How to configure BigFix to integrate with SAML 2.0
How to configure the SAML identity provider and the BigFix server.
Before configuring the integration, ensure that:
- The BigFix server can resolve the hostname used in the URL for the identity provider login page.
- The identity provider (ADFS server or another type of supported SAML authentication providers) can resolve the BigFix root server hostname specified in the redirect URLs used to communicate with the Web UI, Web Reports, and BigFix console.
- The Web UI is enabled and active.
The overall configuration comprises two parts:
- The configuration of the SAML identity provider for explicit two-factor authentication, which is
under the responsibility of the identity provider administrator. For what concerns this part, ensure that:
- The redirect URLs are added to the relying party trust indexed, with binding HTTPS_POST, and in
this format:
https://<WebUI_server>/saml(for the Web UI server, assuming that it listens on port 443)https://<Web_Reports_server>:8083/saml(for each Web Reports server, assuming that they listen on port 8083)https://<Bigfix_server>:52311/saml(for the BigFix Console)Note: If the identity provider is ADFS, the redirect URLs must be added, as SAML Assertion Consumer Endpoints, in the Endpoints tab inside the ADFS Relying Party Trust properties. - In the Identity Provider configuration, the login setting must be set for FORMS login.
- If you plan to use the smart card authentication, ensure that the Identity Provider is correctly configured to use multi factor authentication. For example, if you use ADFS, ensure that at least one between Certificate Authentication and Windows Authentication, if you want to use the Windows Integrated Authentication, is enabled in the Global Authentication Policy configuration.
- For Active Directory user authentication, set the identity provider Claim Rules as follows:
- Attribute store:
- Active Directory
- Mapping of LDAP attributes to outgoing claim types:
-
- LDAP Attribute: User-Principal-Name
- Outgoing Claim: Name ID
- The redirect URLs are added to the relying party trust indexed, with binding HTTPS_POST, and in
this format:
- The configuration to allow the BigFix server
to use SAML authentication, which is a Master Operator (MO) and Web
Reports administrator responsibility. Complete these steps to accomplish
this task:
- Configure LDAP with Active Directory in the BigFix Console. For more details, see Integrating the BigFix Windows server with Active Directory.
- Define LDAP operators. For more details, see Adding LDAP Operators.
- Define Web Reports LDAP operators in the Web Reports user management pages.
- Access the Administration page to configure the integration with SAML 2.0:
- Log in to the Web UI server:
- If the Web UI listens on port 443:
https://<WebUI_server> - If the Web UI listens on a port that is different than 443:
https://<WebUI_server>:<webui_port_number>
- If the Web UI listens on port 443:
- Open the Administrator page:
- If the Web UI listens on port 443:
https://<WebUI_server>/administrator - If the Web UI listens on a port that is different than 443:
https://<WebUI_server>:<webui_port_number>/administrator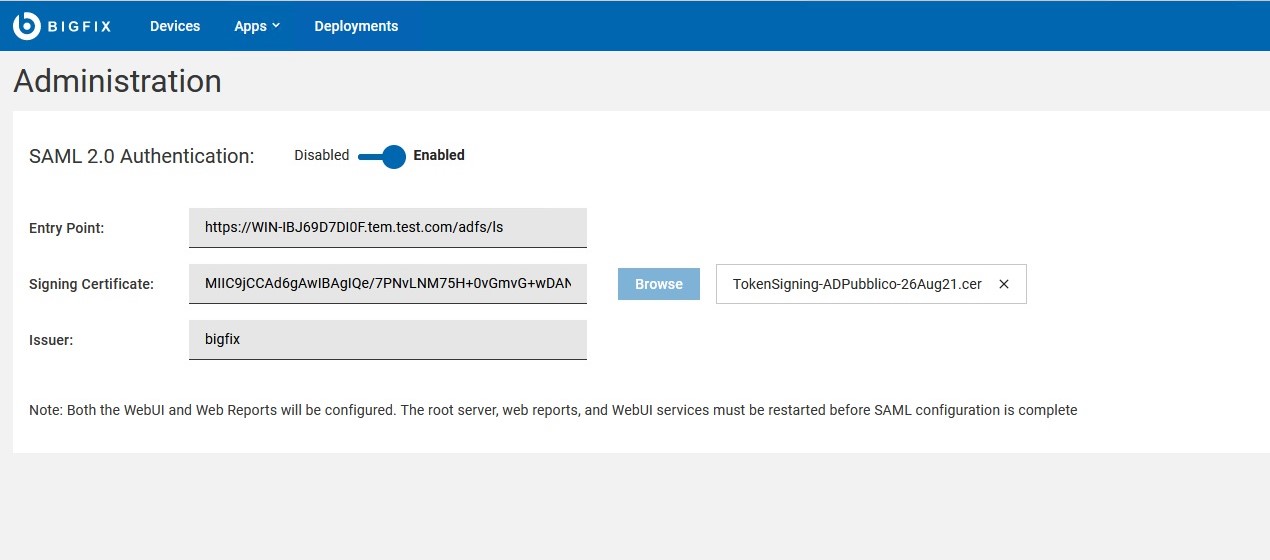
- If the Web UI listens on port 443:
- Log in to the Web UI server:
- In the Administration page, specify:
- Entry Point:
- The Identity Provider login URL. It is the URL from where the
operator can log in and be redirected back to Web UI or to the Web
Reports, for example
https://<idp_fqdn>/adfs/ls. - Signing Certificate:
- Browse for the certificate file or paste in this field the key from the Identity Provider certificate in Base-64 encoded X.509 (.CER) format.
- Issuer:
- Enter the Identity Provider Identifier in a textual format, for example "BigFix". If you are configuring ADFS configuration, this value must match the ADFS Relying Party Identifier setting.
- After filling in all the fields, click Enable.
- If WebUI is installed on a separate remote server, set the
_WebUI_AppServer_Hostnamekey of the BigFix server computer to the hostname, fully qualified domain name (FQDN) or IP address of the computer where the WebUI is installed (the WebUI Server computer), ensuring that it matches the WebUI certificate subject name, as specified in BES WebUI\cert\auth_cert.crt on Windows and in BESWebUI/cert/auth_cert.crt on Linux. If the default WebUI port was changed (_WebUIAppEnv_APP_PORT), you must set the_WebUI_Monitor_Portkey of the BigFix server computer to use the new WebUI port.Note: Ensure that the port of the WebUI server (default HTTPS 5000) is reachable by the BigFix root server. - If you want to enable the Web-based Single Sign-On (SSO) authentication method, on the WebUI machine set the _WebUIAppEnv_SAML_SSO_ENABLE key to 1.
- If you want to enable the use of smart cards as SAML authentication method, set on the WebUI
Server computer the
_WebUIAppEnv_SAML_AUTHNCONTEXTsetting to one of the following two values:urn:oasis:names:tc:SAML:2.0:ac:classes:TLSClientif the Identity Provider is set to use the Transport Layer Security (TLS) cryptographic protocol.urn:federation:authentication:windowsif the Identity Provider is set to use Integrated Windows Authentication (IWA).
- Restart the BigFix root server.
- Restart the BigFix Web Reports services.
- Restart the WebUI Service.
After these steps are successfully run, all LDAP operators from these services must authenticate through the configured identity provider.
An administrator can use the Administration page also to update the existing configuration.
Note: After completing these steps, to prevent errors when logging on to the BigFix console, ensure that you set for the
_BESDataServer_AuthenticationTimeoutMinutes configuration setting a value,
specified in minutes, bigger than 5 minutes.The following links contain some configuration examples for well known Identity Providers: