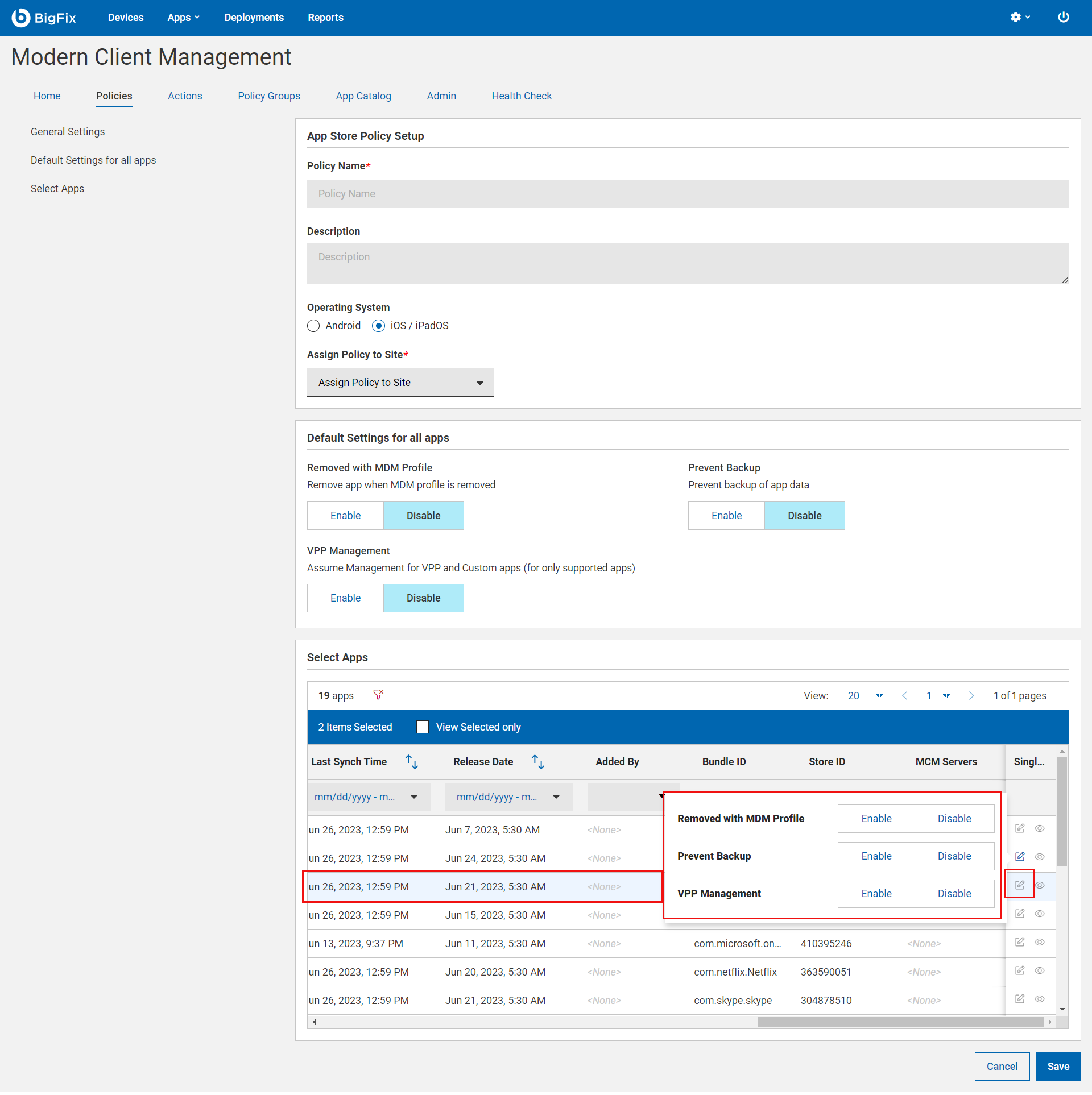
App Deployment Policy
BigFix MCM enables you to configure application policies to install applications from the App store on the Android, iOS, and iPadOS devices.
About this task
Creating an app deployment policy
To create an app deployment policy, perform these steps:
Procedure
- Log in to BigFix WebUI.
- Go to .
- Click Create Policy on the top right corner.
-
From the list of policy types, select App Deployment. The following page
appears.
- Under the General Settings section, enter app deployment Policy Name and Description.
- Select the Operating System.
- From the Assign Policy to Site drop-down, select the site.
-
Configure the operating system specific settings. You can set the permissions
globally for all the apps in the app policy. You can also set permissions for
individual app in the policy as required by selecting the app and clicking
 . You can see the settings set for an app on the fly
when you hover over the mouse on the
. You can see the settings set for an app on the fly
when you hover over the mouse on the  icon.
icon.
