AWS CloudFormation deployment of HCL Workload Automation
- Resources and HCL Workload Automation deployment
- This template deploys all the resources needed for the installation of HCL Workload Automation
charts, and the charts themselves. The resources that can be deployed through
this template are the following ones:
- Amazon RDS Oracle Database
- Ingress-Controller
- HCL Workload AutomationMetering Service Account
- Cert-Manager
- HCL Workload Automation Charts
-
- Pre-requisites
- You must satisfy the following pre-requisites to successfully deploy
this template:
- You must have the necessary permissions to create IAM roles on your account. If you do not have the necessary permissions, you must ask your administrator to create a role with the permissions to create IAM roles for you. Alternatively, an IAM Passrole with such permissions assigned can be passed to the template that is being run.
- Create three IAM Roles to be assigned, respectively, to the
AWSQS Third Party Extensions to be activated in the account.
The recommended policies to be assigned to such roles are
the following ones:
- KubernetesGetRole:
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "secretsmanager:GetSecretValue", "kms:Decrypt", "eks:DescribeCluster", "s3:GetObject", "sts:AssumeRole", "sts:GetCallerIdentity", "iam:PassRole", "ec2:CreateNetworkInterface", "ec2:DescribeNetworkInterfaces", "ec2:DeleteNetworkInterface", "ec2:DescribeVpcs", "ec2:DescribeSubnets", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents", "lambda:UpdateFunctionConfiguration", "lambda:DeleteFunction", "lambda:GetFunction", "lambda:InvokeFunction", "lambda:CreateFunction", "lambda:UpdateFunctionCode", "logs:CreateLogGroup", "logs:CreateLogStream", "logs:DescribeLogGroups", "logs:DescribeLogStreams", "logs:PutLogEvents", "cloudwatch:ListMetrics", "cloudwatch:PutMetricData", "ssm:PutParameter", "ssm:GetParameter", "ssm:DeleteParameter" ], "Resource": "*", "Effect": "Allow" } ] } - KubernetesHelmRole:
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "secretsmanager:GetSecretValue", "kms:Decrypt", "eks:DescribeCluster", "s3:GetObject", "sts:AssumeRole", "iam:PassRole", "ec2:CreateNetworkInterface", "ec2:DescribeNetworkInterfaces", "ec2:DeleteNetworkInterface", "ec2:DescribeVpcs", "ec2:DescribeSubnets", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents", "lambda:UpdateFunctionConfiguration", "lambda:DeleteFunction", "lambda:GetFunction", "lambda:InvokeFunction", "lambda:CreateFunction", "lambda:UpdateFunctionCode", "cloudformation:ListExports", "ecr:GetAuthorizationToken", "ecr:BatchCheckLayerAvailability", "ecr:GetDownloadUrlForLayer", "ecr:BatchGetImage" ], "Resource": "*", "Effect": "Allow" } ] } - KubernetesResourceRole
{ "Version": "2012-10-17", "Statement": [ { "Action": [ "secretsmanager:GetSecretValue", "kms:Decrypt", "eks:DescribeCluster", "s3:GetObject", "sts:AssumeRole", "iam:PassRole", "ec2:CreateNetworkInterface", "ec2:DescribeNetworkInterfaces", "ec2:DeleteNetworkInterface", "ec2:DescribeVpcs", "ec2:DescribeSubnets", "ec2:DescribeRouteTables", "ec2:DescribeSecurityGroups", "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents", "lambda:UpdateFunctionConfiguration", "lambda:DeleteFunction", "lambda:GetFunction", "lambda:InvokeFunction", "lambda:CreateFunction", "lambda:UpdateFunctionCode", "logs:CreateLogGroup", "logs:CreateLogStream", "logs:DescribeLogGroups", "logs:DescribeLogStreams", "logs:PutLogEvents", "cloudwatch:ListMetrics", "cloudwatch:PutMetricData" ], "Resource": "*", "Effect": "Allow" } ] }
- KubernetesGetRole:
- Activate the third party extensions on your account, through
the AWS CloudFormation service, and assign them their corresponding execution
roles. This can be done as follows:
- From the AWS Web user interface, reach the AWS CloudFormation service.
