Step 3: Enabling secure communication
You can enable encrypted communication (HTTPS) to ensure secure communication between your server and all users that access it. You can base your communication on self-signed certificates that are provided by default in BigFix Inventory, but these certificates are not intended for production environments. To improve security, create your own private key and certificate, and upload them to BigFix Inventory.
Before you begin
Note:
- The use of HTTPS is enabled by default, but this configuration is based on temporary self-signed certificates that are not intended for production environments.
- Enabling or disabling the use of HTTPS changes the web address of your BigFix Inventory server. Ensure that you run a data import afterward to update the address in the Fixlets that use it to download files from the server.
Procedure
Procedure
- Log in to BigFix Inventory.
- In the top navigation bar, click .
-
Select Use HTTPS. The Certificate subsection opens.
Important: Starting from application update
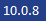 , the use of HTTPS is
selected by default.
, the use of HTTPS is
selected by default. - Provide information about the certificate.
- If you have a private key and a certificate:Note: The certificate and the key must be PEM-encoded or enfolded in PKCS#12 KeyStore.
- Select Import a PEM or PKCS#12 private key and certificate.
In application updates earlier than
 , select Import a PEM encoded private key and
certificate.
, select Import a PEM encoded private key and
certificate. - Click Browse to locate the file in the PEM or PKCS#12 format.
- If the private key and certificates are delivered in separated files, select Private key is in a separate file and locate the private key file.
- In the Private key password field, enter the password for the key. This field is required only if you set a password for your private key.
- Click Save.
Note: The certificate and the key must be PEM-encoded. - Select Import a PEM or PKCS#12 private key and certificate.
- If you want to generate a new self-signed certificate:Restriction: A self-signed certificate contains a public key, information about the owner of the certificate, and the owner's signature. Because such a certificate is signed by its own private key, it does not provide means to verify the origin of the certificate through a trusted certificate authority.
- Select Generate a self-signed certificate.
- Specify the certificate subject common name. The common name must correspond to the DNS name of BigFix Inventory.
- In the Expiration Date field, enter the date when the certificate expires.
- Click Save.
Note: Most browsers display a warning message when a self-signed certificate is used.
- If you have a private key and a certificate:
- Restart the server.