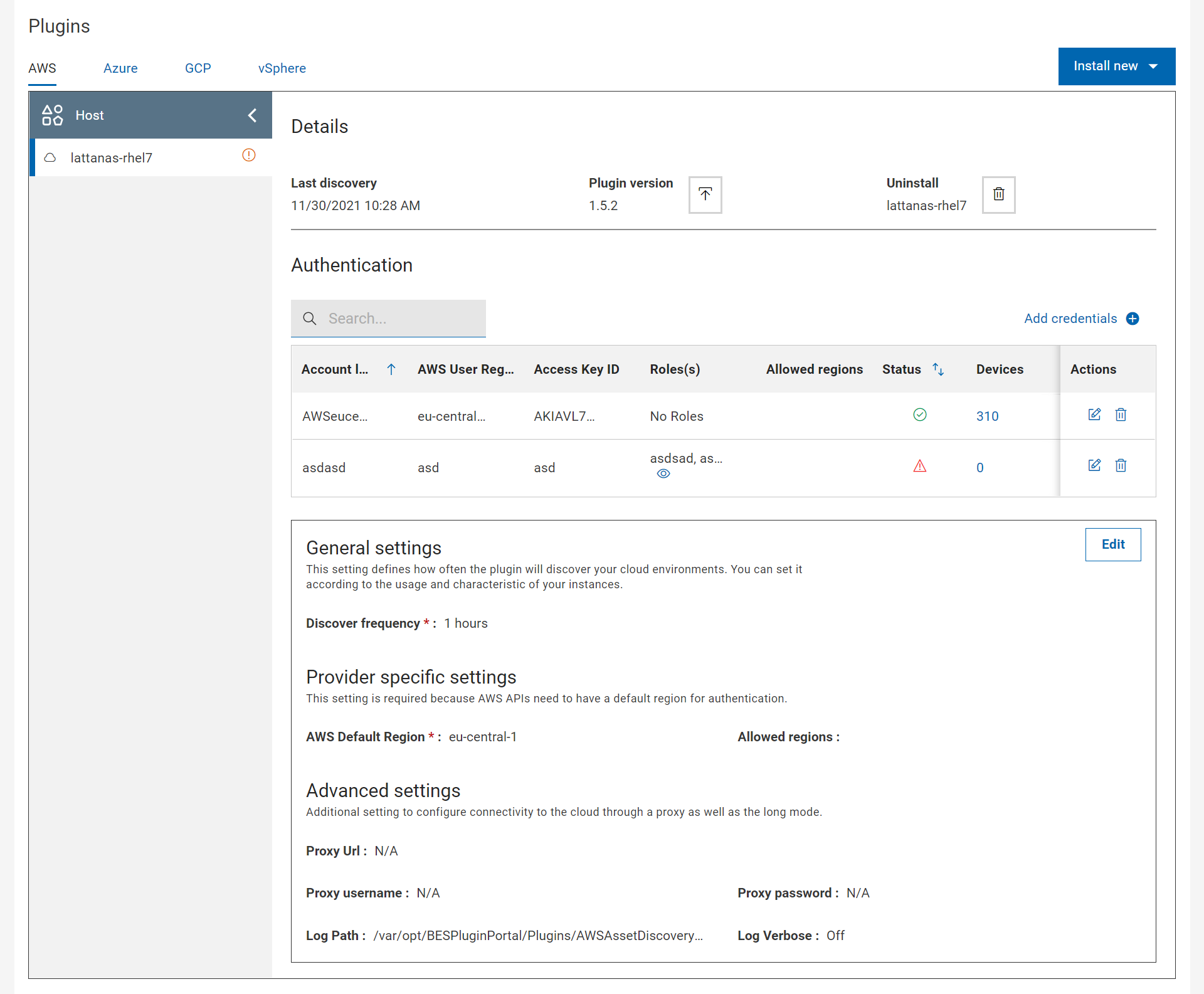
Limit AWS Regions to restrict the scope of device discovery
AWS organizes the data centers and virtual instances by region. This property of a
cloud instance is reported in AWS Region by the Amazon Web Services
Resources analyses.