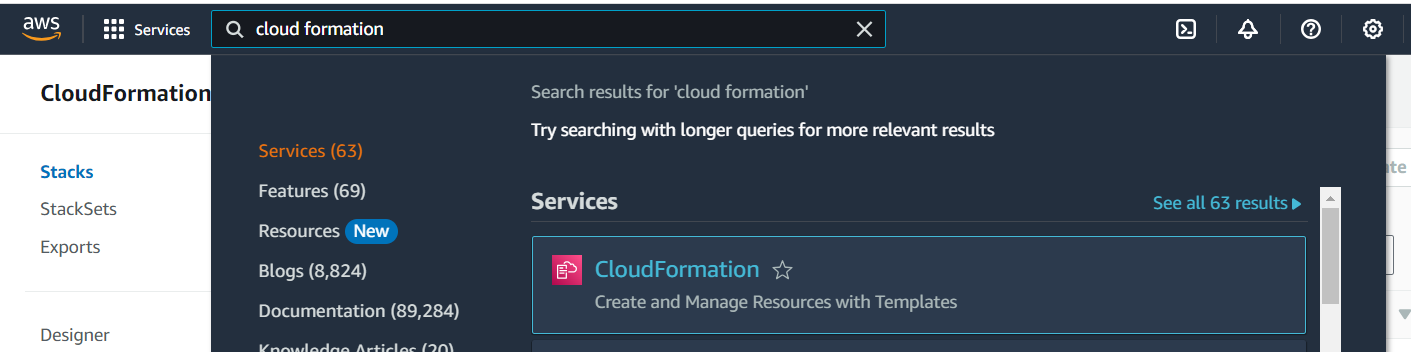
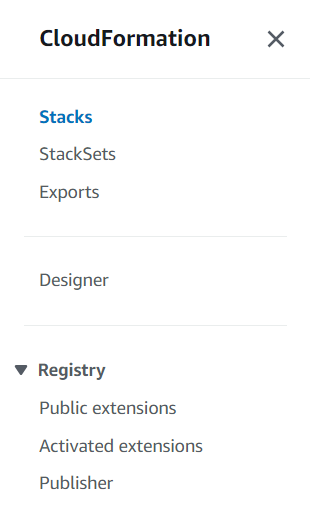
- On the left-side panel, go to
Registry/Public
extensions
- In the Filters panel, select
Third-party in the
Publisher section, and query
for AWSQS in the
Extensions search bar
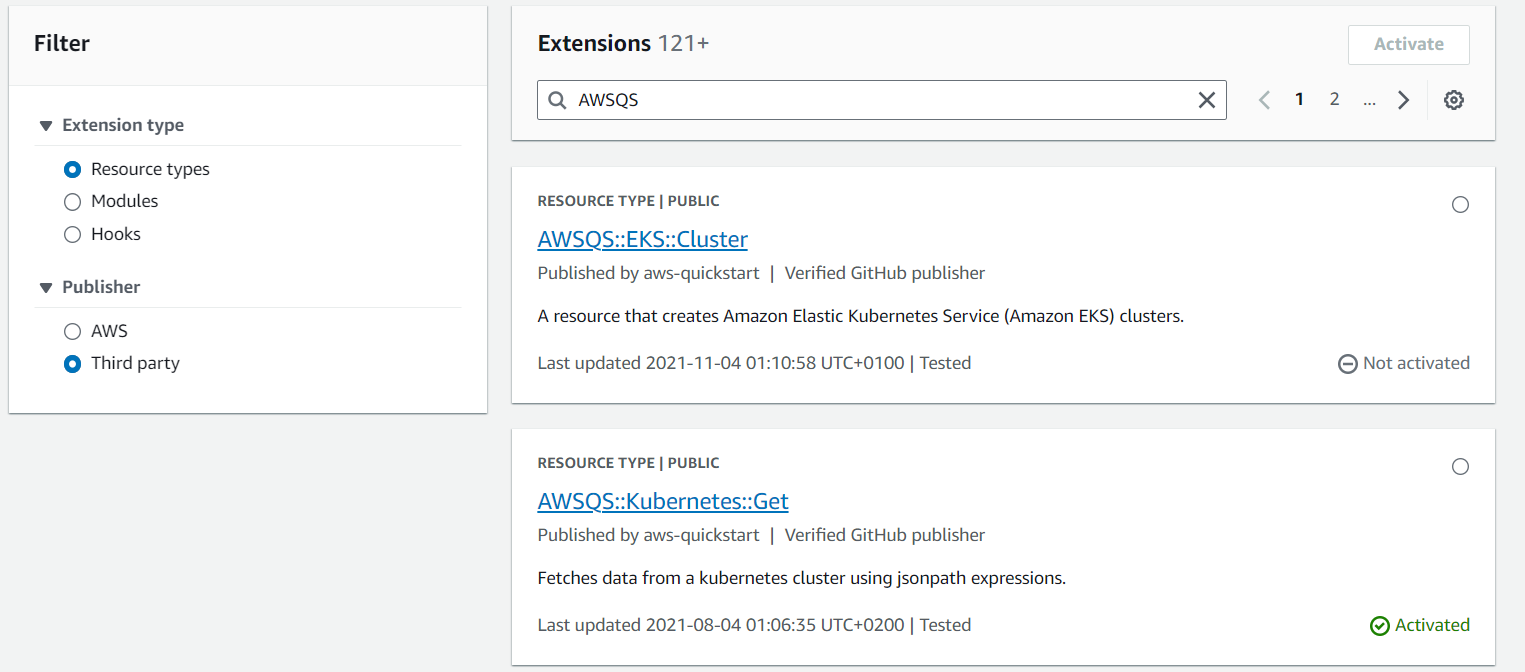
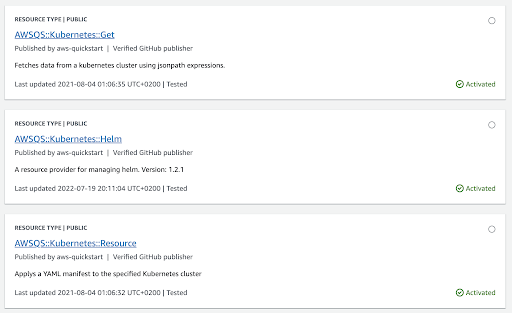
- The resources you need to active are:
- AWSQS::Kubernetes::Get
- AWSQS::Kubernetes::Resource
- AWSQS::Kubernetes::Helm
- Activate the resource
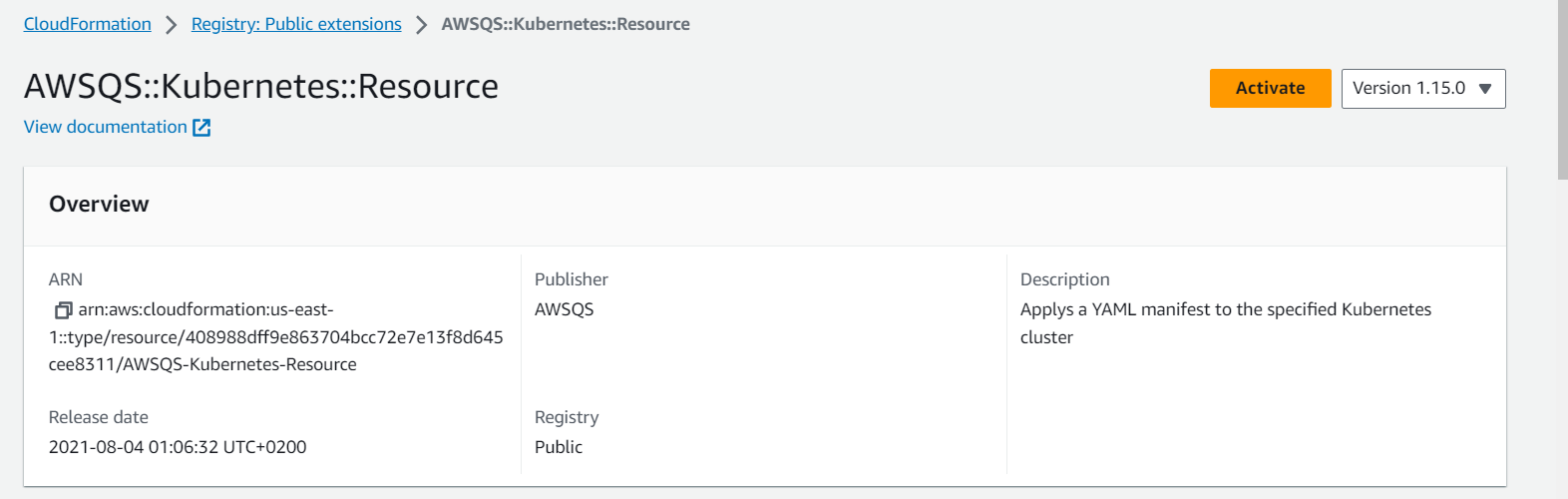
- Use the default name. Type the corresponding
Execution Role ARN created in
the previous steps. The ARN is presented in the
format
