What changes from the BigFix user's perspective
From the BigFix user interfaces operator's perspective, this enhancement affects only authentication.
- LDAP operators:
- Must authenticate to the Web UI and to the Web Reports from the SAML identity provider only by
accessing the following URLs:
https://<WebUI_server>(for the Web UI server, assuming that it uses port 443)https://<Web_Reports_server>:8083(for each Web Reports server, assuming that port 8083 is used)Note: The buttons and links to log out from the Web UI and the Web Reports redirect these users to a page where they can click a Re-authenticate button to get back to Web UI and Web Reports pages without having to log back on, unless the IdP login timeout has expired; in this case they are brought back to the IdP login page. - Must enable the Use SAML authentication check box in the Console login panel, if the
BigFix server was configured to
integrate with SAML V2.0.
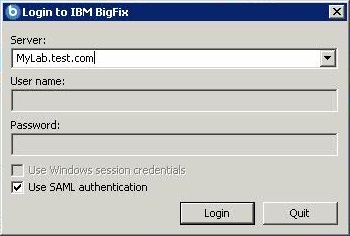 The selection is automatically validated and retained by BigFix for future login requests.Note:
The selection is automatically validated and retained by BigFix for future login requests.Note:- To override the The security certificate was issued by a company you have not
chosen to trust Windows Security Alert warning:
Install the BigFix certificate (known as ServerSigningCertificate_0 by default) in the Trusted People store of Windows.
- To override the The name on the security certificate is invalid or does not
match the name of the site Windows Security Alert
warning:
Starting from BigFix Platform 9.5 Patch 16, you can update the BigFix certificate (known as ServerSigningCertificate_0 by default) including an entry in the SubjectAltName field.
Or you can add an alias for the BigFix server IP address in the Windows 'hosts' file on the Windows computer in which the BigFix Console is installed and set it to the value of CN of the Subject name of the certificate (ServerSigningCertificate_0, by default) and use this alias in the Server field of the BigFix Console Login panel.
Ensure that the same name (for example, ServerSigningCertificate_0) is defined as SAML endpoint in your Identity Provider (for example, AD/FS or WebSeal) to garanteee that your BigFix Console login gets the authorization.
- To override the The security certificate was issued by a company you have not
chosen to trust Windows Security Alert warning:
- Must authenticate to the Web UI and to the Web Reports from the SAML identity provider only by
accessing the following URLs:
- Local non-LDAP operators:
- Log in to the Web UI or to the Web Reports by accessing the usual login
URLs:
https://<WebUI_server>/login(assuming that the Web UI is set on port 443)https://<Web_Reports_server>:8083/login(for each Web Reports server, assuming that Web Reports is set on port 8083) - Log in to the BigFix Console from
the usual login panel ensuring that the Use SAML authentication check box is not
selected.Note: If SAML is not enabled in the environment, the Use SAML authentication check box is greyed out.
- Log in to the Web UI or to the Web Reports by accessing the usual login
URLs:
After SAML is configured and enabled only local non-LDAP users will be able to log in using API; the 4-eyes authentication approvers must be local accounts.