Generating encrypted data with the wcs_encrypt utility
The wcs_encrypt utility encrypts sensitive information with an optional encryption key.
The optional key is usually the merchant key, but can also be the key encryption key when the merchant key itself needs to be encrypted (see example 4).The value of the merchant key is specified through command-line arguments or retrieved by calling out to the Key Locator Framework (KLF) by using the -k parameter. If the merchant key is not specified and the parameter -k is not used, the utility encrypts the sensitive data with an internal encryption key.
Syntax
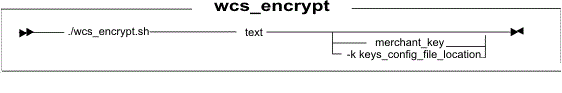
Parameter values
- text
- The character sequence to encrypt. Note: If the value for the text parameter includes special characters, such as '$', you must include the value within single quotation marks.
- merchant_key
- Optional: A plain text unencrypted merchant key. Specify this parameter if the merchant key is
not retrieved from the KLF.
- A 32 hexadecimal character must be used. Characters can be one of 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, a, b, c, d, e, or f.
- Must contain a minimum of one alphabetic character.
- Must contain a minimum of one numeric character.
- Must be in lowercase.
- Cannot contain more than 4 identical consecutive characters.
For example, 1a1a1a1a1a1a1a1a2b2b2b2b2b2b2b2b.
- -k keys_config_file_location
- Optional: Retrieve the merchant key from the KLF by using the specified key configuration file. Specify the absolute path of the file.
Example 1
Data, abc, needs to be encrypted by the merchant key, and then stored in the database. The merchant key is specified in plain text, without using the KLF:
wcs_encrypt.sh abc 1234567890abcdef1234567890abcdefExample 2
wcs_encrypt.sh abc -k C:\WebSphere\CommerceServer\instances\xml\CustomKeys.xmlExample 3
wcs_encrypt.sh myPasswordThe ASCII encrypted string should then be stored in the configuration file.
Example 4
When encrypting a merchant key for specifying it within Vault or within an external file (for example, merchantKey.xml), ensure that you encrypt it by using the key encryption key specified in the KLF (specified within KeyEncryptionKey.xml by default).
wcs_encrypt.sh 1a1a1a1a1a1a1a1a2b2b2b2b2b2b2b2b 3c3c3c3c3c3c3c3c4d4d4d4d4d4d4d4dThe ASCII encrypted string should then be stored in the external file, or in Vault.