Configuring the SafeLinx server for Nomad
Configure the SafeLinx server for Nomad.
Before you begin
About this task
- Configure a SafeLinx login profile and then log in.
- Configure the SafeLinx Access Manager.
- Add a SafeLinx server.
- Configure a Nomad proxy for the SafeLinx server.
- Confirm the configuration.
Procedure
-
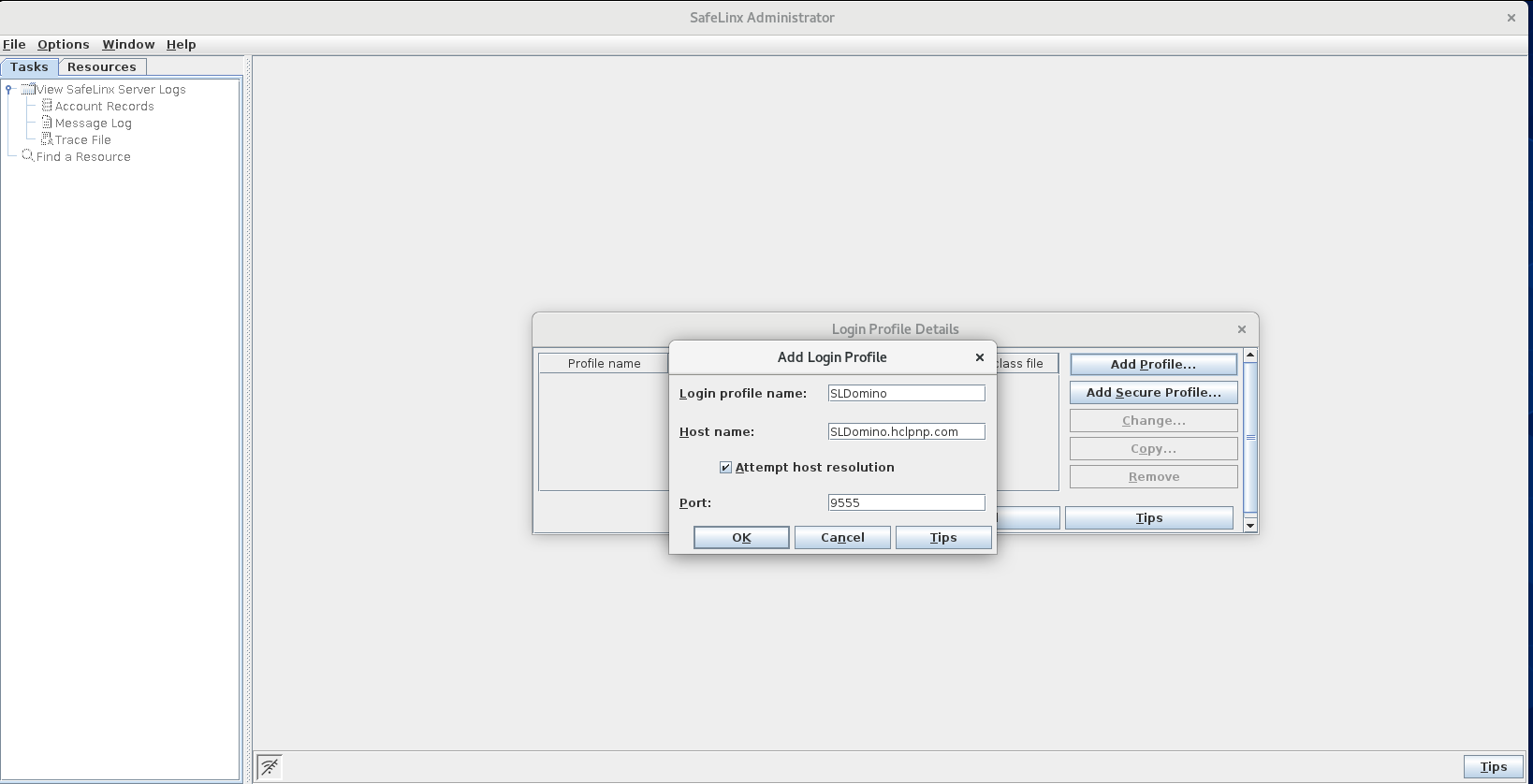
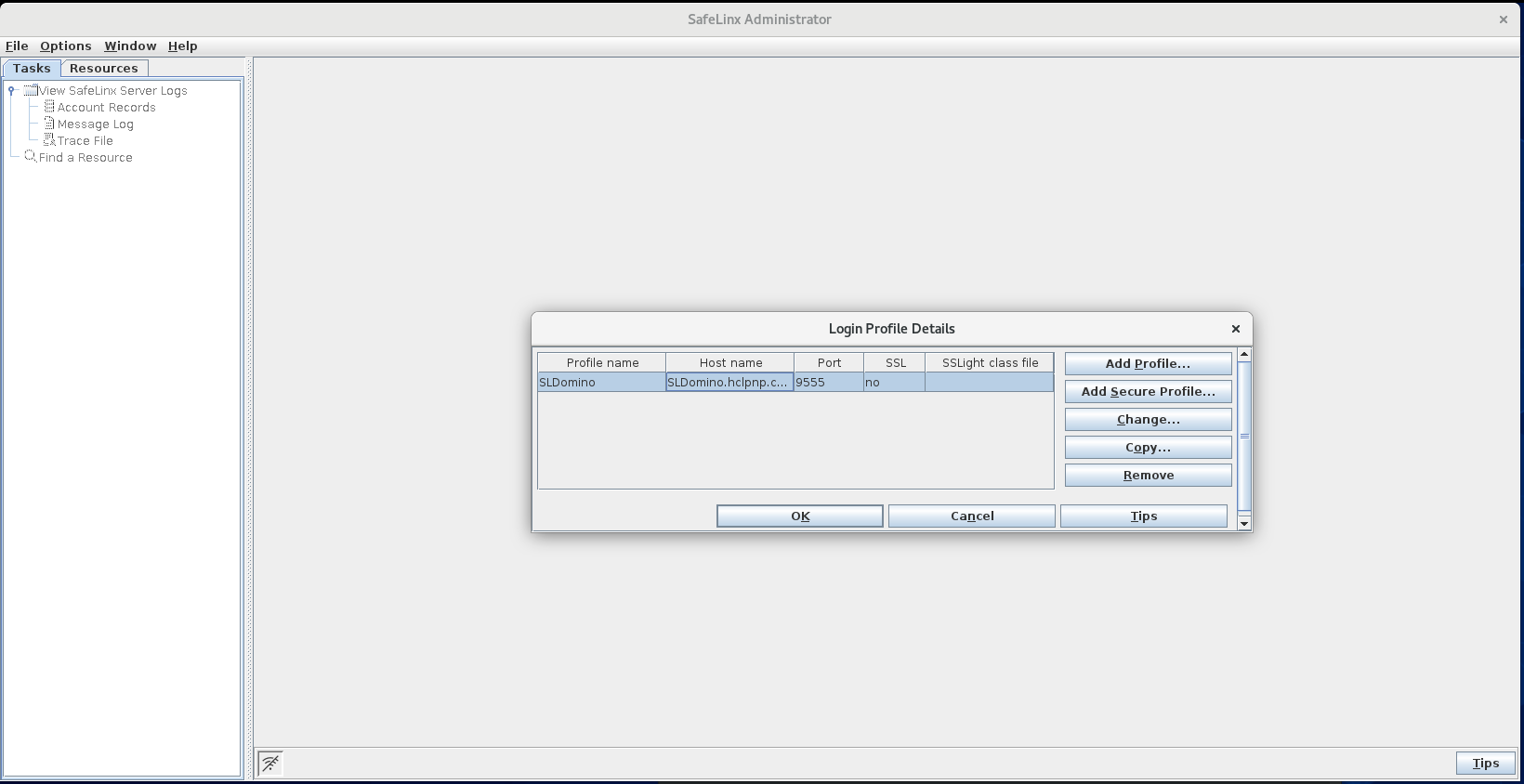