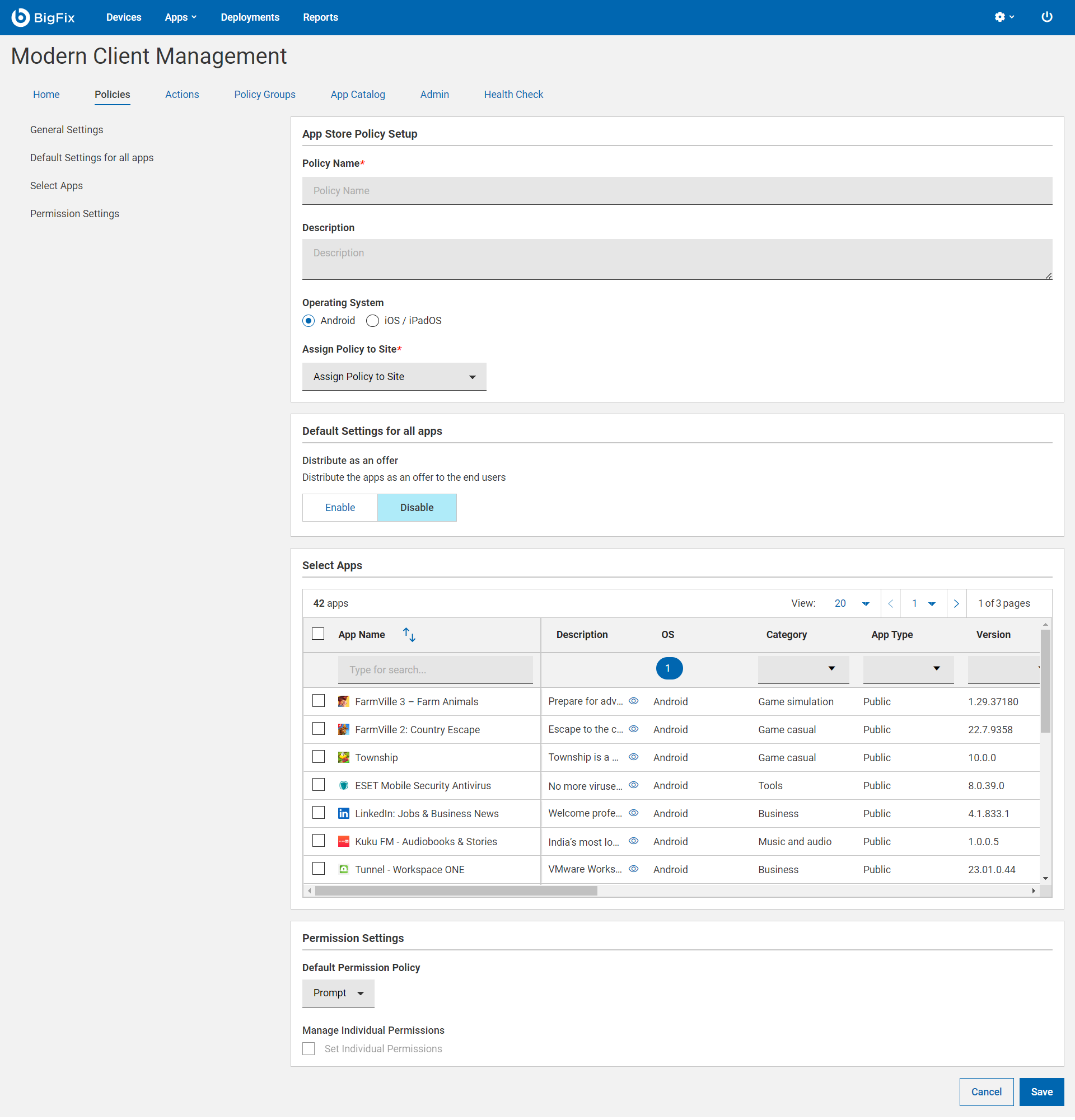
- Android
- Default Settings for all apps:
Distribute as an offer: If enabled, the apps become available for download or installation on Android devices through various methods, such as app marketplaces, websites, or direct distribution. Enable or disable the option to distribute the apps as an offer to the end users.
- iOS/iPadOS
- Default Settings for all apps: The permission
set as Default Settings is applicable globally for all the
applications that are installed through the app policy.