AWS Region
An AWS Region is a collection of AWS resources in a geographic area. The resources that you create in one Region do not exist in any other Region unless you explicitly use a replication feature offered by an AWS service. When you enable a Region, AWS performs actions to prepare your account in that Region. For more information, see the AWS official documentation at https://docs.aws.amazon.com/general/latest/gr/rande-manage.html
Limit scan regions
For faster discovery, it is recommended to limit scanning only the AWS regions that you use. If not specified, after logging into the cloud environment, discovery is performed to all the AWS managed regions retrieved in the login phase, regardless of the authority that the additional credentials defined in the plugin have for the various regions.
For example, if the IAM User credentials specified at plugin install time have
authority only to access us-west1 region, when the plugin logins,
it tries to retrieve all the AWS account managed regions and starts the discovery.
At this point, the AWS plugin tries to use the IAM User credentials to login to all
AWS managed regions. This causes failed logins as the credential is not authorized
to access any regions other than us-west1.
BigFix Platform 10.0.5 introduces the possibility to limit the regions that are used for discovery through the parameter Allowed regions. If specified, it restricts the scope of the discovery, optimizing the network traffic and minimizing errors.
You can customize Allowed region setting by editing the AWS settings or by adding new AWS credentials.
| Applicability | Parameter name | Used for | What if not used? |
| PLUGIN |
AWS Default region * |
Login (to open the session through API) |
MANDATORY at install time |
|
Allowed regions (1) |
Narrows down the scope of the plugin discovery by listing the only regions where the discovery should run among the complete list of entitled regions for the users |
Discovery spans every managed region |
|
| ACCOUNT LABEL |
AWS User region (Regions for account label) |
Login and, if specified, overrides AWS Default region |
AWSDefaultregion Is used instead |
|
Allowed regions (for account label) |
