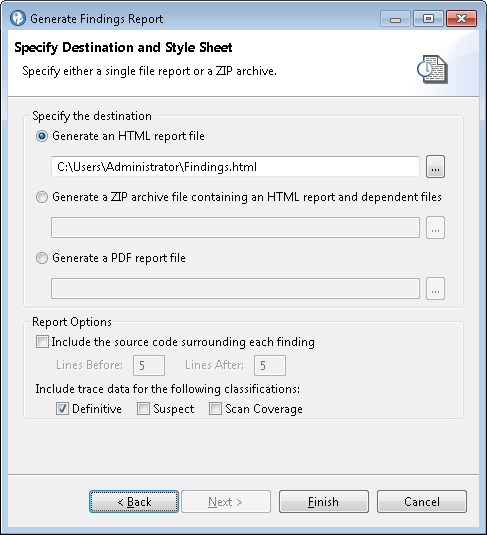
Creating findings reports
About this task
After you scan, you may want to generate reports about the identified vulnerabilities. You can generate multiple findings reports:
- Findings
- Finding by Fix Groups
- Findings by Type
- Findings by Classification
- Findings by File
- Findings by API
- Findings by Bundle
- Findings by CWE (Common Weakness Enumeration)
- DTS Activity
Note: Findings reports show detailed findings by category, similar
to the results in the findings table. The generation of findings reports
can be memory-intensive (related to https://xmlgraphics.apache.org/fop/1.1/running.html#memory) and may require up to 1024 MB of additional
system memory. If you are generating a report for a scan of a large
application and noticing memory issues, you can scan parts of your
application separately or alter your scan configuration, and then
try to generate the report or reports again.
CWE ID hyperlinks in the findings report connect to the CWE website at http://cwe.mitre.org/.
To generate a findings report: