Initiative report
The Initiative Report provides an overview of CVEs (Common Vulnerabilities and Exposures) categorized by different computer groups found in the user's environment. Its purpose is to display the number of vulnerabilities across machines, giving insights into the distribution of vulnerabilities.
Two primary use cases revolve around the comparative and comprehensive aspects of each initiative:
-
Comparative aspect: In cases where the security team emphasizes cleanup efforts, this aspect allows users to assess and track the progress made in the cleanup process.
-
Comprehensive aspect: Once the cleanup is completed, users can evaluate how each department, location or computer group in comparison to one another.
To view the Initiative report, from BigFix CyberFOCUS Analytics web report, click the Initiative tab.
Select initiative
Select the Initiative and Super Group, then click Select.
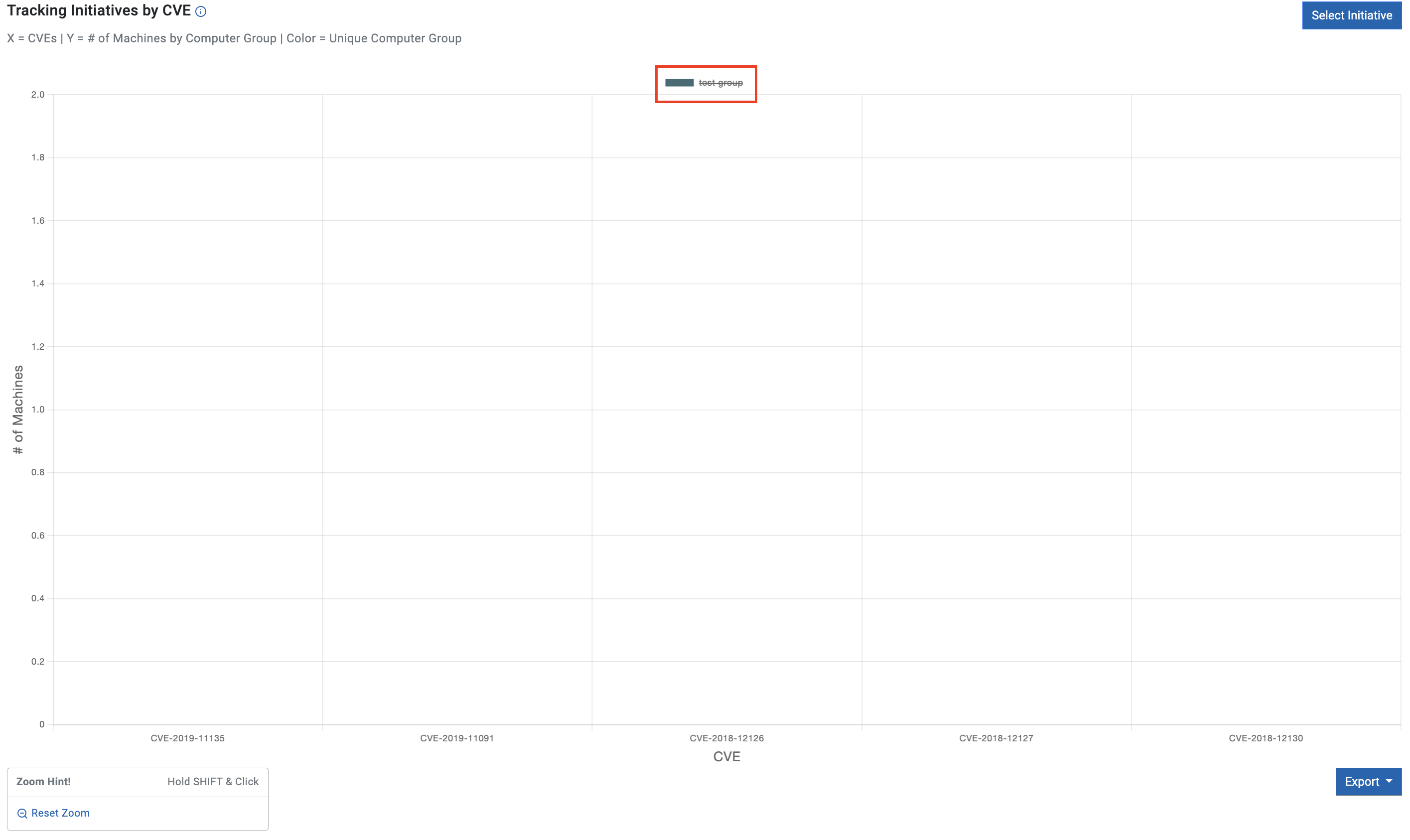
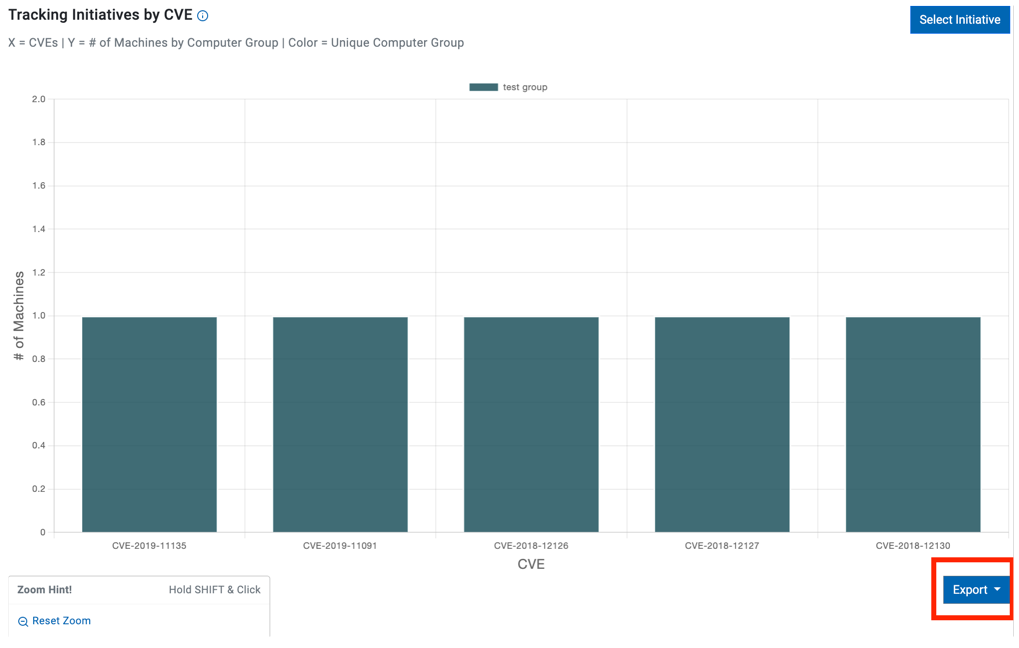
Tracking initiatives by CVE
Tracking initiatives by CVE chart represents vulnerability data across various CVEs categorized by initiative groups. This visualization allows for a quick understanding of which initiative groups are more prone to specific vulnerabilities. It also has the ability to show how the chart would change If the entire group was completely mitigated.
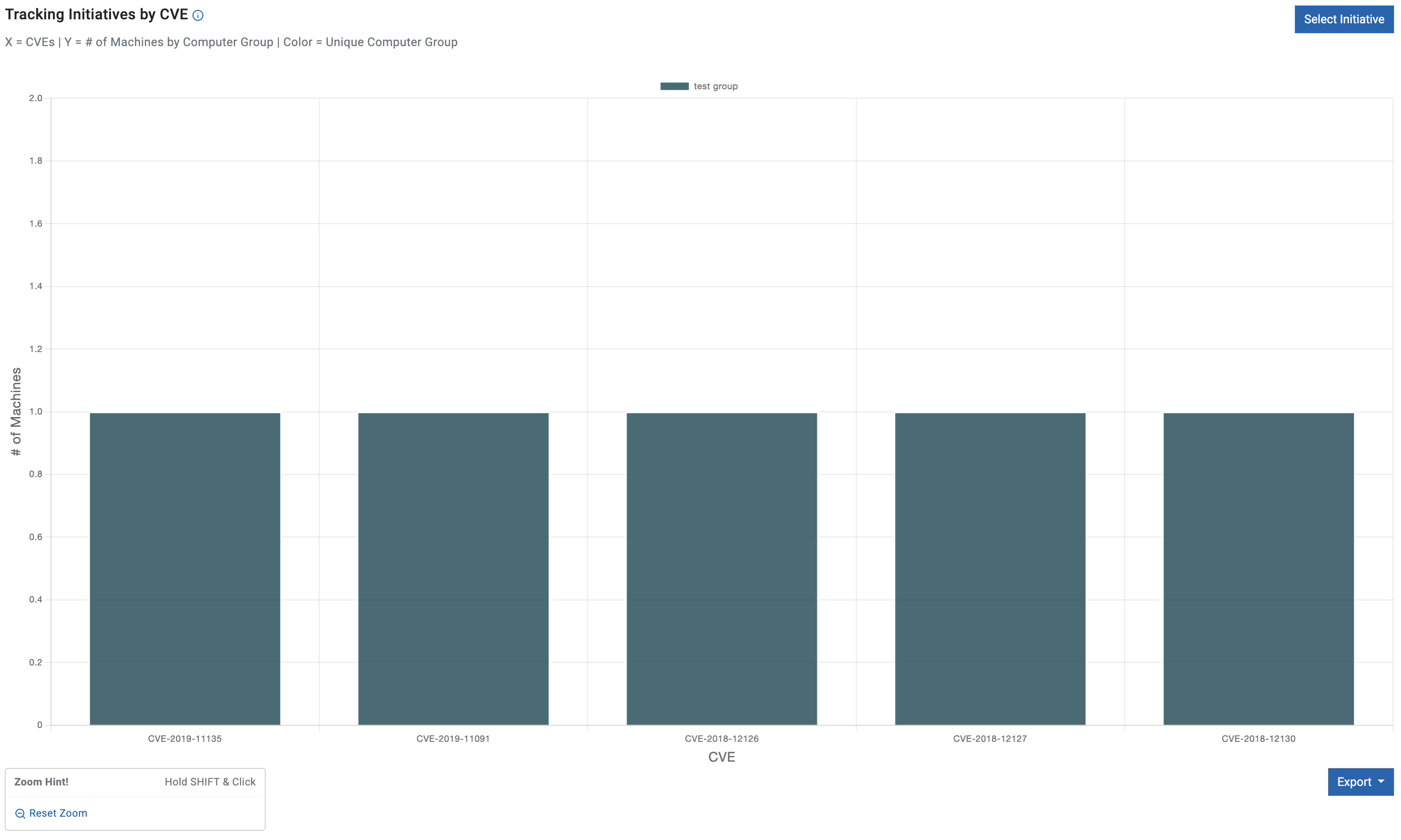
- X-axis indicates CVEs broken down to the initiative group set
- Y-axis indicates number of machines vulnerable to the relevant CVE
