Configuring Compass for LTPA SSOv2
Compass can be configured to use the identity information provided by LTPA cookies, and IBM® WebSphere® can be configured to perform authentication of the user based on a configured federated or non-federated user repository (for example, an LDAP directory).
Lightweight Third-Party Authentication (LTPA) is a method for web application to share identity information using a cookie on the browser. The cookie is encrypted using shared keys that are shared between the WebSphere profiles that are running the applications that need the identity information.
Setting up LTPA Between WebSphere Servers
WebSphere documentation describes how to configure two WebSphere servers to share LTPA. In summary, each WebSphere profile must use the same user registry and LTPA cookie name, and must be in the same domain (for example, *.hcl.com). By default, the LTPA cookie is LtpaToken2, but if you change this you have to change each WebSphere server to use the same cookie name.
Note: If Compass does not work with a federated user registry set up, use a Standalone LDAP registry.
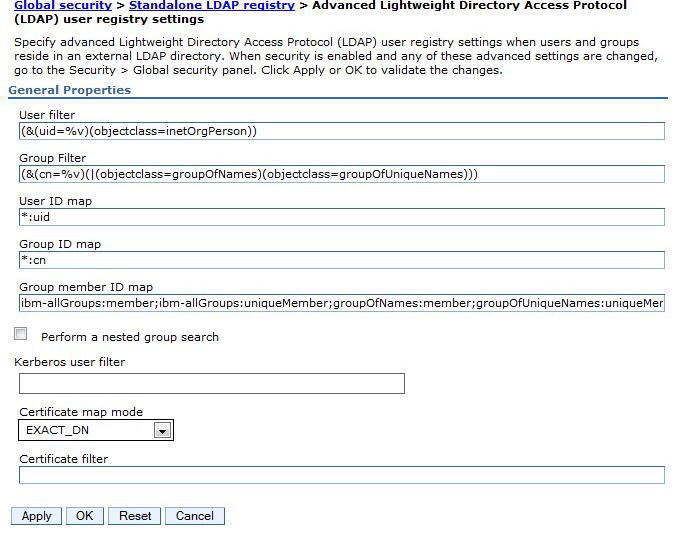
Ensure that the advanced settings for the LDAP registry can find the users you plan to log in as. The following illustration shows an example of a set of advanced settings. Your configuration might require different settings.
Compass SSO Setup
Compass configuration for SSO follows almost the same directions as in the help topic Configuring strong authentication with smart-cards.
- Configure Compass database for SSO.
- Configure Compass Web server for SSO.
- Map LTPA/LDAP users to Compass Web application.
- You must set an SSO password in the database. See the procedure in help topic Configuring HCL Compass databases for container authentication.
- Create an sso.properties file using cqrpc/cqrpc.exe and the password you used in step 1. See the procedure in help topic Configuring Compass Web server for container authentication.
- Configure the sso.properties file for LTPA. See the procedure in help topic Configuring the Compass Web client for container authentication.
Configure Compass Web server for SSO
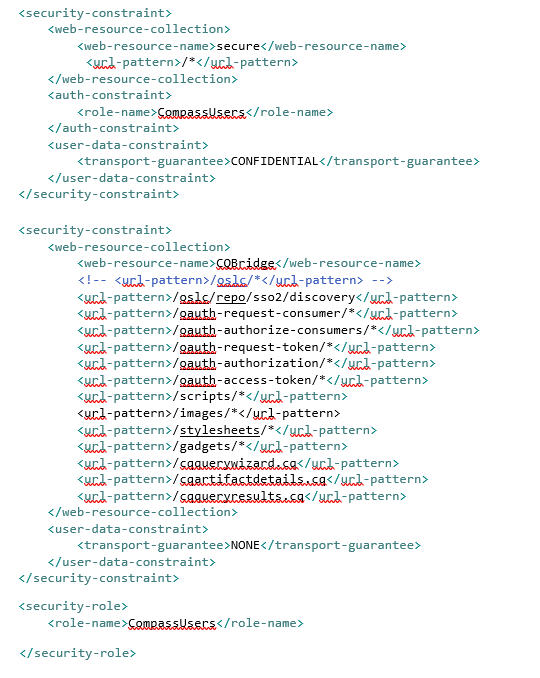
Reference the help topic Configuring client certificate authentication for Compass Web to modify the web.xml descriptor, but for the security constraint and other clauses in web.xml use this:
Map LTPA/LDAP users to Compass Web application
Compass Web must be told which users can access the Compass Web application. You can either tell Compass Web that all authenticated users can access the Compass Web application or choose specific groups or users that can access the application. Just accessing the application does not mean they can actually log in to Compass Web, it only means that they can load the Compass Web resources in their browser. Whether they can actually log in to a Compass database depends on whether the user is already subscribed to the Compass database. For example, if the user “tom” is allowed access to the Compass Web application but does not have any access to a Compass database, they will probably only see the database selection dialog but will not be able to actually connect to the database.
The LTPA/LDAP users of the Compass Web application, see the procedure in the help topic Mapping users to LDAPgroups.
As an alternative, you can also map CompassUsers to “all authenticated users” or “all authenticated users in trusted realms.”