How JavaScript source code analysis works
JavaScript™ Security Analyzer (JSA) performs static JavaScript source code analysis to detect a range of client-side issues, primarily DOM-Based Cross Site Scripting. JSA analyzes the HTML pages that AppScan® Enterprise collected during the Explore stage. JSA runs in parallel to the Test stage, or can be launched manually on existing Explore results at any time.
The issues discovered by JSA include source-level trace information showing the vulnerable source code. You can view the trace information in the Code Snippets tab of the About this Issue report of an issue. Highlighted and numbered lines in the code show, step-by-step, from source to sink, how untrusted data that enters the application gets propagated until it is used in an insecure way.
How it works
JSA uses IBM's advanced String Analysis technology to eliminate false positives and classify issues more accurately. JSA applies two stages for analyzing each page: taint (or data flow) analysis and String Analysis. In the first stage, JSA looks for a trace from source to sink that does not go through a sanitizer. If this is found, JSA validates it in a second stage using String Prefix Analysis (SPA), a variant of String Analysis.
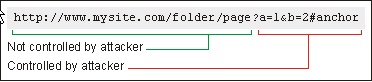
At the point of the sink, SPA checks whether the host and path parts of the URL can be controlled
by an attacker. If it is determined that the host and path parts are both fixed and not controlled
by an attacker, the issue is eliminated. If the redirect target begins with the prefix
javascript: or mailto: the issue is classified more accurately as
'DOM Based Cross-Site Scripting ' or ' DOM Based Email Spoofing'.