Configure a SafeLinx login profile and then log in:
-
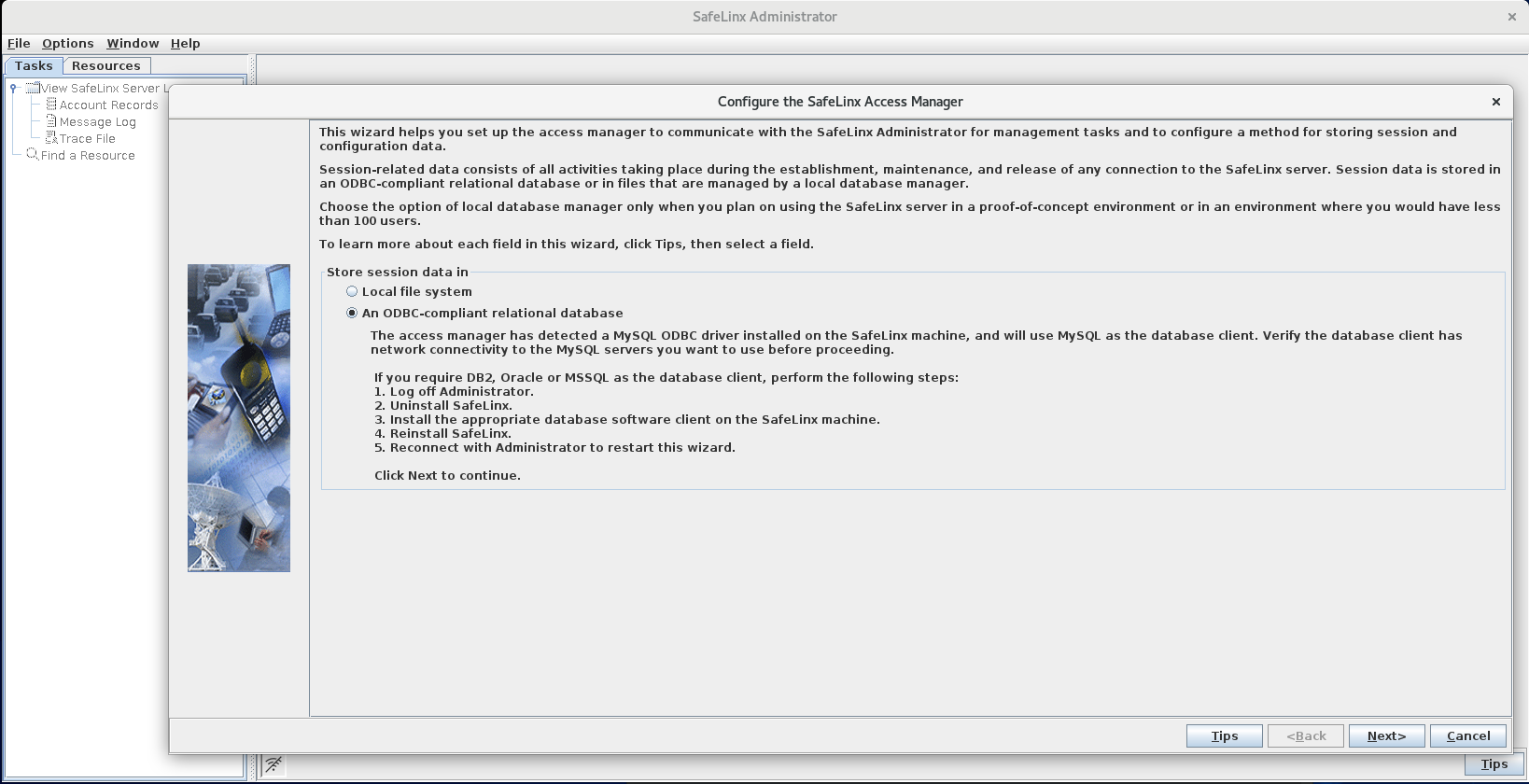
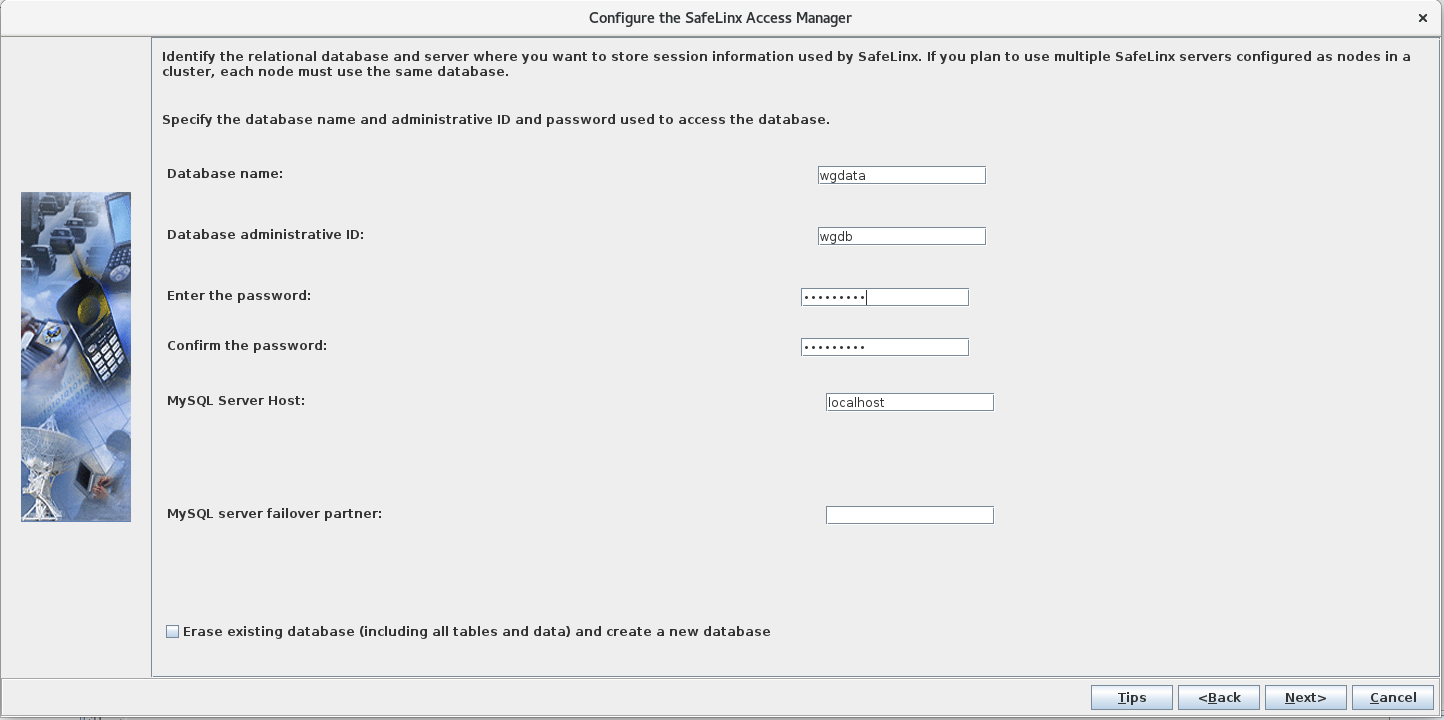
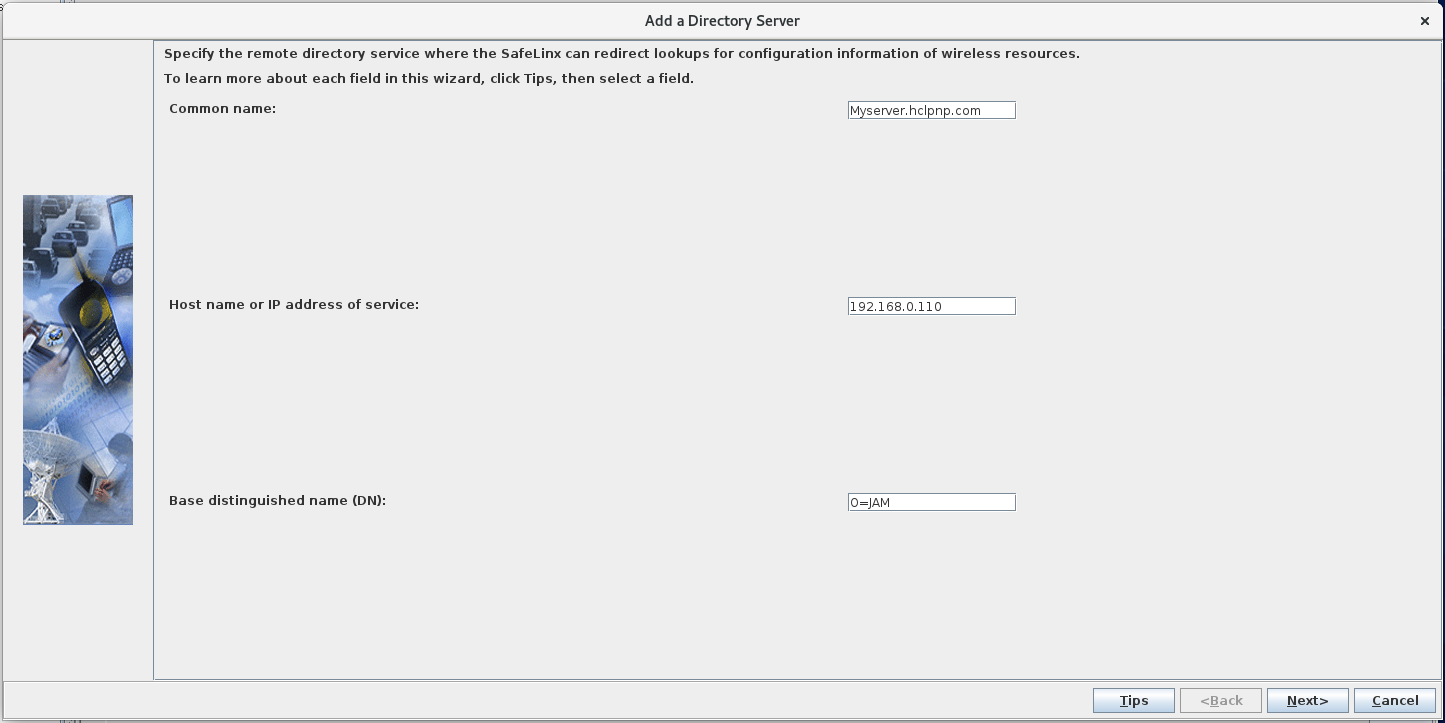
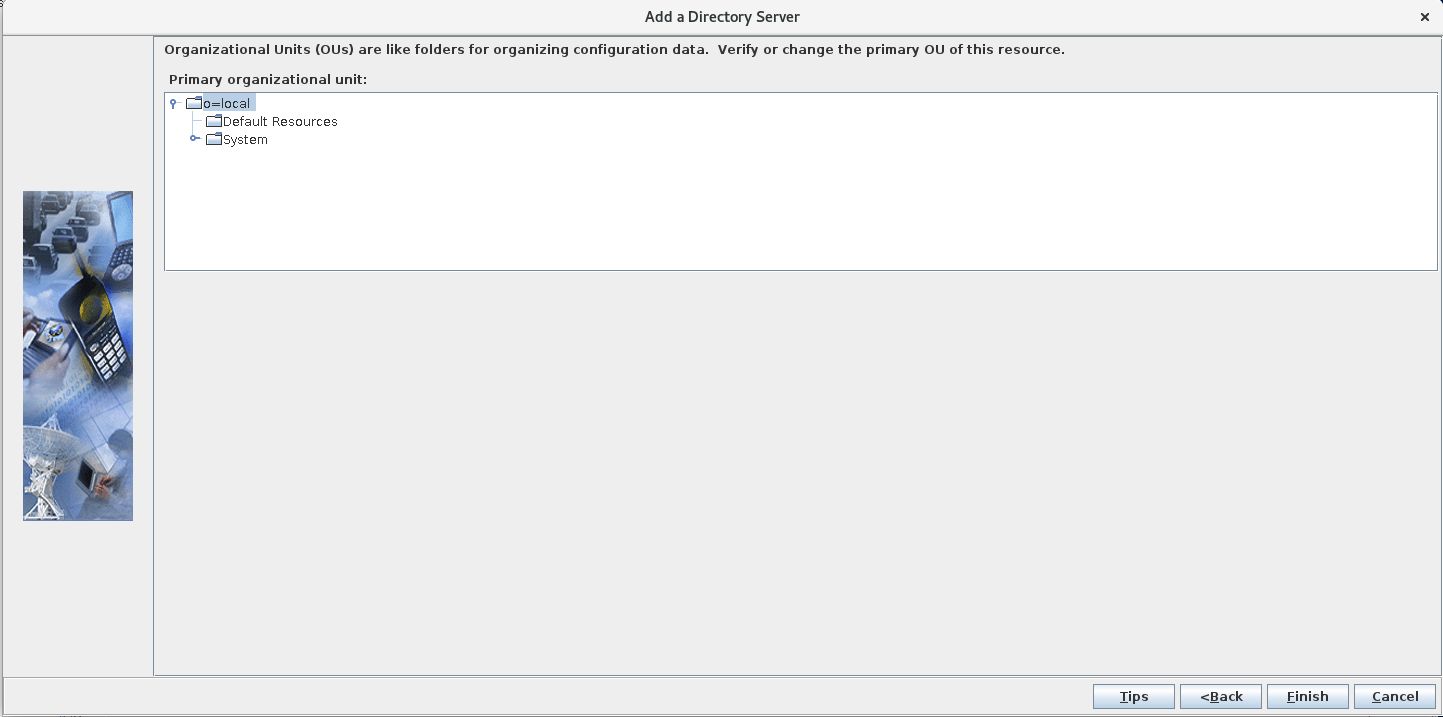
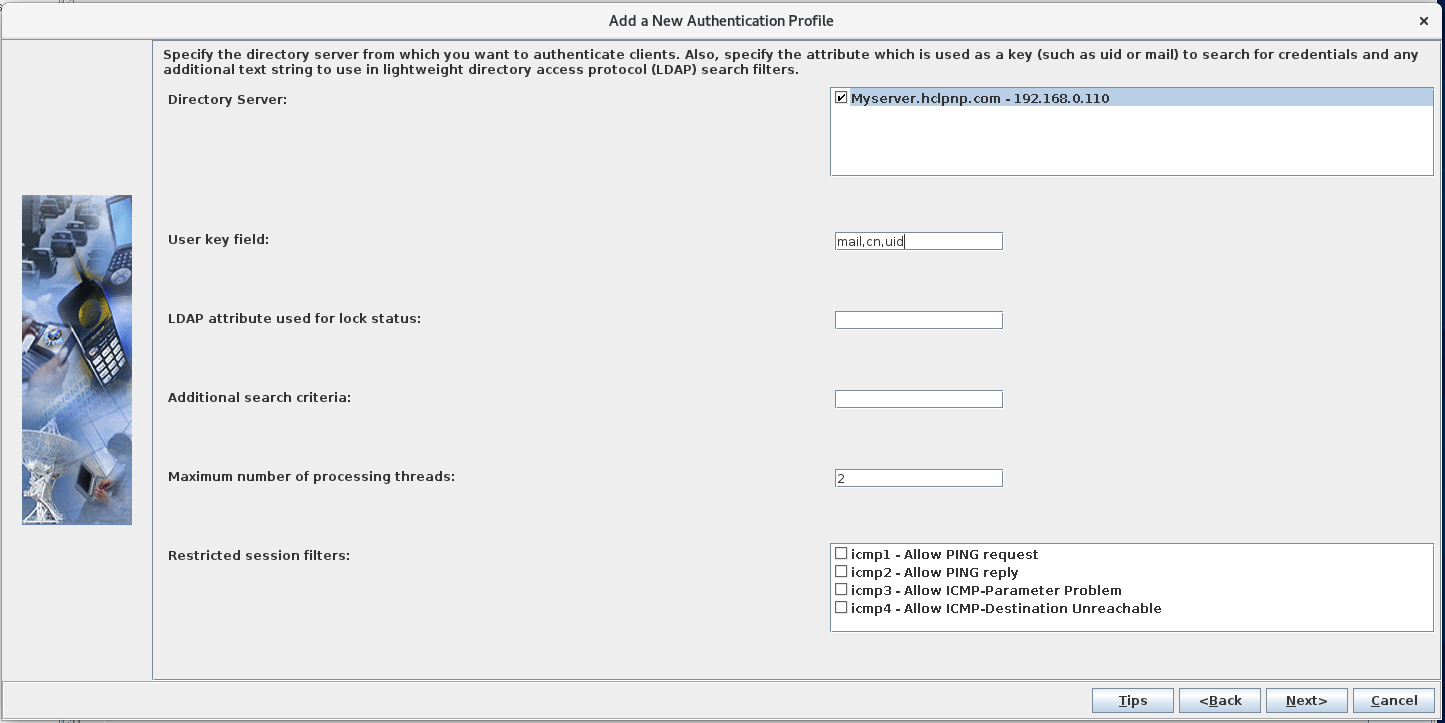
