Security planning for extranet access
Make your Sametime® deployment secure in the extranet for customers, clients, or employees who are mobile. Sit down early with your Security and Network teams early to plan extranet access. Consider security best practices.
There is no "one size fits all" deployment scenario for extranet users. The way you deploy Sametime will determine which Sametime ports to use, which WebSphere® Application Server ports to use, and which ports to open in the firewalls.
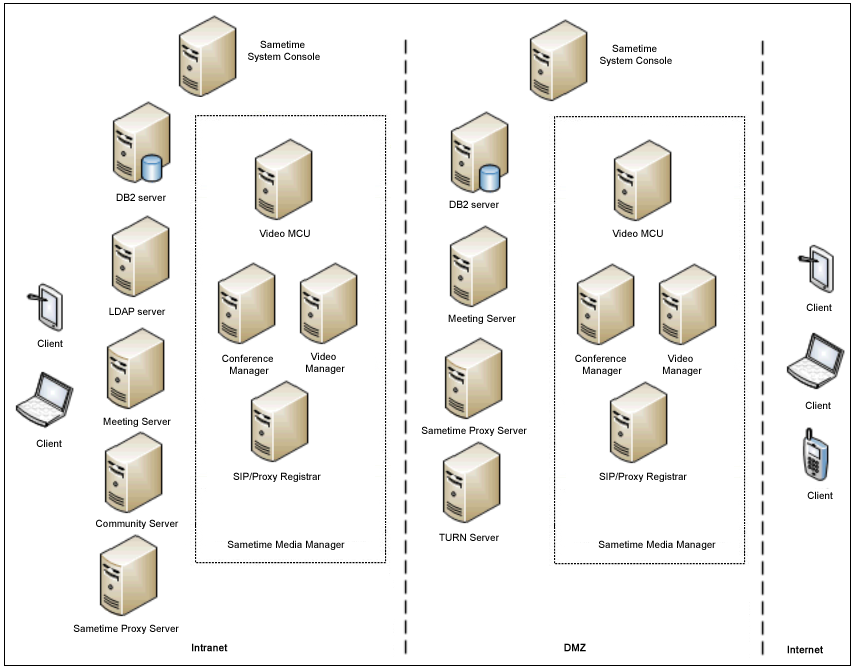
Secure deployments use two firewalls, which define three security zones. The inner firewall isolates the organization’s intranet (the most secure zone), and the outer firewall creates a DMZ between the intranet and the Internet (the least secure zone). Deployment of Sametime is always dependent on your company's security requirements, capacity, and the features you want to install. If you want to allow users within your organization to meet only with external users connecting from the Internet, then you would install a Sametime Meeting Server outside the inner firewall so that it resides in the DMZ.
- LDAP access
- Can servers in the DMZ access the internal LDAP?
- Does your LDAP support guest accounts?
- Can an LDAP server exist in the DMZ?
- DB2® access
- Can servers in the DMZ access the internal DB2 hosts?
- Can a DB2 server exist in the DMZ?
- Are there any restrictions on opening ports from the DMZ to the intranet?
- Use of Internet Control Message Protocol (ICMP)? Ping is used by the Installation Manager and Deployment Plans to confirm presence of servers and host names
- Use SSL for web traffic for secure connections:
- Use the firewall or other boundary device to force traffic to SSL
- Use WebSphere HTTP Proxy Server redirect rules
- Use Transport Layer Security (TLS) for Media Manager traffic:
- Requires additional configuration
- Make sure TCP option is working first, then make the switch to TLS
- If you have cells deployed in the DMZ, consider the following:
- Be sure to enable security to prevent unauthorized access to the administration console
- The Deployment Manager server is not required for runtime of the servers
- Consider using reverse proxies for extra security.
- Meeting Server is HTTP compliant
- Sametime Proxy Server is HTTP compliant
- Sametime supports encrypted access to DB2. For information, see the Tech Note How do I enable SSL encryption for DB2 Connections for WebSphere-based applications and datasources?
- Sametime supports the IBM® Security Access Manager WebSEAL reverse proxy server
- Sametime supports CA Single Sign-On (formerly CA SiteMinder)
- The Sametime TURN
Server enables Sametime clients
to send audio/video communications across a NAT or firewall when direct
peer-to-peer communications are not possible. The TURN Server implements
the TURN (RFC 5766) and STUN (RFC 5389) protocols and performs two
main functions:
- Assists the client (using ICE, RFC 5245) in finding its public address
- Provides an extension, or relay, to the client.
- The client uses the TURN Server as a relay to send packets to these peers and to receive packets from the peers when peer-to-peer communication is not possible. Sametime clients connect to the TURN Server using UDP or TCP. The TURN Server keeps a list of permissions that consist of an IP address and an associated time-to-expiry. While permission exists, all peers using the IP address in the permission list are allowed to send data to the client.
- Sametime System Console
- DB2
- Sametime Media Manager
- Sametime Meeting Server
- Sametime Proxy Server
- LDAP
- Sametime Community Server
- Sametime System Console
- DB2
- Media Manager
- Meeting Server
- Sametime Proxy Server
- Community Server