Overrides Plugin Allowed regions(1) if present Narrow down the scope of the account discovery by listing the only regions where the discovery should run among the complete list of entitled regions for the users |
Plugin Allowed regions(1) is used |
|
|
Region (Role region) |
Used for login and it overrides AWS User region and AWS Default region in cascade |
AWS User region or in cascade AWS Default region is used |
Limit AWS Regions at plugin level
- Click the AWS tab.
- In the Plugin Management page, edit the plugin
General settings
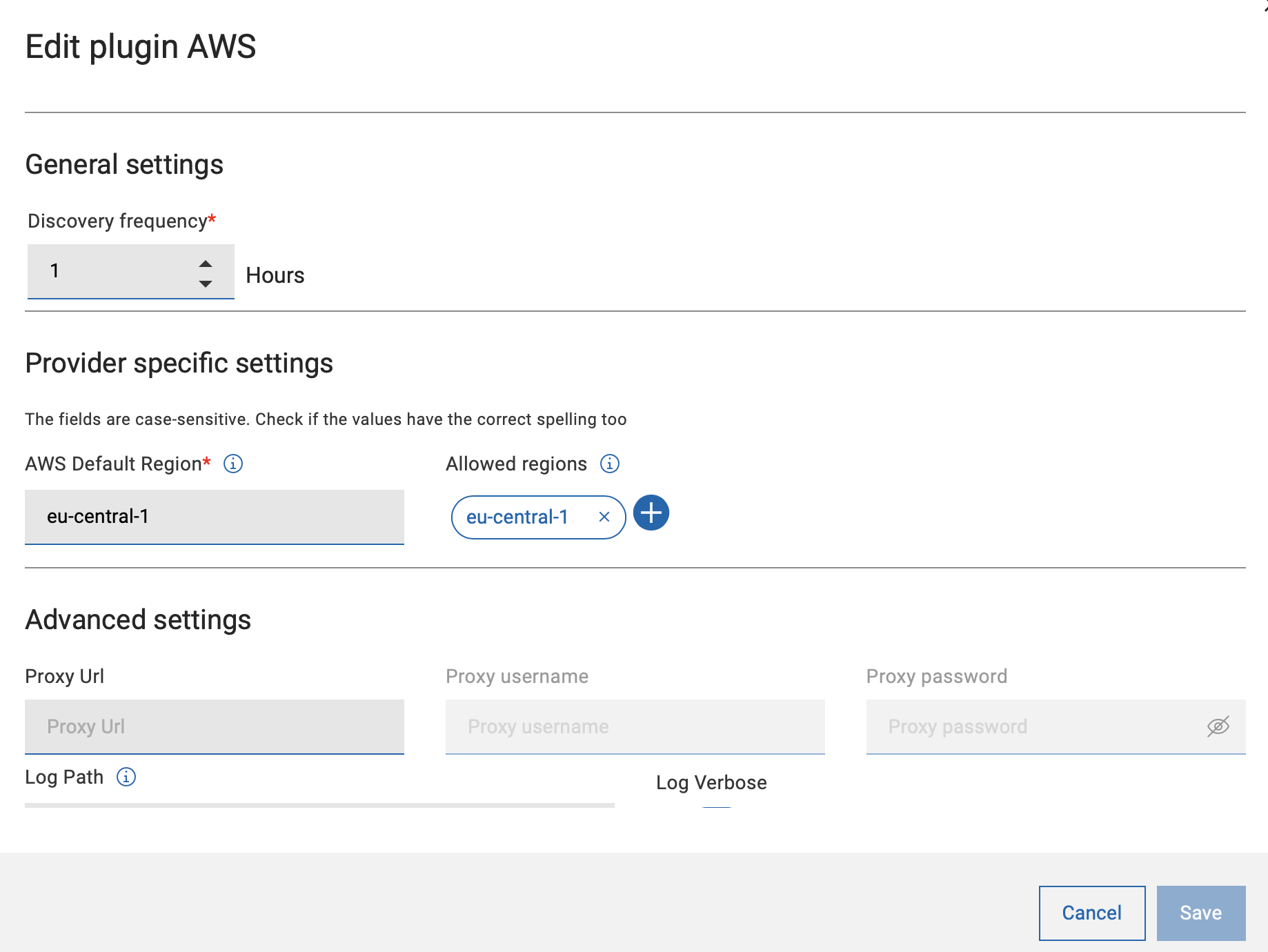
.- Add one or more regions to limit the discovery. The added regions
are listed as pills.Important: Enter the correct spelling for the region names, because BigFix cannot check the name of the region for correctness. Refer name and code of AWS Regions.
- You can also remove a region easily.
- Add one or more regions to limit the discovery. The added regions
are listed as pills.
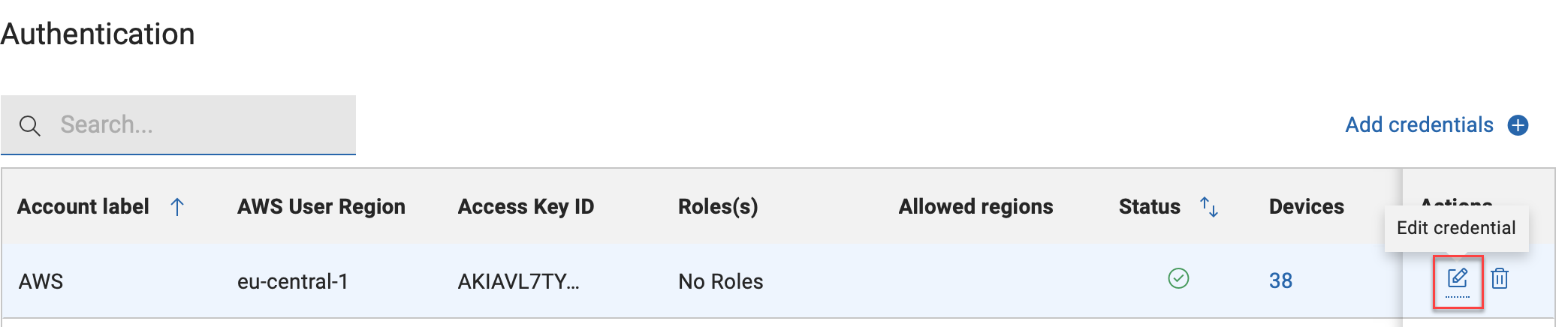
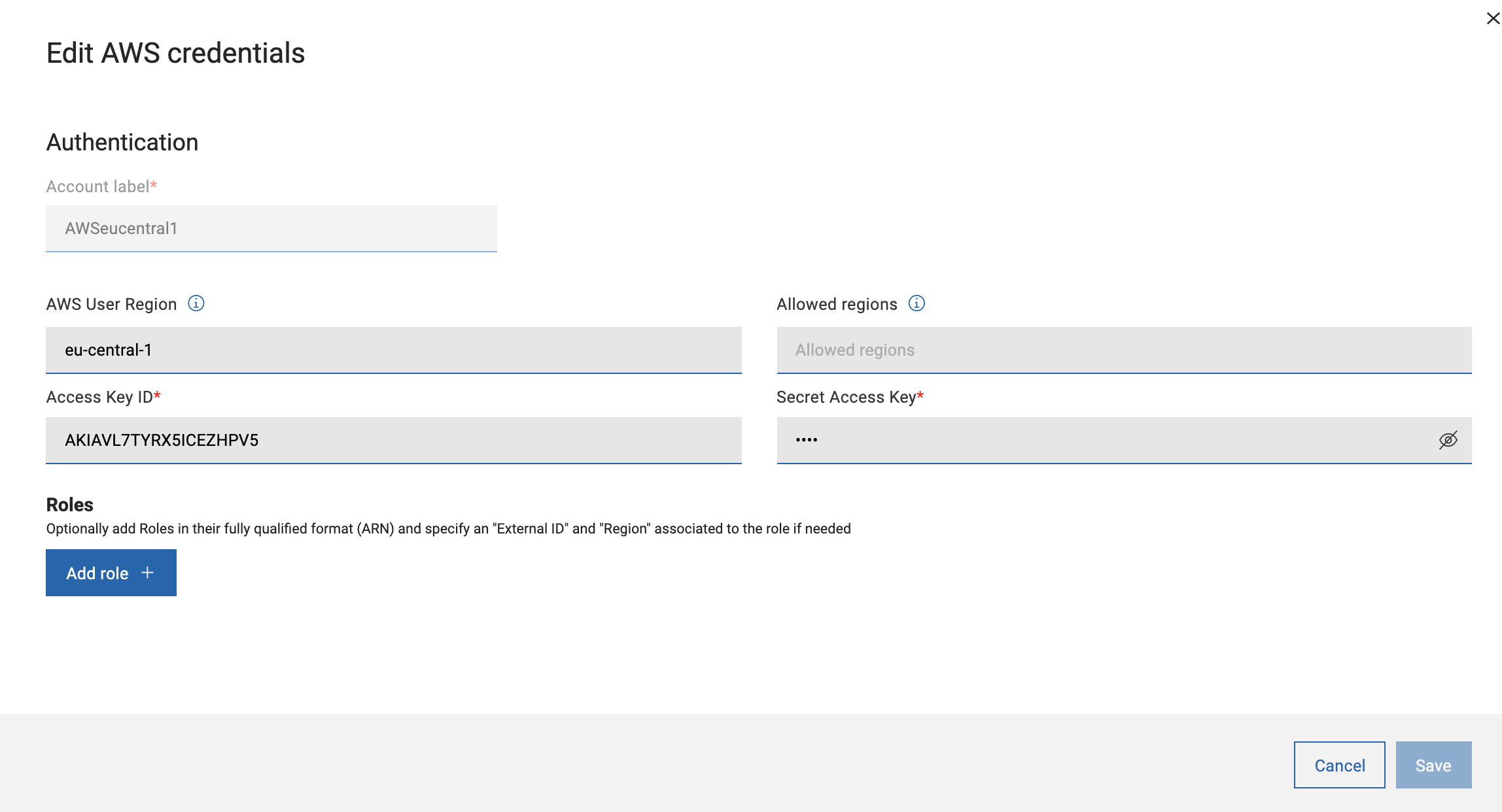
Limit AWS Regions at credential level
- In the Authentication table, click Edit credential in
the specific credential line.