Configure the SafeLinx Access Manager:
-
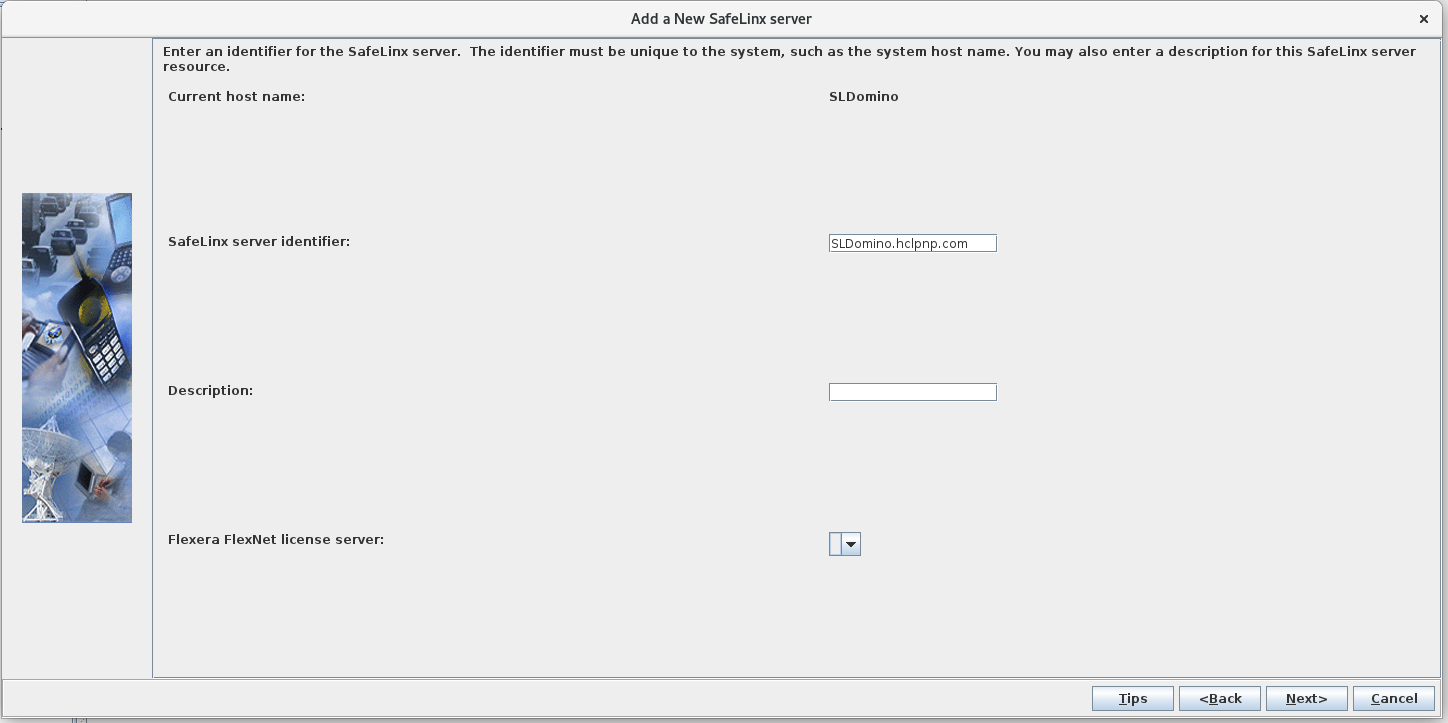
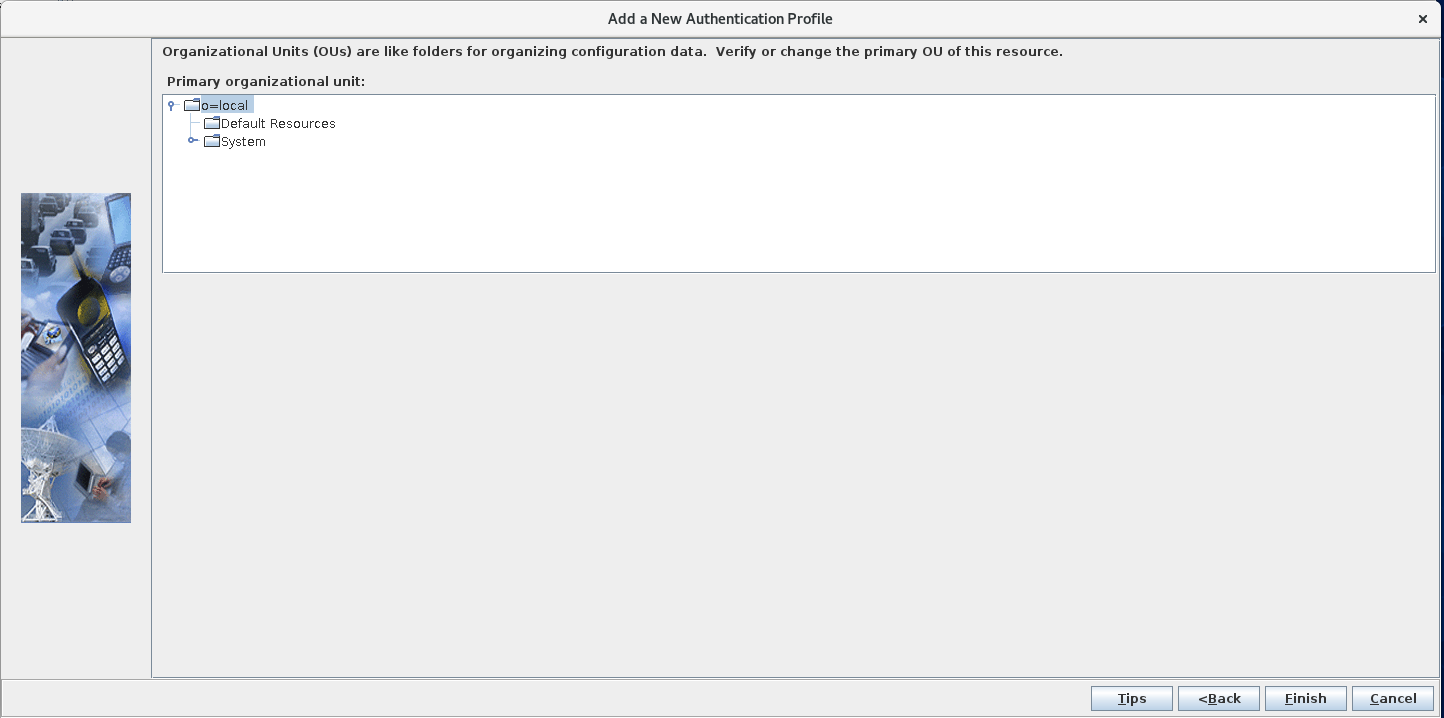
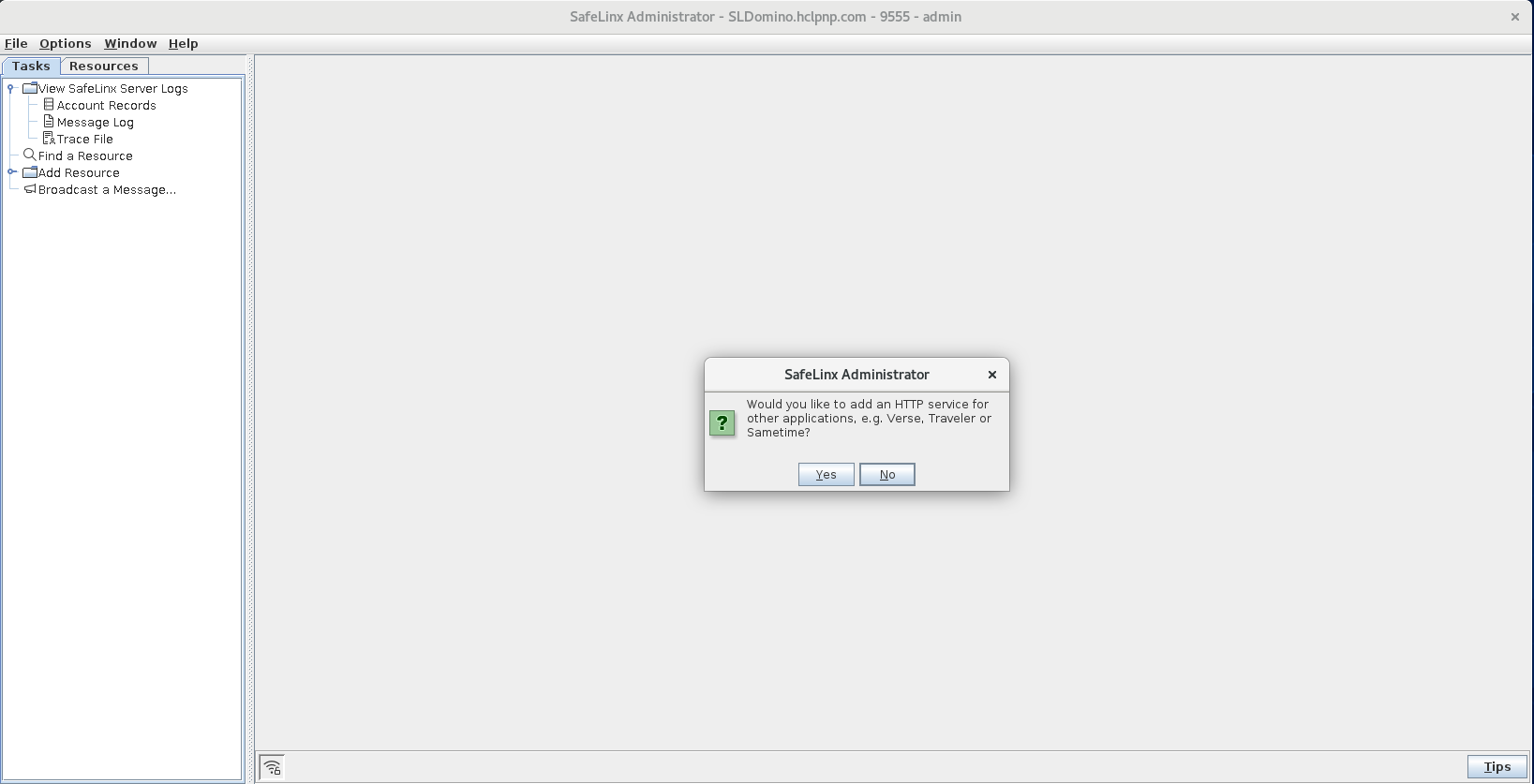
Add a new SafeLinx server:
-
