Extending meetings to external clients and mobile users
How to plan for separated internal and external meetings, external access to internal meetings, and both. Includes server and port requirements, and topology diagrams.
Network considerations
If you will be supporting the use of LiveNames in your IBM® Sametime® deployment, you should deploy all Sametime Meeting Servers, Sametime Proxy Servers, and Sametime Advanced Servers within the same subnet. It is suggested that you configure the IBM WebSphere® Application Server with a single subnet for network traffic. You can use one network interface card on a physical computer or logical partition. You can also reference a single Domain Name System (DNS) server in the network configuration for the physical computer or logical partition.
Options to consider
- Separated internal and external meetings
- Allowing external access to internal meetings
- Both
- Access to DB2® from the DMZ
- Access to LDAP from the DMZ
- TLS/SSL encryption is recommended for all scenarios
- If you allow external access to internal meetings, you should consider authentication, meeting passwords, and document upload restrictions.
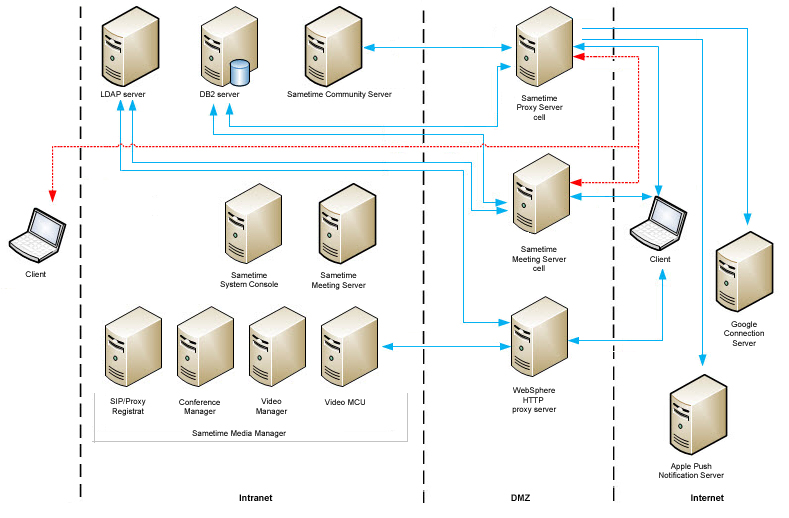
Separated internal and external meetings
- Over HTTP for administration of Meeting features (from System Console)
- Over HTTP for installation and upgrades (to the System Console)
When deploying the Sametime Meeting Server using the Sametime System Console, choose the Cell option.
- 9080/9443 to the System Console for installation and registration
- 389/636 to LDAP
- 50000/50001 to DB2 for Meeting data storage
- 9080/9443 for web traffic (configurable)
- 80/443 if you choose to deploy a WebSphere HTTP proxy server in front of a cluster of Meeting Servers
- LDAP
- DB2
- Sametime Community Server
- Sametime Meeting Server (Internal)
- Sametime System Console
- Sametime Media Manager
- Conference Manager
- Video Manager
- Video MCU
- SIP Proxy/Registrar
- Sametime Proxy Server
- Sametime Meeting Server (External)
- Sametime Community Server in the intranet to Sametime Proxy Server in the DMZ: TCP 1516
- LDAP and Sametime Media Manager: TCP 389 or 636
- Sametime Community Server and Sametime Media Manager: TCP 1516
- DB2 in the intranet, and Sametime Proxy Server and Sametime Meeting Server in the DMZ: TCP 50000 or 50001
- Sametime Proxy Server to the Apple Push Notification Server: 80 or 443
- Sametime Proxy Server to the Google Connection Server: 443
- Internal client and Sametime Community Server: VP 1533
- Internal client and Sametime Meeting Server: TCP 80 or 443
- Internal client and Sametime Proxy Server: TCP 80 or 443 (443 only for Google Connection Server)
- Internal client and Sametime Media
Manager in the intranet:TCP 5060
- 40000 to 49999 UDP (Starting with S9 GA until OpenSSL Security Bulletin released in September, 2015)
- 49152-59151 UDP (Starting with OpenSSL Security Bulletin released in September, 2015 )
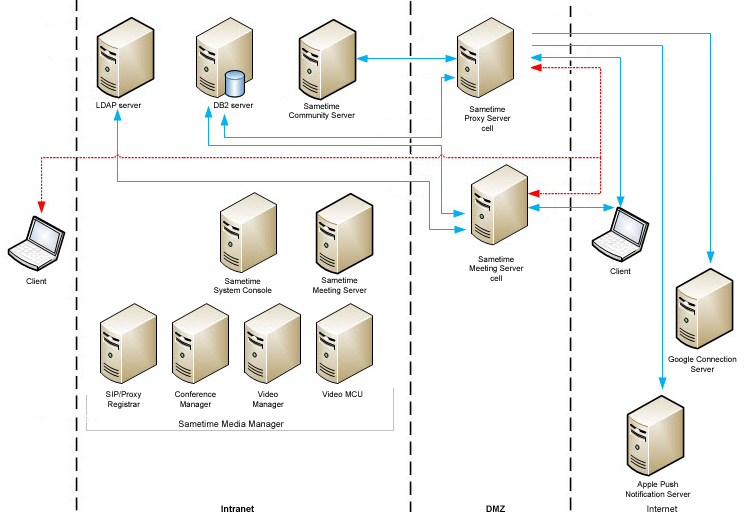
External access to internal meetings
Deploy a WebSphere HTTP proxy server to the DMZ. Use the Sametime System Console for administration. The Sametime Proxy Server and the Meeting Server are part of the cell. Communication with the Sametime System Console is over HTTP for installation and upgrades. The WebSphere HTTP proxy server will route HTTP traffic to the internal Meeting Server nodes over the Web Container ports.
