Security
The sixth tab opens the Security dialog.
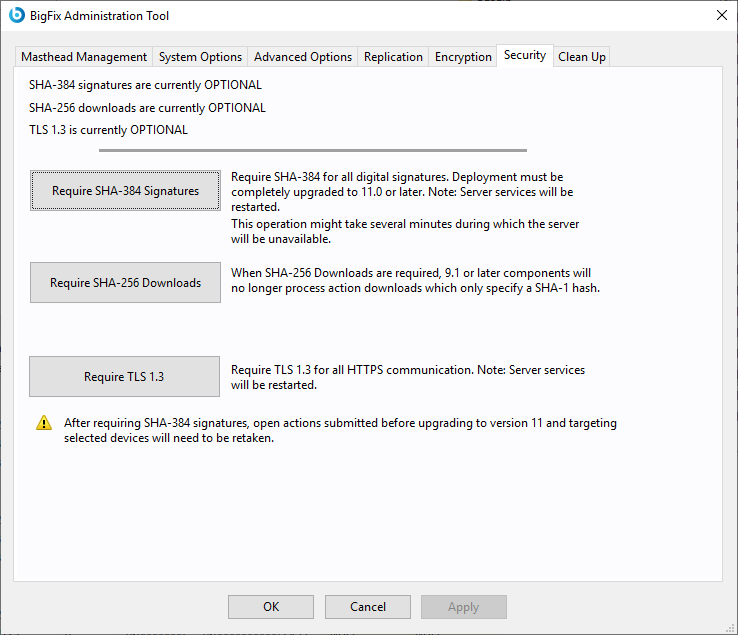
Click the Require SHA-384 Signatures button to adopt the SHA-384 cryptographic digest algorithm for all digital signatures for content verification.
- Ensure that the updated license was gathered. After upgrading to Version 11, the BigFix Server will gather a new license with the SHA-384 certificate.
- Unsubscribe from all external sites that do not support SHA-384. BigFix Administration Tool provides the list of all subscribed sites for which the SHA-384 signature is not present.
- After upgrading to Version 11, existing WebUI certificates must be recreated to include the SHA-384 signature.
Click the Require SHA-256 Downloads button to adopt the SHA-256 integrity check for file download integrity check.
To enforce SHA-384 on a Disaster Server Architecture (DSA) server in Linux environments:
You must enable it only on the primary server by running the command:
./BESAdmin.sh -securitysettings -sitePvkLocation=<path+license.pvk> -requireSHA384Signatures
You do not have to enable it on the replica servers. You might be requested to run the command:
./BESAdmin.sh syncmastheadandlicense -sitePvkLocation=<path+license.pvk> [-sitePvkPassword=<password>]
on the replica servers to ensure that the updated action site is propagated to the replica servers as well.
To enforce SHA-384 on a Disaster Server Architecture (DSA) server in Windows environments:
You must enable it only on the primary server by following the procedure described in On Windows Systems.
You must run the .\BESAdmin.exe command on the replica servers to ensure that the updated action site is propagated to the replica servers as well.
For more information about the BigFix Enhanced Security feature, the supported security configuration and enhanced security requirements evaluation, see Security Configuration Scenarios.