Firewall issues
A sample topology of a SafeLinx Server installation might contain two firewalls. The firewalls are used to block all unwanted connections from the Internet and from the intranet. Enable only known connections to and from the SafeLinx Server in the firewalls.
Your enterprise might deploy a firewall between the carrier network and the SafeLinx Server. In this case, the MNC port must be opened on the firewall.
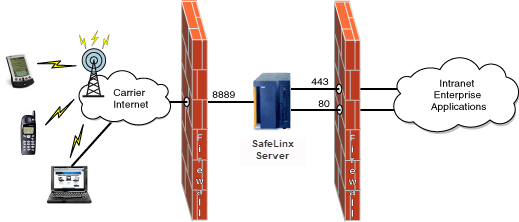
Data flow through a network shows how an enterprise might deploy firewalls that use a single User Datagram Protocol (UDP) MNC. For example, you might deploy a firewall between the SafeLinx Server and its backend applications. If the backend applications require access for traffic that use port 80 or 443, make sure that the appropriate firewall ports are opened. Make sure port 8889 for the MNC is opened on the firewall if one exists between the SafeLinx Server and the carrier network. Also, the mobile computer on which the SafeLinx Client is installed might have a personal firewall. Make sure that the firewall allows access to the Internet for the SafeLinx Client program.
If your network uses a dynamic host configuration protocol (DHCP) server, make sure it located inside the DMZ between the firewalls.
The IP addressing inside DMZ between the firewalls depends on your network topology. You can have private, non-routable IP addresses, in which the firewall provides network address translation (NAT) to substitute the IP address of the SafeLinx Server. In this case, virtual machines outside the DMZ, such as SafeLinx Clients or enterprise applications would use the IP address of the firewall and the firewall would substitute the private, non-routable IP address for traffic destined to the SafeLinx Server. The backend firewall might or might not be one that your enterprise uses.
If you use remote servers for persistent data storage, then where you place them also plays a part in your network topology. If you locate your directory service server (DSS) or relational database (RDB) servers outside the DMZ, then they too might use substituted NAT addresses when connecting with the SafeLinx Server. Understanding these firewalls, NAT, and routing issues is required when setting up your network topology.
| Port number | Component that uses the port | Internet (external) firewall or enterprise (back-end) firewall |
|---|---|---|
| 443 | Secure HTTP service | Internet |
| 9555/9559 | Remote non-secure/secure SafeLinx Administrator | Internet |
| 53 | DNS servers | Enterprise |
| 80/443 | HTTP/HTTPS access to application servers | Enterprise |
| 389/686 | Non-secure/secure LDAP server | Enterprise |
| 1433 | Microsoft SQL Server | Enterprise |
| 3306 | MySQL | Enterprise |
| 9610 | RADIUS authentication server | Internet/Enterprise |
| 50000 | IBM DB2 | Enterprise |
| Port number | Component that uses the port | Internet (external) firewall or enterprise (back-end) firewall |
|---|---|---|
| 80/443 | TCP based Mobile Network Connections (MNCs) | Internet |
| 9555/9559 | Remote non-secure/secure SafeLinx Administrator | Internet |
| 53 | DNS servers | Enterprise |
| 80/443 | HTTP/HTTPS access to application servers | Enterprise |
| 389/686 | Non-secure/secure LDAP server | Enterprise |
| 1433 | Microsoft SQL Server | Enterprise |
| 3306 | MySQL | Enterprise |
| 9610 | RADIUS authentication server | Internet/Enterprise |
| 50000 | IBM DB2 | Enterprise |
To limit the external networks that have connectivity, you can either configure appropriate rules on your external firewall, or specify static routing paths for the appropriate subnets. In this configuration, set the default route of the virtual machine to something other than the Internet-facing adapter.