Integrating the Windows server with Active Directory
To add an existing Active Directory to the console, follow these steps:
- From the Tool menu, select Add LDAP Directory. The Add LDAP Directory
dialog displays.
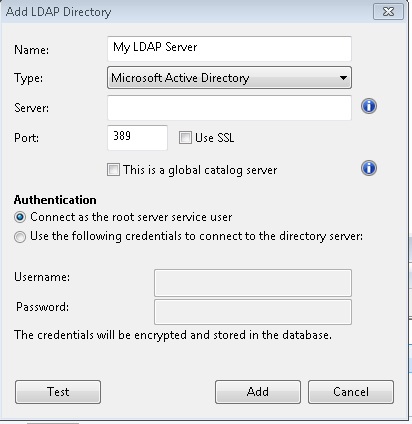
- Provide a name for the Active Directory and from the Type pull-down, make sure Microsoft Active Directory is selected.
- Under Server, enter the host name, IP Address or fully qualified domain name of the server.
- Click Use SSL if you want to configure a secure connection (SSL).
- To access an entire Active Directory forest, click This is a global catalog server.
- Click the button to connect as the root server service user or to use credentials. If you choose to connect using credentials, enter your Active Directory Username and Password.
- Click Test to make sure you have entered your information correctly and a connection can be made to your Active Directory server.
- Click Add to complete the Active Directory setup.
Note: When you add an LDAP Server as Microsoft Active Directory, ensure that on the LDAP
server you have defined the
UserPrincipalName attribute corresponding to the
User logon name of each user. This attribute value is used on the BigFix Console for each
user authentication.Your Active Directory Server is now configured and available for use in the console.
AD Domain/Forest Function level for BigFix Server running on Windows only
BigFix 9.5.19 is fully supported in an AD Domain/Forest Function environment with SSL in the following configuration:
- BES Server must be running on Windows only.
- Active Directories Windows 2016 defined with 2016 Domain Functional Level and with patch level updated.
- Every Active Directory installed with Global Catalog.
- Enterprise Certification Authority installed on root domain.
- Creation of a certificate for the CA with the following characteristics:
- In an AD forest with various domain extension (for example BIGFIX.ACME.COM for
root domain and CHILD.BIGFIX.ACME.COM for child domain) consider the common part of
domain name and create a certificate having a common name that starts with "*" (for
example):
CN = *.BIGFIX.ACME.COM - Then, on same certificate, define the DNS and list all AD servers, so the created
certificate will have on the Details tab the field "Subject Alternative Name" with
the values (for
example):
DNS Name=MyRootAD.BIGFIX.ACME.COMDNS Name=MyChildAD.CHILD.BIGFIX.ACME.COM
- In an AD forest with various domain extension (for example BIGFIX.ACME.COM for
root domain and CHILD.BIGFIX.ACME.COM for child domain) consider the common part of
domain name and create a certificate having a common name that starts with "*" (for
example):
The certificate must be loaded on All Active Directories of the SAN list.
The scenario was certified with DNS installed on the Active Directories.