When planning the deployment using the Sametime System Console, choose the Secondary Node option. After installation, the Application Server will be removed and you can create a WebSphere HTTP proxy server on that node.
- 9080/9443/8701/8703 to the Sametime System Console for installation and registration
- 389/636 to LDAP (required)
- WebSphere key ports
- Web Container ports to the internal Sametime Meeting Server nodes
Ports to open to the WebSphere HTTP proxy server from the Internet: 80/443
- LDAP
- DB2
- Sametime Community Server
- Sametime Meeting Server (Internal)
- Sametime System Console
- Sametime Media Manager
- Conference Manager
- Video Manager
- Video MCU
- SIP Proxy/Registrar
- Sametime Proxy Server
- WebSphere proxy server
- Sametime Community Server in the intranet to Sametime Proxy Server in the DMZ: TCP 1516
- WebSphere HTTP proxy server and LDAP: TCP 389 or 636
- WebSphere HTTP proxy server and Sametime Media Manager: WebSphere transports
- LDAP and Media Manager: TCP 389 or 636
- Sametime Community Server and Sametime Media Manager: TCP 1516
- DB2 in the intranet, and Sametime Proxy Server and Sametime Meetings Server in the extranet: TCP 50000 or 50001
- Sametime Proxy Server to the Apple Push Notification Server: 80 or 443
- Sametime Proxy Server to the Google Connection Server: 443
- External client and WebSphere HTTP proxy server: TCP 80 or 443
- External client and Sametime Proxy Server: TCP 80 or 443
- Internal client and Sametime Community Server: VP 1533
- Internal client and Sametime Meeting Server: TCP 80 or 443
- Internal client and Sametime Proxy Server: TCP 80 or 443 (443 only for Google Connection Server)
- Internal client and Sametime Media
Manager in the intranet:TCP 5060
- 40000 to 49999 UDP (Starting with S9 GA until OpenSSL Security Bulletin released in September, 2015)
- 49152-59151 UDP (Starting with OpenSSL Security Bulletin released in September, 2015 )
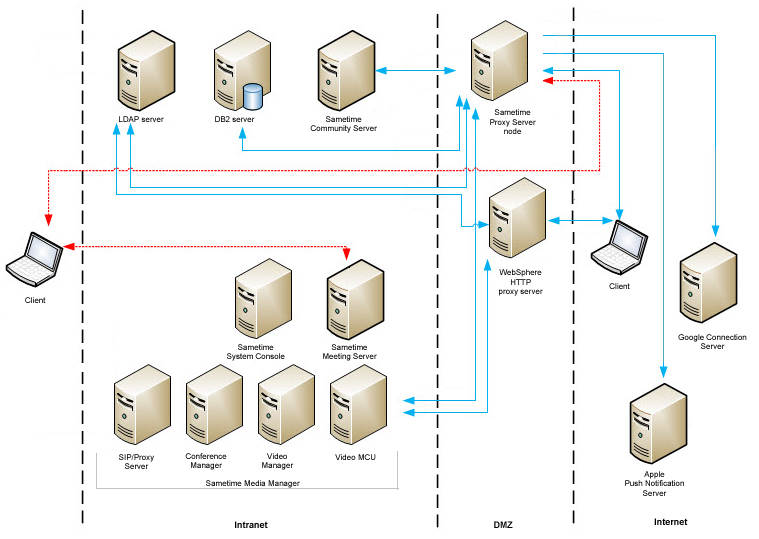
Separate internal and external meetings and external users can attend internal meetings
Deploy the a Meeting Server, Sametime Proxy Server, and WebSphere SIP Proxy Server together in a separate cell in the DMZ, separated from Community and Meeting services in the internal cell. In addition, external users have access to audio and video capabilities.
The following diagram shows a typical deployment that allows internal and external meetings, where external users can attend internal meetings. The deployment uses a separate cell of meetings in the DMZ, separated from the internal cell.
- LDAP
- DB2
- Sametime Community Server
- Sametime Meeting Server
- Sametime System Console
- Sametime Media Manager
- Conference Manager
- Video Manager
- Video MCU
- SIP Proxy Registrar
- Sametime Proxy Server
- Sametime Meetings Server
- WebSphere HTTP proxy server
- Sametime Community Server in the intranet to Sametime Proxy Server in the DMZ: TCP 1516
- WebSphere HTTP proxy server and LDAP: TCP 389 or 636
- WebSphere HTTP proxy server and Sametime Media Manager: WebSphere transports
- LDAP and Media Manager: TCP 389 or 636
- Sametime Community Server and Sametime Media Manager: TCP 1516
- DB2 in the intranet, and Sametime Proxy Server and Sametime Meetings Server in the extranet: TCP 50000 or 50001
- Sametime Proxy Server to the Apple Push Notification Server: 80 or 443
- Sametime Proxy Server to the Google Connection Server: 443
- External client and WebSphere proxy server: TCP 80 or 443
- External client and Sametime Proxy Server: TCP 80 or 443
- Internal client and Sametime Community Server: VP 1533
- Internal client and Sametime Meeting Server: TCP 80 or 443
- Internal client and Sametime Proxy Server: TCP 80 or 443
- Internal client and Sametime Media
Manager in the intranet:TCP 5060
- 40000 to 49999 UDP (Starting with S9 GA until OpenSSL Security Bulletin released in September, 2015)
- 49152-59151 UDP (Starting with OpenSSL Security Bulletin released in September, 2015 )