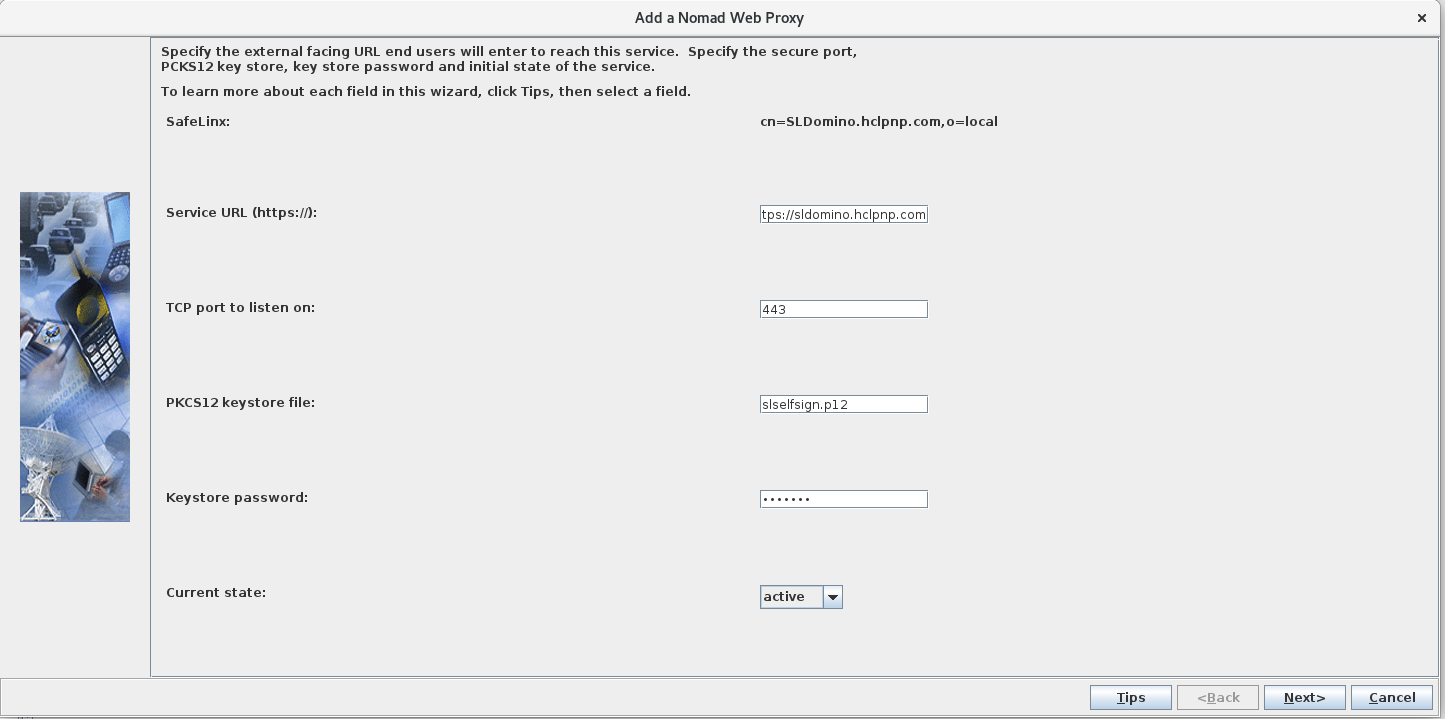
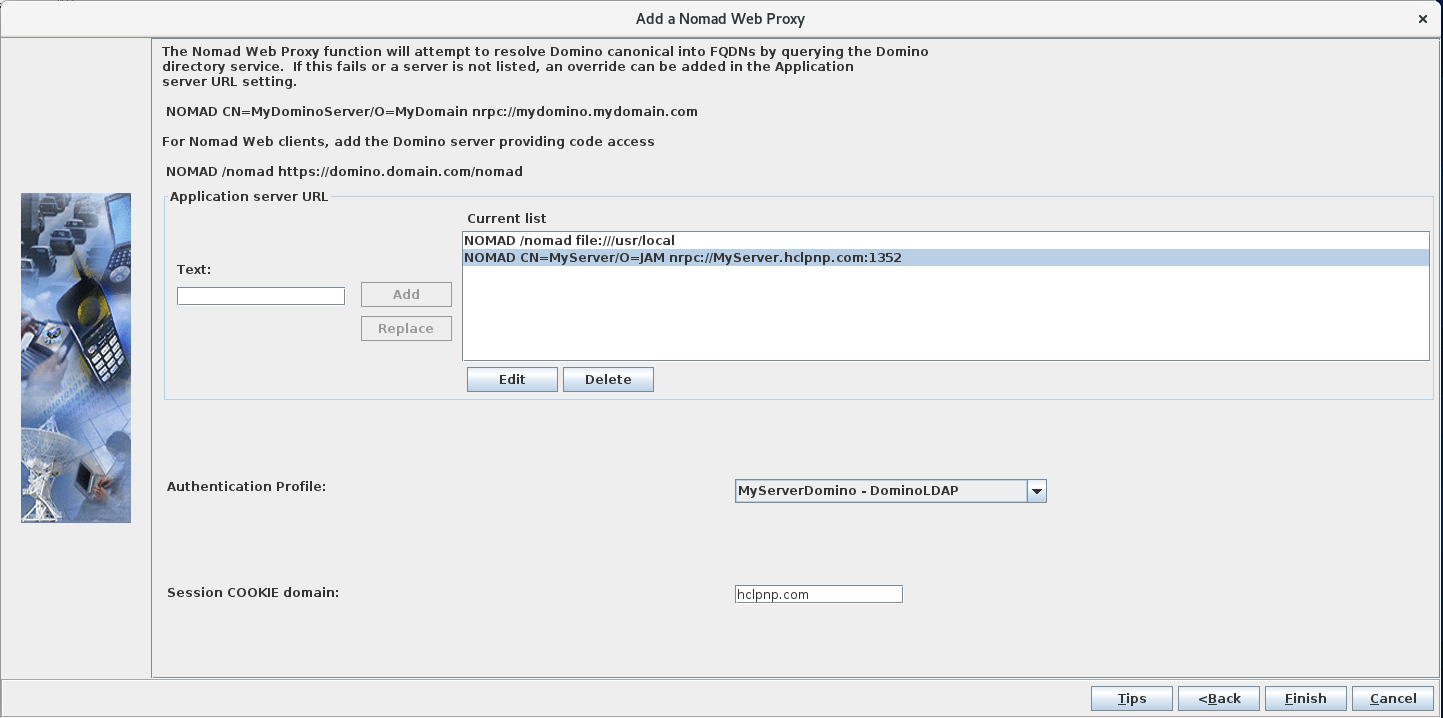
Configure the Nomad proxy:
-
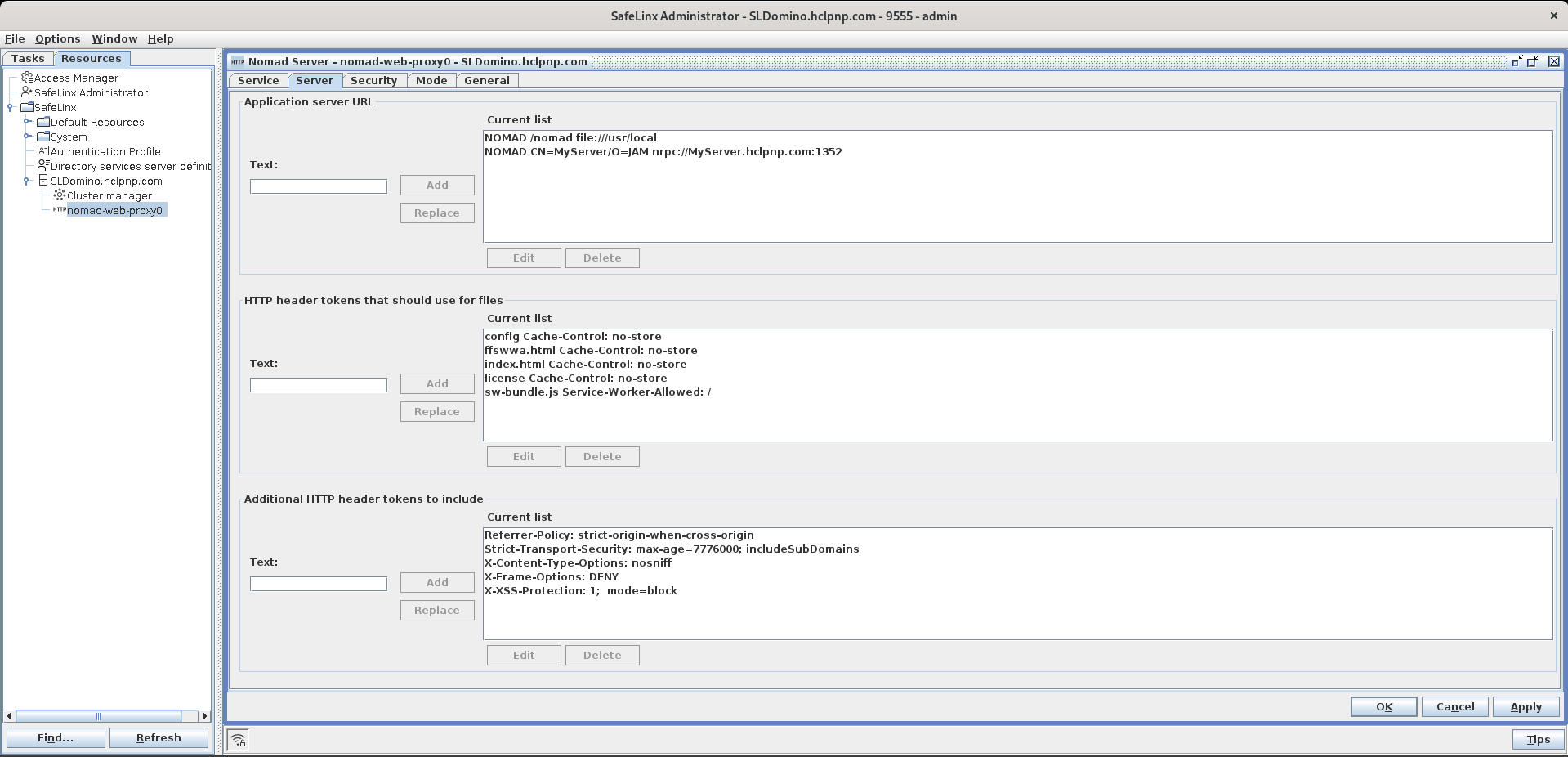
Configure HTTP response headers
In the SafeLinx Administrator Client, navigate