Creating the IMS™ Connect transport
You create an IBM® IMS Connect transport when you create a logical IBM® IMS Connect resource in the Architecture school of the HCL OneTest™ API. Starting from V9.2.0, the IBM® IMS Connect transport supports forwarding proxy to assist with your testing.
Before you begin
Ensure that there is at least one environment in your project. If there are no environments, you must create one. See Environment properties, bindings, and tasks.
- Service component. See Creating a service component.
- Operations for each service component. See Creating an operation.
Procedure
-
Create a logical IMS™ Connect
resource by completing the following steps:
- Open the Logical view of the Architecture school perspective and select a component in which to create the resource, or create it separately.
- Right-click the component and then select .
-
Set the binding for the IMS™ Connect
physical resource by using one of the following steps:
-
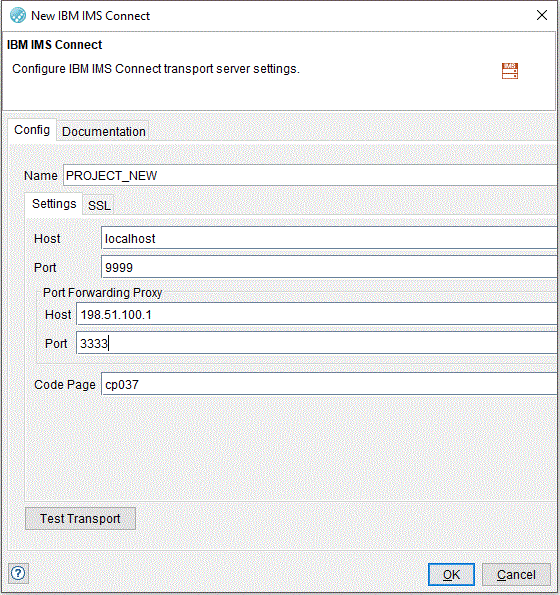
Click Settings to configure the basic transport settings.
The settings are described in the following table:
Field Description Name
The name of the IMS™ Connect Transport.
Host
The host name or IP address of the IMS™ Connect server.
Port The port number where the IMS™ Connect server is listening.
The default port for IMS™ Connect is 9941. Retain or change this port to the one you have configured.
Port Forwarding Proxy The Port Forwarding Proxy settings help you to specify a proxy through which HCL OneTest™ API connects to the computer that hosts the IMS™ Connect transport server. By using a port forwarding configuration in the HCL OneTest™ API TCP Proxy, you enable the messages sent by HCL OneTest™ API to pass through the proxy. This allows you to record them for later use in test and stub resources.
Field Description Host The host name or IP address of the proxy through which to connect to the computer that hosts the IMS™ Connect transport server.
Port The port number of the proxy through which to connect to the computer that hosts the IMS™ Connect transport server.
Code Page A suggested value for use when saving events as tests or stubs by using the events generated by a transport monitor (the Save wizard of the Recording Studio). If the events are generated by an Operation monitor, then the value from the Operation editor is used as a "suggestion" when saving tests and stubs. If the generated tests or stubs contain byte arrays or COBOL Copybook data or both in the messages, then the value is used as the encoding value in the schema properties. The code page value is also displayed in the header of IMS™ messages.
Note: The Code Page field was added to the IMS™ Connect transport editor to be used when messages are recorded since it is not possible to determine the code page from the raw TCP traffic. When you use a transport monitor to record, the Code Page field of the transport editor is used. When you use an operation monitor to record, the Code Page field from the Operation editor is used. -
Click
SSL to configure the secure socket layer (SSL) settings for the
transport. The SSL settings are described in the
following table:
Field Description Use SSL Select this check box to enable security for the transport. Selecting the check box makes the other controls on the SSL tab available. You can enable security for Testing (Client) or Virtualization (Server) or both.
Server certificates to trust All available identity stores are displayed in the drop-down list. Select one of the following menu items: Field Description Trust All To accept any certificate presented by the server, regardless of its validity. This option is the default and assumes you are focused on testing an application rather than the security of the server.
New To define a new identity store.
Identity store To specify an identity store, that contains certificates that the client is to trust. Client identities to give to the server All available identity stores are displayed in the drop-down list. If you use mutual authentication, a suitable identity is selected from the chosen identity store. Select one of the following menu items: Field Description None If the server does not request an identity.
New To define a new identity store.
Identity store To use an existing identity store. Specify an alias in the Identity field.
Certificate source All available identity stores are displayed in the drop-down list. You can select one of the following menu items: Field Description Generated To use a certificate that HCL OneTest™ API generates for you. The source for that certificate is displayed in the Signed by field.
New To define a new identity store.
Identity store To use a certificate from an identity store.
Signed by If you chose Generated in the Certificate source field, this field holds the location of a certificate within the HCL OneTest™ API installation directory that is used to generate the new certificate. This is a read-only field. Identity If you specified an identity store in the Certificate source field, use this field to specify the alias of a key in that identity store. Certificate Authorities a stub will trust All available identity stores are displayed in the drop-down list. You can select one of the following menu items: Field Description Trust All To accept any certificate presented by the client.
New To define a new identity store.
Identity store To specify an identity store that contains certificates that the stub is to trust.
Override default protocols If you are required to use a specific version of the secure sockets protocol, such as SSLv2 or TLSv1.2, enter that algorithm name here. - Click Test Transport to verify the connection works.
- Click OK.