Sametime Gateway deployments
Use IBM® Sametime® Gateway to connect Sametime clients with other instant messaging clients. Several options are available for setting up a single server or a cluster of Sametime Gateway Servers in a network deployment. You can install a Sametime Gateway Server securely in the network DMZ. In some cases, Network Address Translators (NAT) is supported.
Topologies for a standalone server
A standalone Sametime Gateway Server has its own administrative console. Standalone servers do not require a SIP or XMPP proxy server. In the following configuration, the Sametime Gateway Server is deployed outside the internal firewall in the DMZ, while DB2® and LDAP servers are behind the firewall.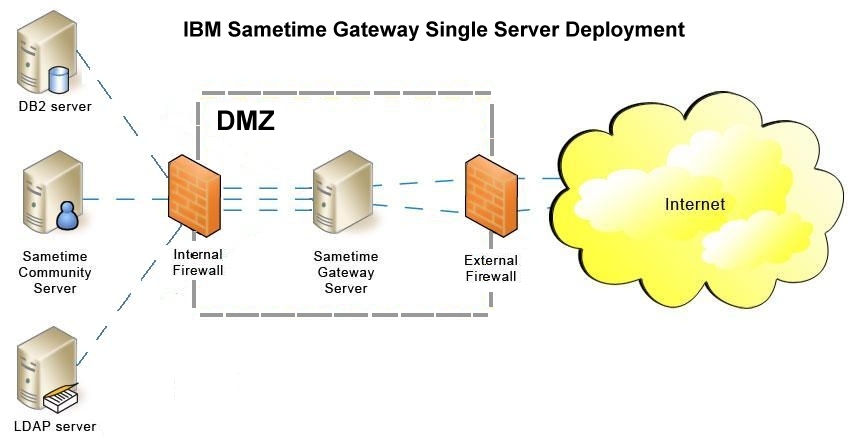
Topologies for a managed group of servers
Each of the following deployments consists of a cluster of servers that work together in a cell to provide high availability and failover. There is one administrative console to manage all servers. The following cluster deployments are considered:- Scenario: Two-computer installation of a cell of Sametime Gateway Servers
- Computer 1: DB2, Deployment Manager, primary node
- Computer 2: secondary node, proxy servers
- Scenario: Three-computer installation of a cell of Sametime Gateway Servers
- Computer 1: DB2
- Computer 2: Deployment Manager, primary node
- Computer 3: secondary node, proxy servers
- Scenario: Four-computer installation of a cell of Sametime Gateway Servers
- Computer 1: DB2
- Computer 2: Deployment Manager, primary node
- Computer 3: secondary node
- Computer 4: proxy servers
- Scenario: Five-computer installation of a cell of Sametime Gateway Servers
- Computer 1: DB2
- Computer 2: Deployment Manager, primary node
- Computer 3: secondary node
- Computer 4: secondary node
- Computer 5: proxy servers
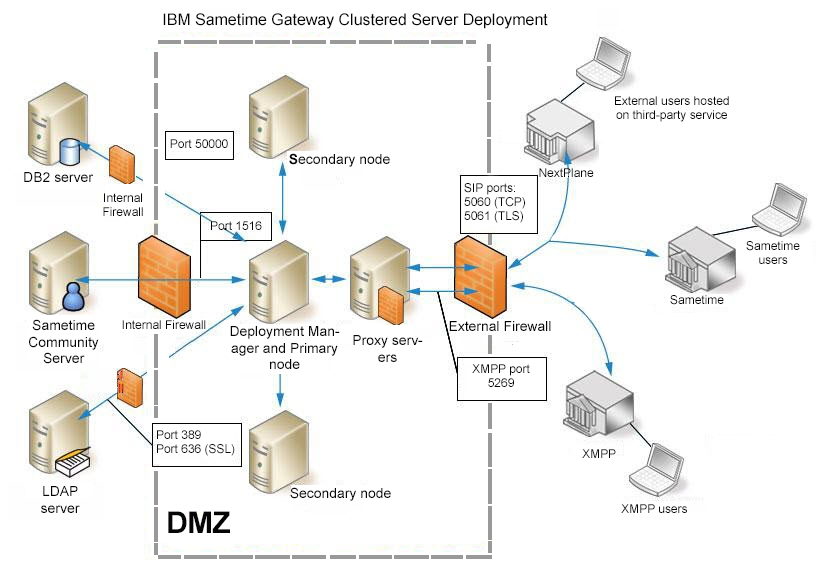
WebSphere® Application Server and DB2
- Clustering support, robust failover capability using the High Availability Manager
- Session Initiation Protocol (SIP) Infrastructure, including stateless SIP Proxy and SIP IP sprayer provided by the platform
- Open, extensible platform support. Additional plug-in services can configured in a flexible manner
- A central place to administer system configuration and monitoring and security policies through the Integrated Solutions Console and wsadmin script commands.
