema. |
| Vault path | Requirement | Description |
|---|---|---|
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/ts-app |
Optional | Specify a value if you want to enable Health
Center. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/search-app |
Optional | Specify a value if you want to enable Health
Center. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/xc-app |
Optional | Specify a value if you want to enable Health
Center. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/crs-app |
Optional | Specify a value if you want to enable Health
Center. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/search-query-app |
Optional | Specify a value if you want to enable Health Center. Accepted values
are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/healthCenterEnable/search-ingest-app |
Optional | Specify a value if you want to enable Health Center. Accepted values
are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/traceSpecification/ts-app |
Optional | If you want to change the trace specification for the Transaction server, specify a value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/traceSpecification/search-app |
Optional | If you want to change the trace specification for the Search server, specify a value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/traceSpecification/crs-app |
Optional | If you want to change the trace specification for the Store server, specify a value. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/traceSpecification/xc-app |
Optional | If you want to change the trace specification for the Customization server, specify a value. |
| Optional | ||
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/ts-app |
Optional | Specify a value if you want to enable Thread
Monitor. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/xc-app |
Optional | Specify a value if you want to enable Thread Monitor. Accepted values
are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/search-app |
Optional | Specify a value if you want to enable Thread
Monitor. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/crs-app |
Optional | Specify a value if you want to enable Thread
Monitor. Accepted values are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/search-ingest-app |
Optional | Specify a value if you want to enable Thread Monitor. Accepted values
are:
false. |
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/threadMonitorEnable/search-query-app |
Optional | Specify a value if you want to enable Thread Monitor. Accepted values
are:
false. |
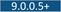 ${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/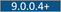 ${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/
${VAULT_URL}/${TENANT}/${ENVIRONMENT}/${ENVTYPE}/