Setting up internet relays
You can configure your relays to manage clients that are only connected to the Internet without using VPN as if they were within the corporate network.
Using this approach, you can manage computers that are outside the corporate network (at home, in airports, at coffee shops, and so on.) using BigFix to:
- Report their updated properties and Fixlet status.
- Enforce new security policies defined by a Console operator.
- Accept new patch or application deployments.
This configuration is especially useful for managing mobile devices that might often be disconnected from the corporate network. The following picture shows a typical Internet-based relay, as it might exist in a DMZ network:
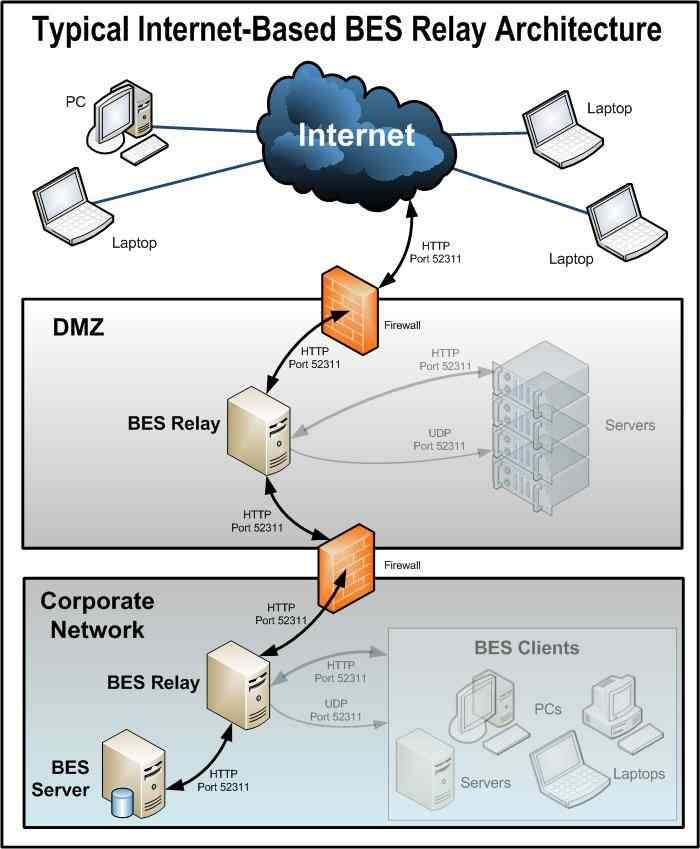
Setting up an Internet-facing relay enables external clients to find and connect to a relay. In our picture the clients can select the following types of relay:
- Manual Relay Selection: Clients can be configured using the console to manually select the Internet-facing relay DNS-alias (or IP address) as their primary, secondary, or failover relay. For more details about the failover relay setting, see Registration.
- Automatic Relay Selection: If ICMP traffic has been allowed from the Internet to a
DMZ-based Internet relay, then automatic relay selection can be leveraged to allow
clients to find the closest relay as they move from location to location (either
within a corporate network or on the Internet). For external clients on the
Internet, the only relay they are able to find and connect to is the Internet-facing
relay (because ICMP traffic from the Internet would be blocked to the relays within
the corporate network).Note: You can use the feature relay Affiliation to configure clients to find the most appropriate relay. For more details, see Relay affiliation and https://bigfix-wiki.hcltechsw.com/wikis/home?lang=en-us#!/wiki/BigFix%20Wiki/page/Relay%20Affiliation.
This is how the relays, clients, and firewalls are configured in a typical internet-based BigFix relay architecture:
- A relay is deployed in a DMZ and the internal DMZ firewall allows only BigFix traffic (HTTP Port 52311) between the DMZ relay and a designated relay within the corporate network. The design above suggests bidirectional traffic as opposed to only allowing the Internet-facing relay to initiate network connections to the relay within the internal corporate network. This enables quicker client response times because immediate notifications of new content are made to the Internet-facing relay thus maintaining a real-time synchronization of content. If the bidirectional communication between the Internet-facing BigFix relay and the relay in the corporate network is not allowed, the Internet-facing relay must be configured to periodically poll its parent (the relay within the corporate network) for new content. For more details about configuring command polling, see Command polling .
- BigFix deployments that include
internet-facing relays that are not configured as
authenticating
are prone to security threats. Security threats in this context might mean unauthorized access to the relays and any content or actions, and download packages associated with them or to the Relay Diagnostics page that might contain sensitive information (for example: software, vulnerability information, and passwords). When a relay is configured as authenticating, only the BigFix clients in your environment can connect to it and all the communication between them happens through TLS (HTTPS). This configuration also prevents any unauthorized access to the Relay and Server diagnostics page.For instructions on how to set the internet-facing relays as authenticating, see Authenticating relays.
- After relay communication is established between the DMZ and the internal corporate network, the external firewall also has to be opened to allow Internet-based client traffic (HTTP port 52311) to reach the DMZ relay. In addition, allowing ICMP traffic through the external firewall to the Internet-facing relay can aid in the external client auto-relay selection process.
- A DNS-alias (or IP address) is assigned to the relay that enables external clients to find the DMZ-based Internet relay. The DNS-alias must be resolvable to a specific IP address.
- To make the relay aware of the DNS-alias (or IP address) deploy the BES Relay Setting: Name Override Fixlet to the DMZ-based Internet relay.
- Disable the relay diagnostics for Internet relays (by configuring
_BESRelay_Diagnostics_Enable) or password-protect the page (by configuring_BESRelay_Diagnostics_Password). For details about the configuration settings, see Relay diagnostics.For more information about relay diagnostics, see Relay and Server diagnostics.
- With the entire BigFix communication path established from the Internet through the DMZ-based Internet relay and ultimately to the main server, the next step depends on the various relay selection methods available in a given BigFix infrastructure.
- Dynamic Policy Settings can be applied to Internet-based clients to allow for configurations better suited to external agents. For example, because the normal notification method (a UDP ping on port 52311) for new content might not reach external clients, dynamic settings can be used to have clients check for new content more frequently than the default period of 24 hours. For more information on setting up command-polling, see Changing the gather interval for a BigFix Client via the command polling client settings.