- Color indicates unique Computer Group
To see how the graph would look like if the entire group was entirely mitigated, click on the Alias Group above the chart.
Example below shows how the graph changes when clicking test group.
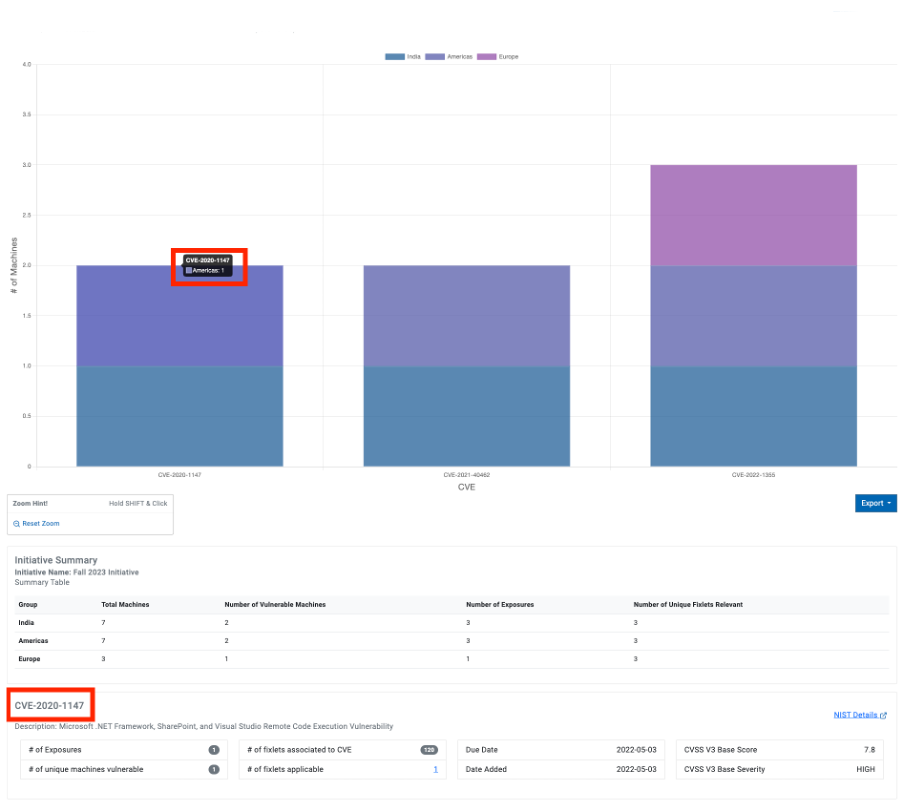
Select a specific CVE to view its details. Once a particular CVE is clicked, the system remains focused on that specific CVE until a different one is selected.
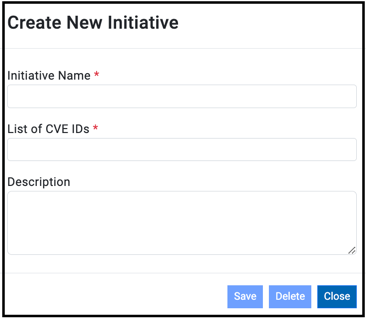
Create/Edit Initiative
To edit Initiative or create a new one, select Create or Edit and provide required details:
- Initiative Name
- List of CVE IDsNote: CVEs can be separated by semicolon, comma, or space. The maximum allowable number of CVEs is 30.
