Exception Rules Configuration
Add a custom exception rule to the firewall policy by clicking the Add button. Click an existing exception rule to open the rule for editing. The options are explained below.
Name: The name you type here will appear in the Exception Rules list. Once saved, it cannot be changed. Use a name that will make the purpose of the policy clear.
Actions: Deny/Allow. Choose an action that contradicts the prevailing disposition of the policy as set by the Security Level.
Protocol: Select TCP/UDP to affect all traffic on the port, the typical assumption. Otherwise, to block or allow a specific application, match the protocol and port.
Direction: Inbound/Outbound or both. Blocking inbound traffic, for example, can prevent unauthorized access on the endpoint, while blocking outbound traffic can be used thwart malicious spyware or programs such as file sharing.
Figure 1: Exception Rule Configuration Screen 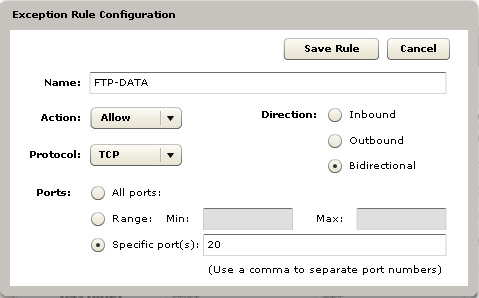
Ports: Ports 0-1023 are "well-known," 1024-49151 are registered ports, and those above 49151 are dynamic or private ports.
All ports: Includes ports 1 through 65535
Range: Create multiple, parallel exception rules to include a number of different ranges.
Specified port(s): Do not use zero or invalid input such as non-whole numbers.
