URL rewriting for HTTP access services
By default, when you click a link in a mobile application that connects through HTTP access services, the link opens only if it points to content in the same application. To enable mobile applications such as HCL Connections, iNotes®, and others to render content from links to other internal sites, you can configure the HTTP access service to allow URL rewriting.
URL rewriting allows the SafeLinx Server to detect internal URLs in documents, email, and chat sessions, and rewrite them dynamically to force them through the HCL SafeLinx session. Internal URLs can be persisted by HCL SafeLinx for crash and roaming protection and are hidden from the external user.
For performance reasons, by default, SafeLinx does not scan all document types to identify URLs for rewriting. You must specify the document types you want to scan. You can enable URL rewriting for all MIME types or for selected types only.
After you enable URL rewriting and specify document types, the HTTP access service applies its default rewriting behavior automatically to links that are included in the Application server URL field. Only links that are defined by fully qualified URLs can be rendered. If documents include relative URLs, you must define specific rules to govern how to rewrite URLs that are contained in specific types of documents.
To configure URL rewriting for an HTTP access service, edit its properties.
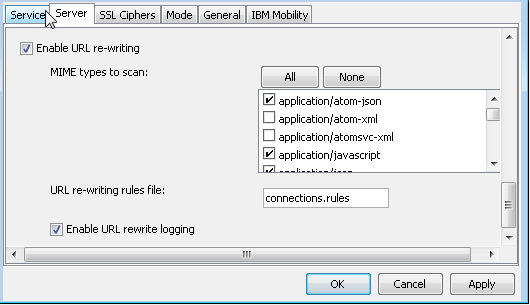
Rules for rewriting URLs are defined in a rules file stored in a directory on the Connection Manager or on a mapped drive. The rules file contains statements that allow or deny access to internal sites and specifies URL patterns to match. You can use regular expressions to specify patterns, but regular expression substitution is not supported.
As when you configure single URLs, you can specify an affinity identifier to map a string to specific servers. However, an affinity identifier is only needed when the regular expression specifies part of the of path; if the regular expression describes the server portion of a URL, the HTTP access service assigns an affinity string at random. If a specified pattern matches multiple URLs, the SafeLinx Server directs the session to the URL with the longest matching string.
For domain-based rules, or rules that do not have an affinity ID or path, the rewrite engine inserts a random string as the affinity ID. Rewrites of this type are only valid for the current session and cannot be saved as a bookmark by the external application.
To assist you in building a rules file, the SafeLinx Server logs all URL rewrite operations, as well as instances in which a detected URL does not match a rule. The log file is named for the specific service (for example, http-service0-rules.log) and can be found in the default log directory. The log entries include information about the rule, the application type, and the operation performed. You can enable or disable the rules log file from the Server page in the HTTP access service properties. The maximum size of the rules log file is 50 MB. When the log file reaches the maximum size, the service backs the file up automatically and creates a new file. The service maintains three backup logs, which are rolled over automatically.
A sample rules file (sample.rules) is provided in the SafeLinx Server installation directory, for example, /opt/hcl/SafeLinxServer or c:\Program Files\HCL\SafeLinxServer.
#
# Sample rules file, copy or rename and set in the http-service
# resource definition.
#
# Directives:
#
# ALLOW [ MAP URL | URL | DOMAIN ]
#
# DENY [ URL | DOMAIN ]
#
# Examples:
#
# MAP URL: ALLOW /ihost1/ https://internalhost1.myco.com
# URL: ALLOW https://internalhost1.myco.com
# URL: ALLOW internalhost1.myco.com
# URL: ALLOW http://((w3)|w3-[0-9]+)).myco.com
# URL: ALLOW /W3/ http://w3.ibm.com/applications/ab.*\.cgi/
// Matches any string containing "http://w3.ibm.com/applications/abXXXXX.cgi/"
// where XXXX is any char sequence.
# DOMAIN: ALLOW .myco.com
#
#
ALLOW /WWW3/ http://w3.myco.com
ALLOW /WWW3S/ https://w3.myco.com
ALLOW .appdev.myco.com
ALLOW .rtp.raleigh.myco.com
ALLOW .boston.myco.com
ALLOW /bluepages/ http://server01.myco.com/bluepages/
DENY http://server02.myco.com/