- Description - provide short description of the Initiative
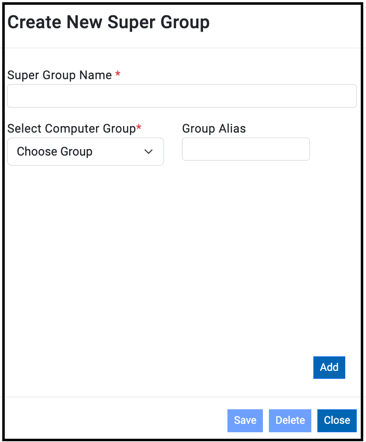
Create/Edit Group Set
To edit Group Set or create a new one, select Create or Edit and provide required details:
- Super Group Name
- Select Computer GroupNote: The maximum allowable number of super groups is 30.
- Group Alias
Initiative summary
The Initiative Summary table provides additional information about the selected Initiative. For example, Total machines, Number of Vulnerable Machines. This pane is dynamically updated based on the selected Initiative.
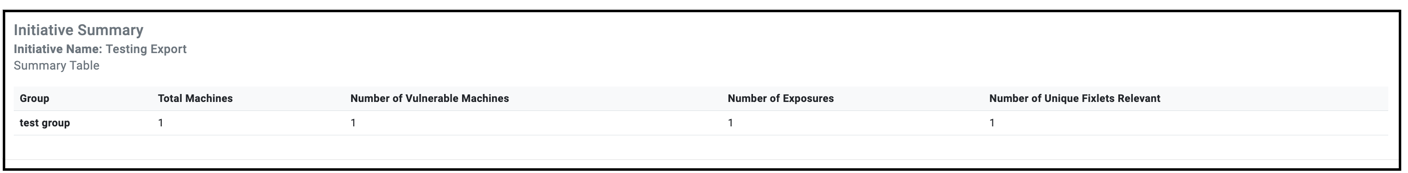
The Initiative summary table is represented in a tabular format and contains the following columns:
- Group set
- Total Machines
- Number of Vulnerable Machines
- Number of Exposures
- Number of Unique Fixlets Relevant
Export CVE (.csv)
To export the list of CVEs, click on the Export option located in the right corner of the chart. The exported CSV file will contain essential information about each CVE, including the vulnerability name, CVE description, and details associated to computer group, exposures, and the number of unique machines.
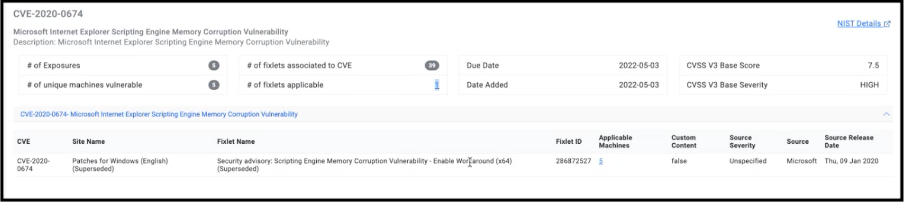
Machine Drilldown
The Machine Drilldown feature enables the user to focus on specific CVEs and gather information by drilling down into multiple Fixlets. The list of devices in the Drilldown tab is expanded as additional Fixlets are selected, and the results remain available for analysis and further action.
User visibility filtering
When a secondary user initiates a support operation, the User Visibility Filtering mechanism restricts the displayed computer groups to only those containing applicable computers for the respective user.
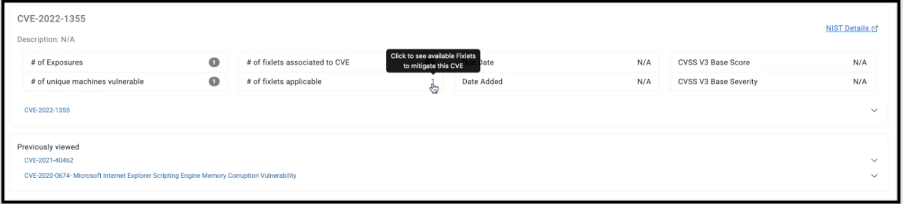
Previously viewed
The functionality enables users to select a specific CVE for detailed examination and perform a drill-down. User can explore other CVEs that have undergone similar drill-down procedures. This feature gives users the ability to review CVEs that were previously examined.
Debug
Go to Debug → Advanced Options to load initiatives from Mitre APTs or CISA as default initiatives.