Discovering software in Docker containers
![]() Available from 9.2.5. Docker and Podman are platforms
that allow automating the deployment of applications inside software containers. BigFix Inventory
BigFix Inventory discovers
software that is installed inside Docker containers. It also measures license metric
utilization of the discovered BigFix products.
Available from 9.2.5. Docker and Podman are platforms
that allow automating the deployment of applications inside software containers. BigFix Inventory
BigFix Inventory discovers
software that is installed inside Docker containers. It also measures license metric
utilization of the discovered BigFix products.
Requirements
- Only one Docker or Podman engine is deployed on the host computer.
- The container is running.
- Scans and uploads of their results are enabled on the host computer.
- Software that is installed in the container delivers software ID tags.
- To ensure proper discovery of software on containers, the content of a container cannot change throughout its lifecycle.
- The BigFix client or disconnected scanner must be installed on the host computer.
- The Docker container is deployed on one of the following platforms:
- Red Hat Enterprise Linux 7 for x86
- Red Hat Enterprise Linux 7 for BigFix 64-bit)
- SUSE Linux 12 for x86
 Red Hat OpenShift container application platform
Red Hat OpenShift container application platform
- The Podman container must be deployed on one of the following platforms:
- Red Hat Enterprise Linux 8 for x86
- Red Hat Enterprise Linux 9 for x86
- Discovery of a software that is installed in Podman containers relies on the compatibility of the podman command arguments with the syntax of the docker command arguments.
- docker commands need to be redirected to the podman command in one of the
following ways:
- install podman-docker Red Hat package.
- configure the installation path for Podman engine using the computer setting. For more information, see:
Enabling software discovery in containers
Discovery of software that is installed in containers is enabled by default. In some Docker or Podman environments, you might need to perform additional steps to specify a non-default installation path, or to exclude directories from scanning. For more information, refer to Configuring scans on Docker containers. For information about disabling software discovery in containers, refer to Disabling scans on Docker containers.
Disconnected scanners
To enable discovery of software that is installed in containers, set the value of the DOCKER_SCAN_ENABLED parameter to true. For more information, see: Configuration parameters of the disconnected scanner (disconnected scenario).
Viewing software
Software that is installed in Docker containers can be viewed on the Software Installations report. It is presented under the host computer. To learn why the software was discovered, click Details.
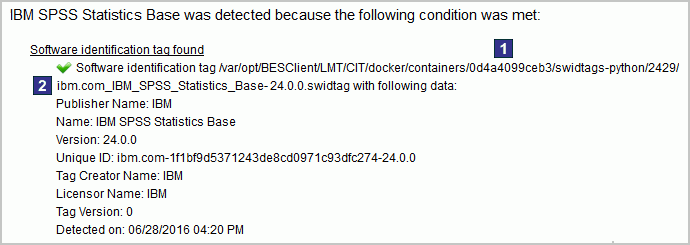
 Container on which the software was detected.
Container on which the software was detected. Software ID tag that caused the detection.
Software ID tag that caused the detection.
Measuring license metric utilization
Scenario 1: Docker or Podman engine deployed on a physical server
When the Docker or Podman engine is deployed directly on a physical server, PVU and RVU MAPC utilization is measured on the level of the host computer.
Example: Three containers are deployed on a physical server that has four Intel Xeon 3400 processors, each with six cores. It gives 24 cores in total. IBM MQ is installed in two out of three containers. BigFix Inventory counts PVU and RVU MAPC utilization on the level of the host computer.
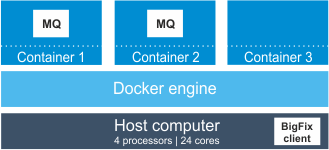
In this case, IBM MQ has access to 24 cores. According to the PVU table, when the server has four sockets, this processor model is assigned 100 PVUs per core. Thus, PVU utilization for IBM MQ equals 2400 PVUs. The value would be the same if another instance of IBM MQ was installed in the third container.
Scenario 2: Docker or Podman engine deployed on a virtual machine
When the Docker or Podman engine is deployed on a virtual machine, PVU and RVU MAPC utilization is counted as the highest number of PVUs that are available for the virtual machine.
- In one container on the first virtual machine
- In two containers on the second virtual machine
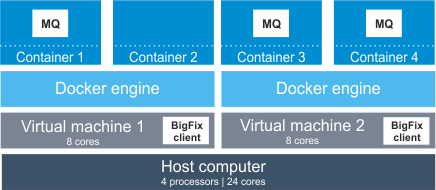
In this case, IBM MQ that is installed on each of the virtual machines has access to eight cores. In total, it has access to 16 cores out of 24 cores that are available on the physical computer. According to the PVU table, when the server has four sockets, this processor model is assigned 100 PVUs per core. Thus, PVU utilization for IBM MQ equals 1600 PVUs. If the Docker or Podman engine was deployed directly on the physical server, IBM MQ would have access to 24 cores and its PVU utilization would equal 2400 PVUs.
Logs
 var/opt/BesClient/LMT/CIT/docker_scan.log
var/opt/BesClient/LMT/CIT/docker_scan.log C:\Program Files (x86)\BigFix
Enterprise\BESClient\LMT\CIT\docker_scan.log
C:\Program Files (x86)\BigFix
Enterprise\BESClient\LMT\CIT\docker_scan.log