Configuring HCL Campaign in SSL and HCL Campaign Listener in non-SSL
If your setup has HCL Campaign in SSL and the HCL Campaign Listener in the non-SSL mode, you must configure settings for the applications to work seamlessly.
Before you begin
About this task
All configurations are applicable to the WebSphere Application Server for HCL Campaign. Multiple steps are involved to configure the SSL and non-SSL setup. Each step might have more substeps to be completed.
Procedure
To configure HCL Campaign in SSL and HCL Campaign Listener in non-SSL, complete the
following steps:
Complete the following steps.
| # | Step | Substeps |
|---|---|---|
| 1 | Generate keystore database files for the Listener server. | Run the following commands from and location and note the
paths.The following files are generated at the location from where you ran the commands. 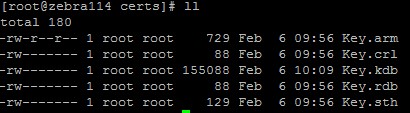 |
| 2 | Import the Key.arm file into the application server where the Campaign web application is deployed. |
The listener key is added to the application server. |
| 3. | Extract Personal and Signer certificates from the HCL Campaign WebSphere Application Server. |
The ClientPersonal.cer and ClientSigner.cer certificates are generated in the path that you provided. |
| 4 | Import the Personal and Signer certificates into the listener keystore database. |
|
| 5 | Modify config.xml file on the listener server. | Provide the following information:
|
| 6 | In the unicaACListener settings set useSSL to TRUE. | - |
| 7 | Restart the Campaign Application Server and the Campaign Listener. | - |