Access control lists (ACLs) and ACL Profiles
An access control list (ACL) is a table of access levels for all resource types per organizational unit (OU). An ACL profile is a collection of ACLs that you assign to administrators to define their level of access to resources.
Access control list (ACL) levels of access range from the lowest level of None through Read-only, Modify, Create, and up to the highest level All. You can create as many ACL profiles as you want and you can assign one profile to as many administrator IDs as you want.
When an administrator logs in to the SafeLinx Administrator, resources the administrator can access are displayed in the Resources tab. Tasks appropriate to the administrator are available in the Tasks tab and in resource task options.
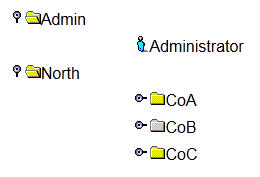
For example, as the super user administrator for the company BigNet, you administer a SafeLinx Server, which services the subsidiaries CoA, CoB, and CoC. In the organizational structure of the company, these three subsidiaries are considered part of the North region. SafeLinx Administrator represents the organizational relationship for the North region as a folder tree in which the parent folder, labeled North, opens to display child folders labeled, CoA, CoB, and CoC, as shown in the following diagram:

You need three BigNet administrators, one for each of the three companies. You create three administrator resources under an Admin primary OU for o=BigNet,c=US. The three administrators are represented by a single Administrator icon.
| Resource | Type | Access Level | Other |
|---|---|---|---|
| SafeLinx Server | Read | start=0, reset=0 |
|
| Mobile Device | Dial | Add | |
| Modem Profile | Read | ||
| Password Policy | Add | ||
| User | All | cbpwd=1, resetfl=1, lock=1 |
Then, you apply the ACL profile to the three administrators.
The following diagram show how SafeLinx Administrator represents the CoA organizational unit and its resources to the administrator of the CoA OU:

| Resource | Type | Access Level | Other |
|---|---|---|---|
| User | Read | chpwd=1, resetfl=0, lock=0 |
|
| SafeLinx Server | None | start=0, reset=0 |
|
| Mobile Device | None | ||
| Modem profile | None | ||
| Password profile | None |
The following diagram shows the organizational units and resources that SafeLinx Administrator displays to the password administrator:

To assign access levels to an admin ID for resources within an OU, first create an ACL profile, add ACLs to it, then assign it to the admin ID.
To add an ACL profile, from the Tasks pane or the Resources pane, right-click the OU in which you want to add the profile, then click . Follow the wizard instructions to name and describe the profile and select the organizational unit to which it belongs. After the ACL profile wizard is complete, you are prompted to add ACLs to the profile. Follow the wizard instructions to add the ACLs to the profile and define the access you want the admin to have.
Next, assign the ACL profile to the admin ID. Select the admin ID and click Properties. Click the Access type tab, then click Access control list. Select the ACL profile from the list, then click OK or Apply.
- For admins that are assigned an ACL profile, when you want them to manage a resource, give them access to that resource and grant separate access to all the resources needed to support that resource. For example, if they are managing users, give at least read-only access to resources like password policies so that they can assign a policy to the users.
- A transport profile is the only resource for which you cannot set an ACL. Instead, the transport profile inherits its ACL from the ACL setting for connection profile resources under that OU.