SAML federated identity provider configuration enhancements
Active Directory Federation Services (ADFS) 4.0 and the industry-standard SAML 2.0 AuthnRequest are now supported. In addition, the IdP Catalog (idpcat.nsf) design has been improved to simplify the steps to configure Domino® to use a SAML federated identity provider. To take advantage of these enhancements, replace the design of your IdP Catalog with the Domino® 10 idpcat.ntf template.
- Protocol version
- Federation product. If your identity provider is ADFS 4.0, this value is set to AuthnRequest SAML 2.0 compatible.
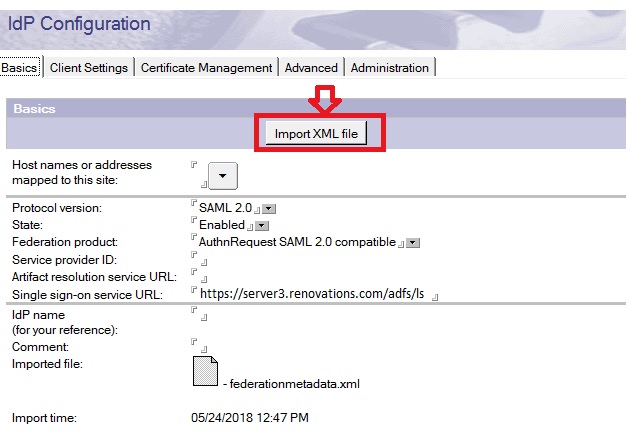
The Host names or addresses mapped to this site field is populated from the HTTP host names in the Domino® directory Server document or Web site document, when possible. A drop-down arrow is also available for you to open the Domino® directory.
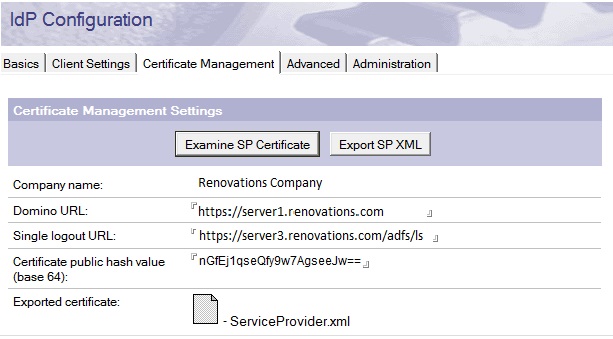
The identity provider uses the Domino® certificate for two purposes in this release: to encrypt SAML assertions that it sends to Domino® and to sign AuthnRequests that it receives from Domino® if it support AuthnRequests.
For more information, see Using Security Assertion Markup Language (SAML) to configure federated-identity authentication.