Adding Active Directory
You can use Microsoft Active Directory (AD) to handle authentication on IBM BigFix. That allows you and other users to log in
to the console using your Active Directory credentials, taking advantage of your existing
authentication policies. The same advantage applies also to Web Reports.
Note: To integrate the Linux
BigFix server with Active Directory you
must configure the Kerberos protocol, downloaded as a prerequisite with the Linux BigFix server installation. For additional
information, see the Integrating Linux Server with Active Directory.
Starting from BigFix Platform Version 9.2 Patch 19, integration with Active Directory that is configured with LDAP channel binding and LDAP signing is supported.
To add an existing Active Directory to the console, follow these steps:
- From the Tool menu, select Add LDAP Directory. The Add LDAP Directory dialog appears.
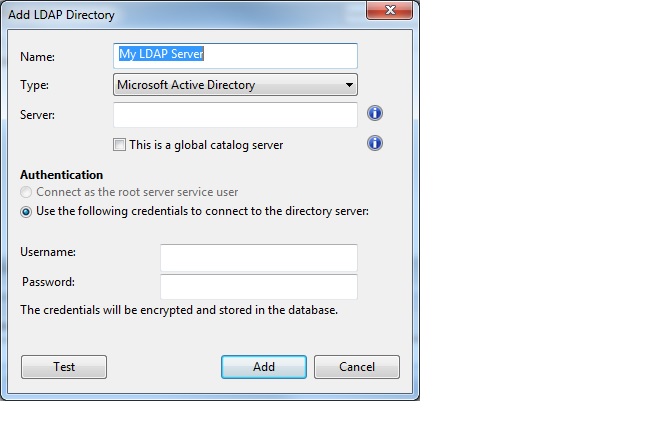
- Provide a name for the Active Directory and from the Type pull-down, make sure Microsoft Active Directory is selected.
- Under Server, enter the host name, IP Address or fully qualified domain name of the server.
- To access an entire Active Directory forest, click This is a global catalog server.
- Click the button to connect as the root server service user or to use credentials. If you choose to connect using credentials, enter your Active Directory Username and Password.
- Click Test to make sure you have entered your information correctly and a connection can be made to your Active Directory server.
- Click Add to complete the Active Directory setup.
Note: When you add an LDAP Server as Microsoft Active Directory, ensure that on the LDAP
server you have defined the
UserPrincipalName attribute corresponding to the
User logon name of each user. This attribute value is used on the BigFix Console for each
user authentication.Only when Active Directory is running over SSL, you must perform the following steps:
- Select Generic LDAP Server as server type and leave “Use SSL”
selected.
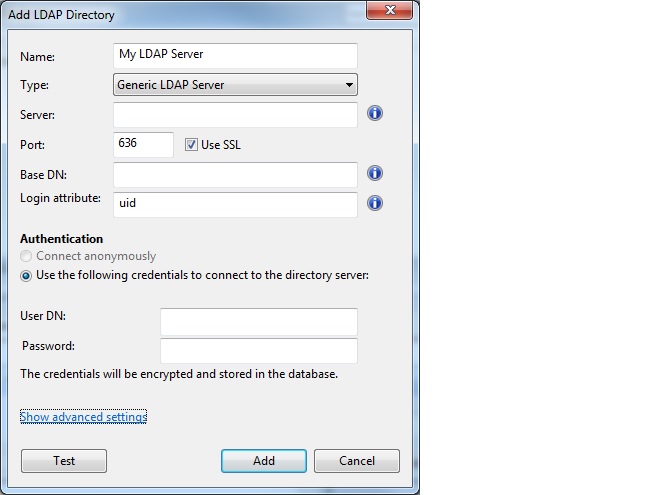
- If the server is a global catalog server, specify as port number
3269. - Click the Show advanced settings link. The user filter and group
filter options are displayed:
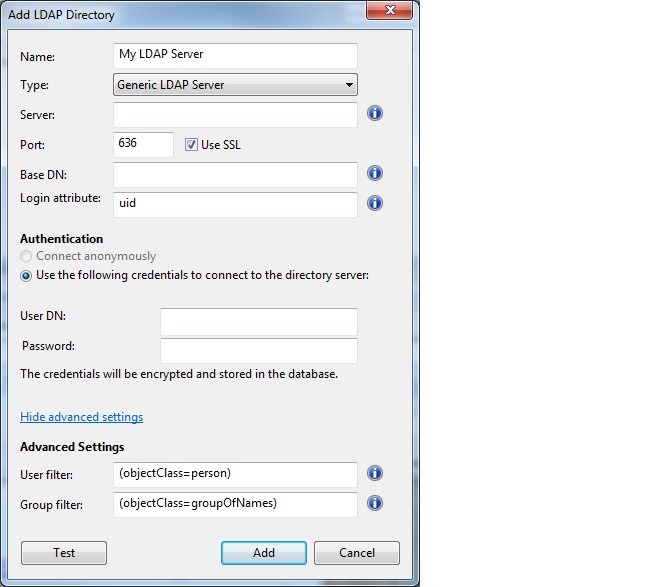
- Enter
UserPrincipalNamein Login attribute.Note: TheUserPrincipalNameattribute cannot be one of the following formats:domain/user,domain.com/user, oruser. - Enter
(objectClass=user)in User filter - Enter
(objectClass=group)in Group filter. - Click Use the following credentials to connect to the directory server and enter your Active Directory Username and Password.
- Click Test to ensure you have entered your information correctly and a connection can be made to your Active Directory server.
- Click Add to complete the Active Directory setup.
Your Active Directory Server is now configured and available for use in the console.
