Governing Logic
There are several sets of logic that affect policy targeting. When creating and deploying a firewall policy, the chronological order is:
Create a policy.
Add it to a task.
Deploy it.
The endpoint, which makes the final determination of relevance, is more-or-less autonomous.
Irrespective of this chronology, however, is the determination of applicability. Whether or not a given policy is in fact applied to a given endpoint is determined by the population of endpoints that remains after configuring the Task and Action. This is important because it means that simply including an IP address in a firewall policy does not mean that the IP address will receive the policy.
The list below shows the order of inheritance. The Task defines the population within which the Action can occur, and the Action defines the population within which IP addresses defined in the policy can occur. The Policy sets the population of IP addresses available for the Task. Knowing exactly which endpoints will ultimately receive your policy can be complex.
To determine which endpoints receive a policy depends on:
The Policy List: Only one policy will ever be in effect for a given client at a given time. The policy in effect is the first policy on the policy list that contains the IP address of a targeted endpoint. This condition makes the order of policies in the Policy List significant. Evaluation occurs from the top down and stops once a policy has been found that applies to an endpoint IP addresses. Always put policies that specify fewer than "All Possible IPs" above those that specify all IP addresses, which is, typically, most if not all policies). If you do not, the policy that includes specific IP addresses will never be applied.
Figure 1: Firewall Policy Settings Wizard Screen 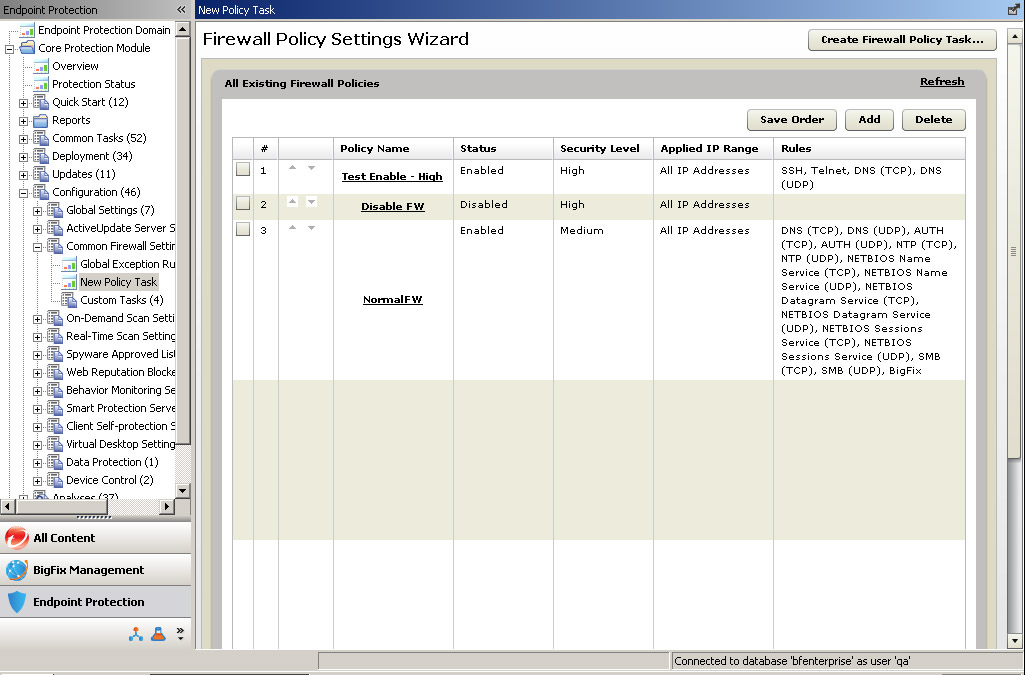
The Policy: Within a firewall policy, include all possible IP addresses or a range of IP addresses. Policy IP addresses will always be limited to the population of IP addresses defined in the Task that deploys it.
The Task: You can make the Task relevant to all or certain computers. By default, tasks created for a firewall policy will use a relevance statement that is made up of conditions from the firewall policy.
The Action: When you deploy a Task, you select your targets from the population of endpoints made available in the Task. You can reduce the population of endpoints to those that you want the policy to target, and the conditions under which you want the policy to apply. For example, you can filter the possible endpoints by selecting a different target, by defining user eligibility, or by setting execution or offer conditions.
The Endpoint: The agent installed on the endpoint keeps a detailed list of computer-specific parameters against which it continuously evaluates the relevance statements of all Tasks deployed to it. If the endpoint finds that it is not relevant, it will not incorporate the policy. This is significant when you deploy multiple firewall policies to co-exist on the same endpoint as opposed to one policy replacing another. The endpoint selects which policy to apply based on its current status, for example, the IP address it is currently using to connect to the network.