arn:aws:iam::<your_account_id>:role/role-name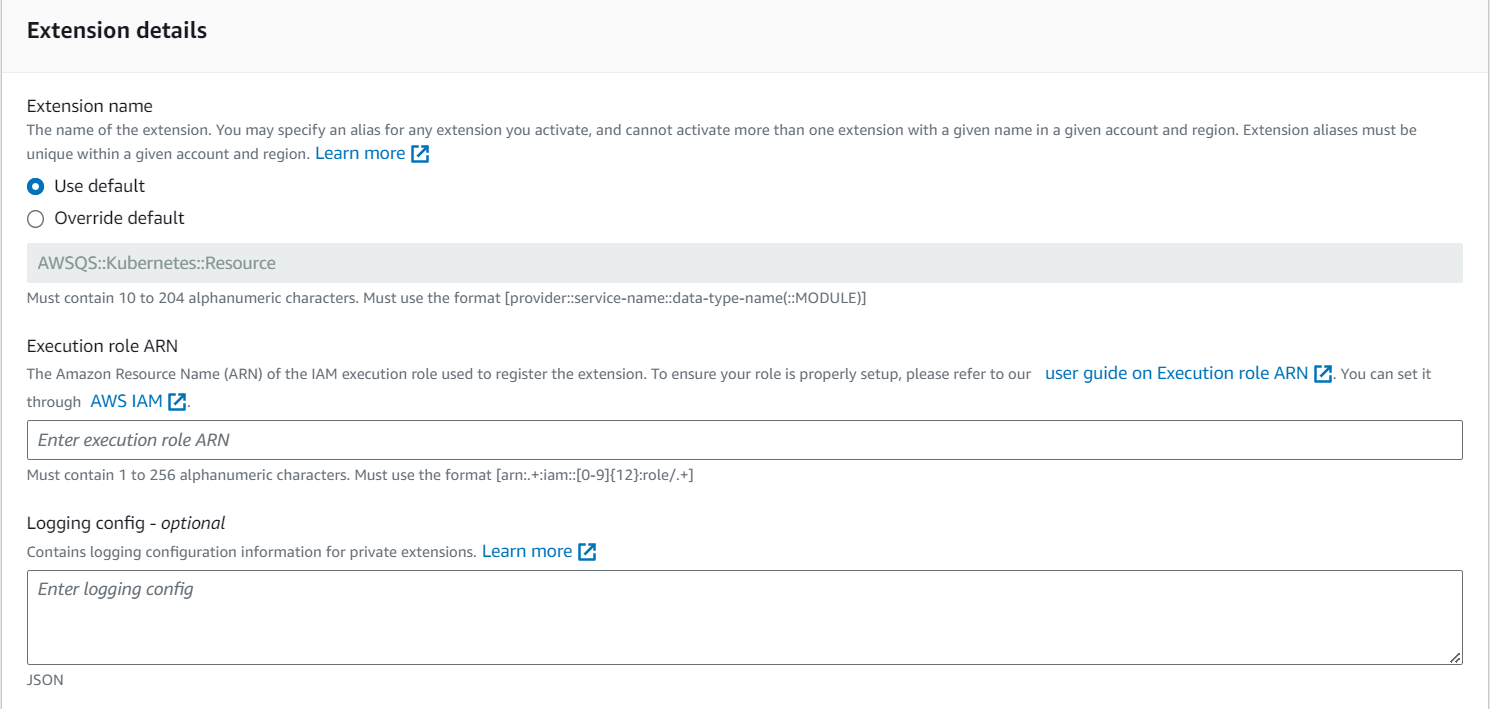
- Click Activate extension
- From the AWS Web user interface, reach the AWS CloudFormation service.
- Patch the aws-auth ConfigMap that has been created in
the target cluster where the resources and charts are
installed. The three roles for the extensions must be added
to this ConfigMap:
- Connect to your cluster. You can find the relevant information here
- Edit the ConfigMap through
kubectl:
kubectl edit configmap aws-auth -n kube-system - Add the execution roles for the AWSQS extensions in
the sysadmin group, in the
data.mapRoles
section:
data: mapRoles: | ... - groups: - system:masters rolearn: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-helm username: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-helm - groups: - system:masters rolearn: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-get username: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-get - groups: - system:masters rolearn: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-resource username: arn:aws:iam::<your_account_id>:role/awsqs-kubernetes-resource
- You must create a security group to create the Amazon RDS Oracle Database: the ARN of this resource is provided as input in the second template. The security group must allow incoming connections for Oracle DB (tcp port 1521) and outgoing connections.