DB2 is the storage for the Sametime Gateway Server policies and logging. DB2 can be clustered for failover and load-balancing purposes. DB2 is part of the IBM common storage strategy. Domino® can use DB2 as an alternative repository, and Sametime Enterprise Meeting Server also uses DB2 for storing and sharing configuration data across servers. DB2 should be installed on a separate computer behind the internal firewall.
Typical deployment when connecting to instant messaging communities
Sametime Gateway Server allows selected individuals in your company to send instant messages to users on one or more public networks, giving your users immediate access to millions of users worldwide. When you connect to other Sametime companies, you can connect business users of different companies. This deployment is very useful in case of acquisitions when IT infrastructure is still separate, when you want to interconnect vendors over the Internet. Connections are made secure by using an SSL certificate exchange..
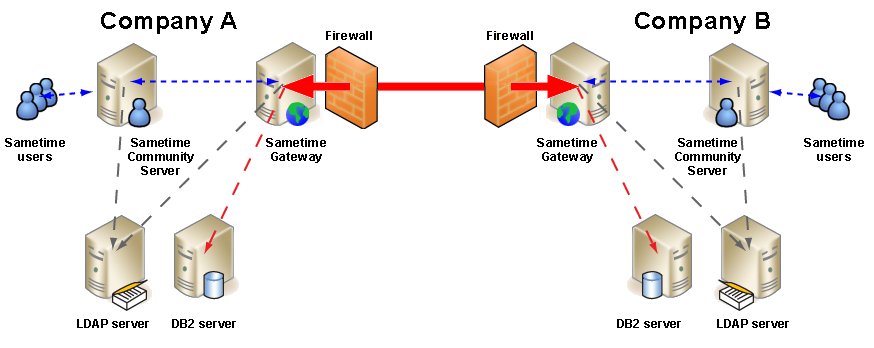
Recommended deployment
For small, test configurations only, you can install Sametime Gateway Server on the same computer as Sametime Community Server, DB2, or other applications. For a production environment, your Sametime Community Server should be installed on a separate computer from your Sametime Gateway Server.
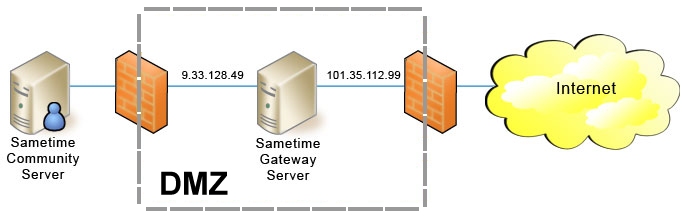
Multiple Network Interface Cards
The following graphic shows how you can simulate a NAT (Network Address Translator) by using two Network Interface Cards (NICs), one for an internal IP address and the other for an external IP address.
Deploying Sametime Gateway in the DMZ
The Sametime Gateway Server is an enterprise solution that requires a clustered deployment in the network DMZ. "DMZ" is a networking term that comes from the military term "demilitarized zone." DMZ refers to an area of a network, usually between two firewalls, where users from the Internet are permitted limited access over a defined set of network ports and to predefined servers or hosts. A DMZ is used as a boundary between the Internet and your company's internal network. The network DMZ is the only place on a corporate network where Internet users and internal users are allowed at the same time.
- Firewall restrictions make it impossible for users from the Internet to directly access a Sametime Community Server on your corporate intranet, but Internet users can access Sametime Gateway Server in the network DMZ.
- Sametime Community Servers, behind the internal firewall, are accessible only over an encrypted VP protocol.
- DB2 is behind the internal firewall, restricted by host and port access.
- LDAP is behind the internal firewall, accessible over SSL and restricted by host and port access
- Sametime Gateway Server exchanges with other instant messaging providers over SIP can be encrypted with SSL.