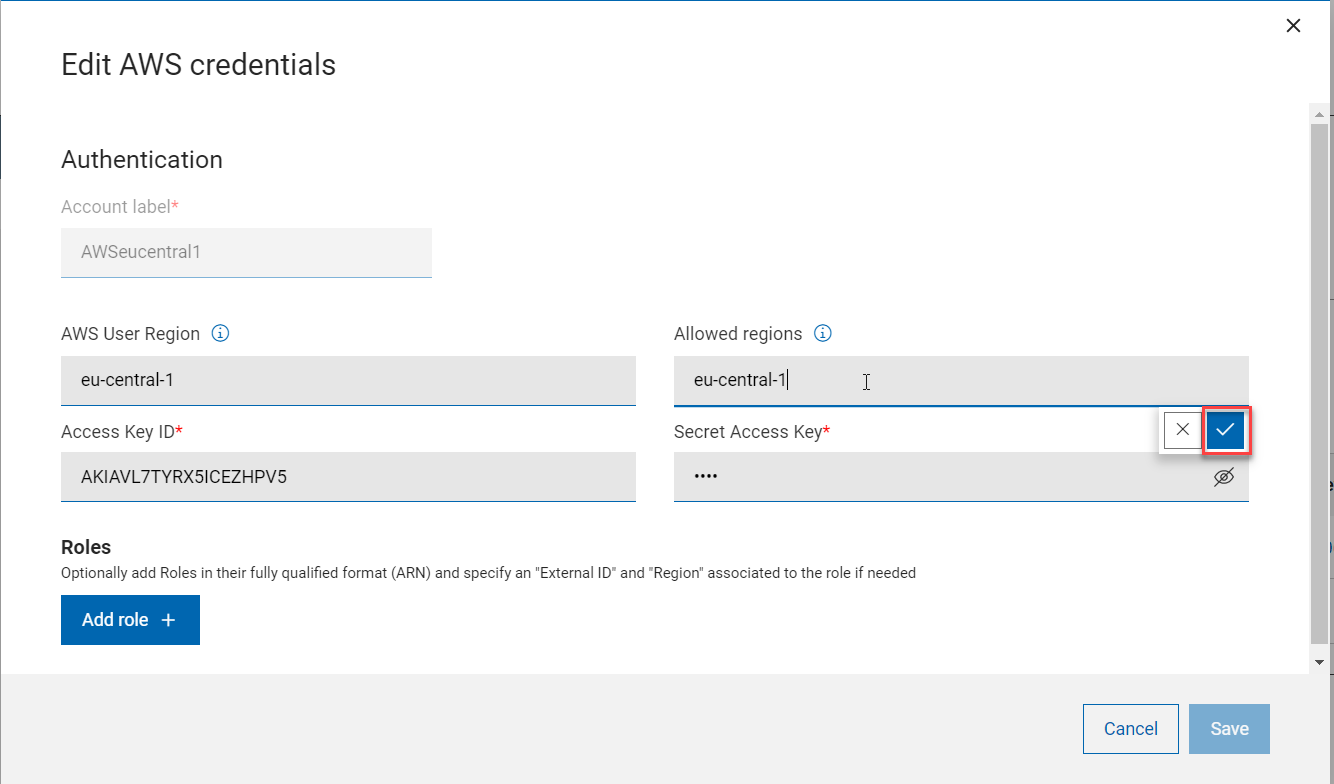
-
On the Edit AWS credentials page, enter AWS Region and click the tick mark to add it. Add one or more regions as needed.
-
Important: Enter the correct spelling for the region names, because you cannot check the name of the region for correctness.
- You can also remove a region easily as needed by clicking ‘x’ mark.
-
- After you have added all the regions you want, click Submit. This deploys the fixlet to apply the configuration change.
When changes are applied, they are visible in the related section of the AWS plugin tab, either in the Authentication table column "Allowed regions" or in the General Settings section.