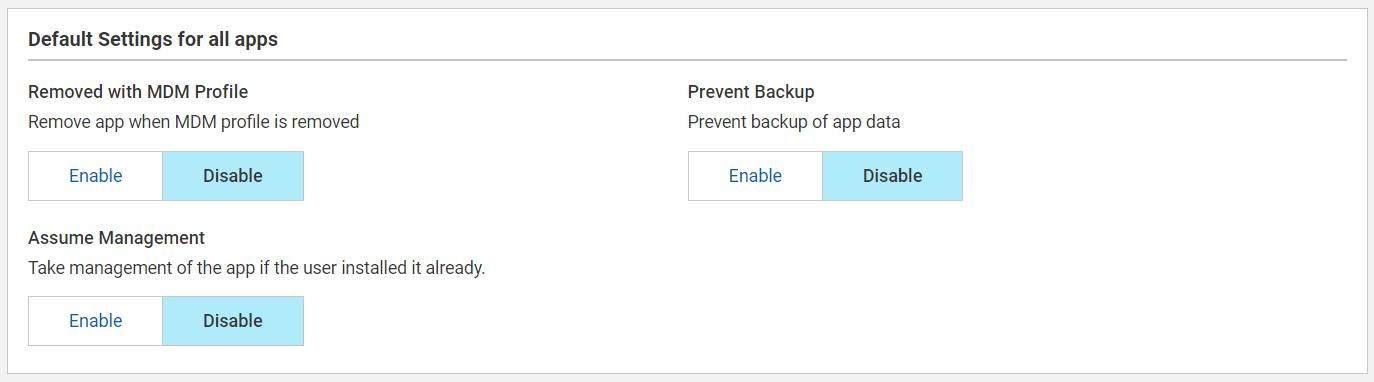
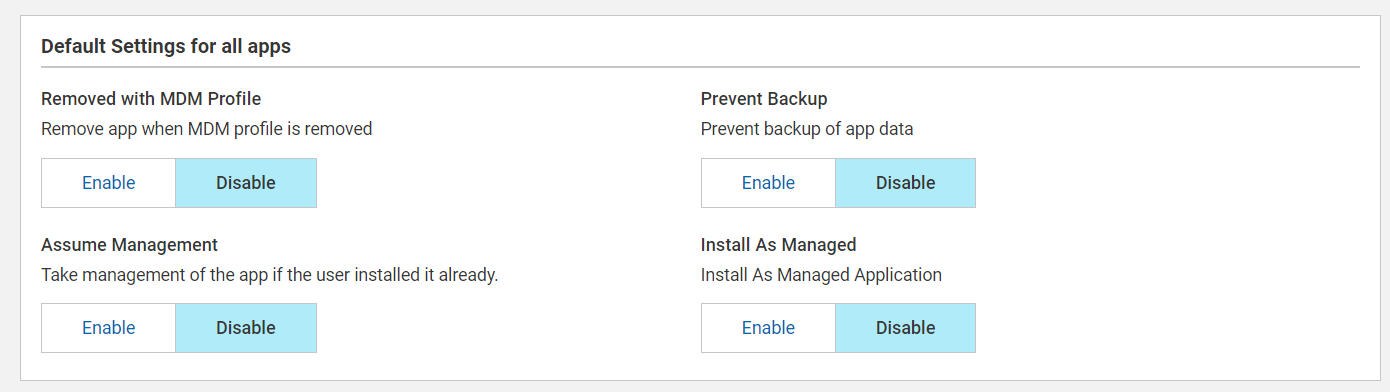
- Removed with MDM Profile: Enable this setting if you want to remove the app when MDM profile is removed.
- Prevent Backup: Enable this setting to prevent backup of app data.
- Assume Management: If enabled, once
the MDM profile is installed, the device "assumes
management." This means that BigFix can now manage the
device's settings, security policies, app installations, and
other configurations.Note: This option is applicable only for VPP apps. Enable this setting for delivering apps to supervised Apple devices only. Do not select this option if the app is to be delivered to an Apple user enrolled device, as that option is not allowed for BYOD enrollments. For more information, see Known limitations.
- Install As Managed: If enabled,when the app configuration profile is applied to the devices, the apps are installed as "Managed" on those devices. That means, IT administrators can install and manage the apps specified in the policy. IT admins can remotely deploy and install applications on macOS devices; push specific configuration settings and preferences to the application; enforce security policies, compliance requirements, and access controls; track application usage; gather data for reporting; and perform troubleshooting or updates as needed; install updates and patches of the apps; remove the apps from devices when necessary.
- Select apps: This grid lists all the apps added to the app catalog. Select the desired app and configure settings as needed.
- Click Save.
Results
When the policy is deployed, the device receives a notification that a set permission or action is being performed on the device by the device manager. The permission manager in the device shows the permission that are applied.