The following graphic shows how Sametime Gateway security can be enhanced using the IBM WebSphere DMZ Proxy Server. Using this component, a firewall can be inserted between the SIP proxy (hosted on the DMZ Secure Proxy Server) and the Sametime Gateway Servers. The following two deployments are supported:
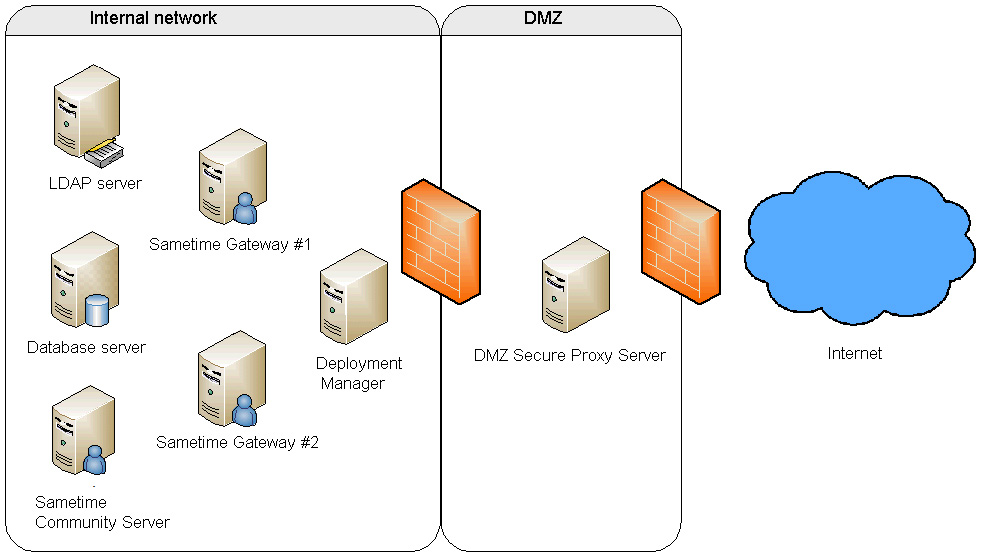
The following graphic shows a "single DMZ" configuration, the DMZ Secure Proxy Server is deployed in the DMZ while the rest of the Sametime servers, including Sametime Gateway Server, are deployed on the corporate intranet. All requests from external clients are routed through the DMZ Secure Proxy Server.
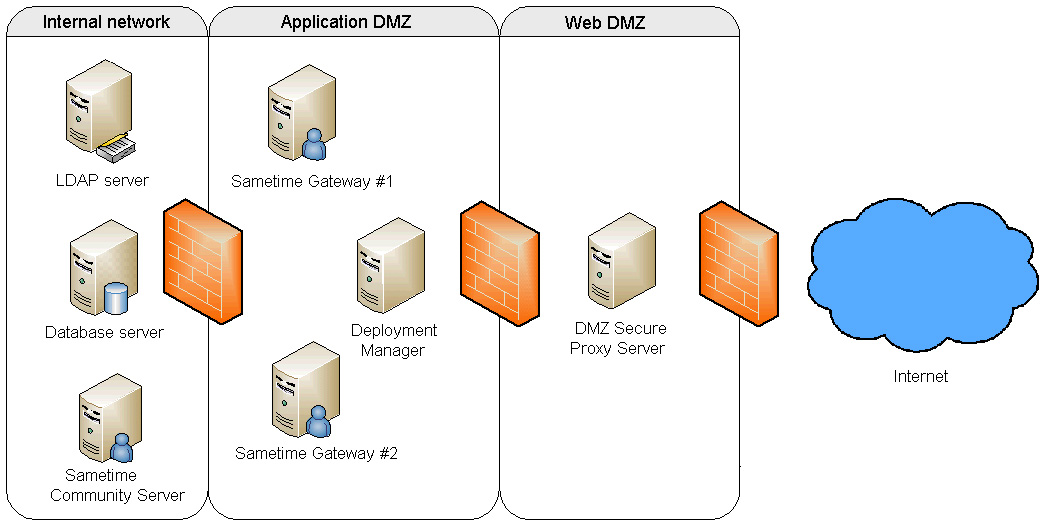
In the "dual DMZ" configuration, the DMZ Secure Proxy Server is deployed in the outermost "Web" DMZ, the Sametime Gateway Servers are deployed in an inner, "Application" DMZ, and the rest of the Sametime servers are deployed on the corporate intranet.
For more information on configuring Sametime Gateway with the DMZ Secure Proxy Server, see the following guide in the Sametime wiki: Sametime Gateway: Deploying DMZ Secure Proxy Server.
You can also deploy the Sametime Gateway XMPP server in the DMZ; for information, see the following guide in the Sametime wiki: Deploying a DMZ XMPP proxy server for Sametime Gateway.