to the Resources tab, expand the SafeLinx Server and then right-click on the Nomad Web Proxy you just configured. In the popup-menu, select Properties. In the window that opens, select the Server tab. Edit HTTP header tokens that should use for files to configure the required HTTP headers corresponding to the files and Additional HTTP headers to include sections to update the preconfigured optional HTTP headers (in all responses). For HTTP header tokens that should use for files, entries should include filename and headers token and should be separated by a space (' ').
-
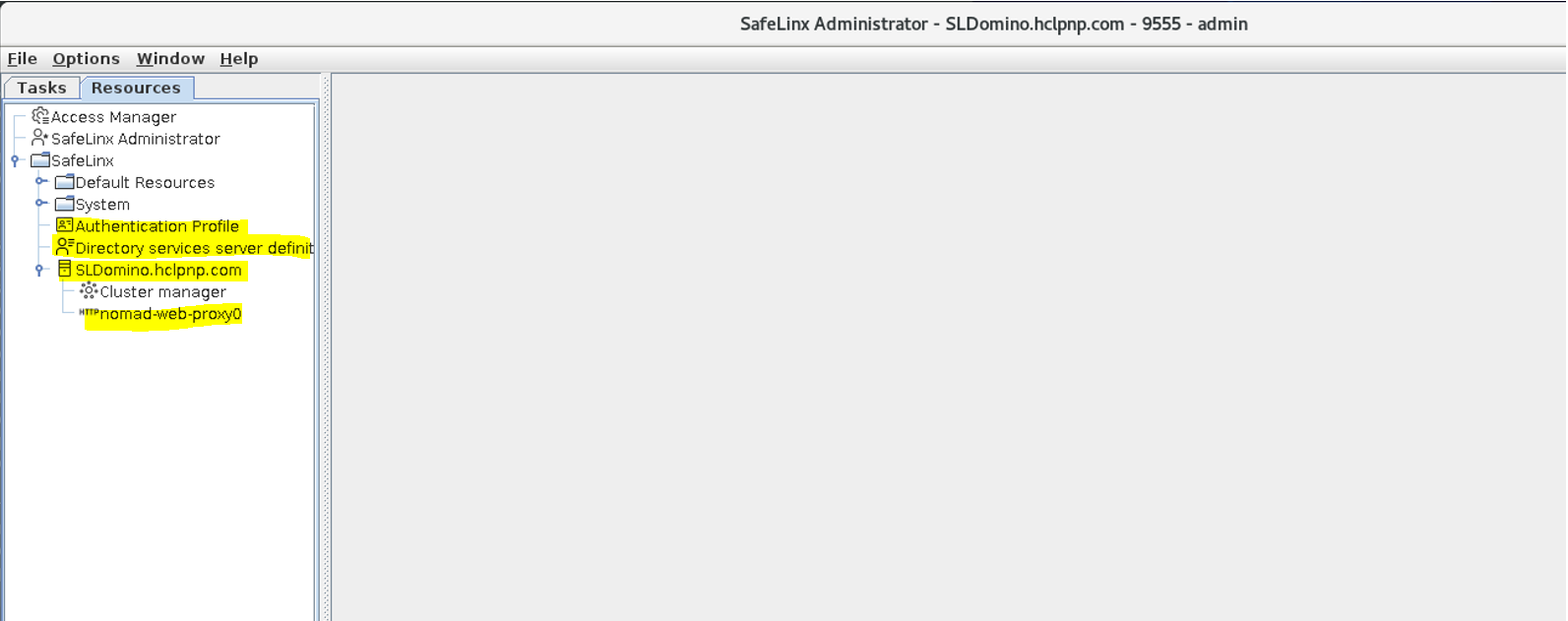
Confirm the configuration: