Configuring Web Login with OIDC for web users
A Single Sign-On (SSO) option for browser clients is available using the Open ID Connect (OIDC) authorization code flow with PKCE.
Domino's Web Login with OIDC SSO functionality allows browser clients to access the Domino web server by authenticating with an OIDC provider. This form of SSO serves a similar role to basic SAML authentication for Web servers. In Domino 14.0 this functionality cannot be used to authenticate against the Notes ID vault to acquire an ID file, so does not serve as a replacement for Web Federated Login, Notes Federated Login, or Nomad Federated Login. After authenticating against a trusted OIDC provider, the user's web browser will receive a session cookie that is used to authenticate subsequent HTTP requests to that Domino server.
Procedure
- Configure HTTP bearer authentication for one or more Internet Sites as discussed
in Enabling HTTP Bearer authentication.Note: Internet Sites must be enabled for HTTP Bearer authentication in order to support Web Login with OIDC.
- Configure a trusted OIDC provider for one or more of those Internet Sites as shown in Configuring trusted OIDC providers.
- Enable Session authentication from the Domino Web Engines
tab of the Internet Site document.
In environments where all web servers can be configured to support a single identity provider, security can be improved by using SAML IdP or an OIDC provider to authenticate end users to each server, and using single-server session cookies on each of those back end servers instead of using a multi-server SSO cookie such as an LTPA Token. OIDC SSO and SAML SSO are mutually exclusive.
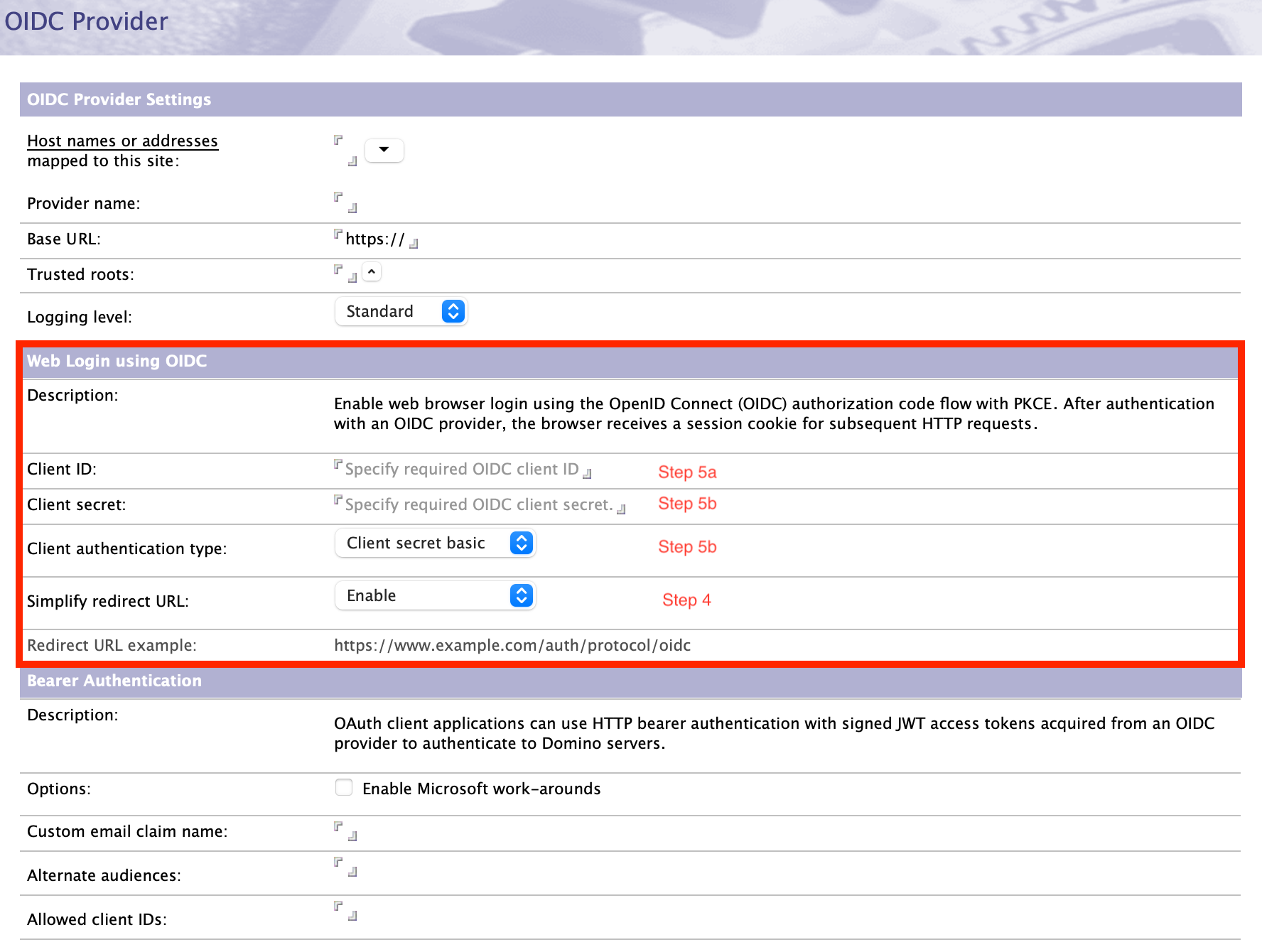
- Configure a new OIDC/OAuth 2.0 client for this internet site in your OIDC
provider. We recommend configuring Domino as a "confidential client," only
enabling the authorization code flow and requiring PKCE with S256. The redirect
URI for a Domino server listening on myserver.example.com will now have two
forms, but we recommend the new
https://myserver.example.com/auth/protocol/oidc over
the old
https://myserver.example.com/names.nsf?OIDCLogin.
Note that Web Login with OIDC can be enabled on multiple internet sites by selecting all of those internet sites in the OIDC Provider document in idpcat.nsf and configuring redirect URIs for each of those host names in your OIDC provider.
For an example of a KeyCloak configuration, see Sample KeyCloak configuration as an OIDC provider for Domino.
-
- Set the client_id configured at the OIDC provider in the Client ID field of idpcat.nsf.
- Set the client_secret configured at the OIDC provider in the Client
secret field of idpcat.nsf.
In Domino 12.0.2, the only supported authentication type was "Client secret basic". In Domino 14.0, "Client secret post" and "Private key JWT" are added. For the latter, the PEM or JWK-formatted private key should be placed in the client secret field. If "Private key JWT" is configured then Domino will publish the public key corresponding to the configured private key in jwks_uri format at the /auth/protocol/oidc/keys endpoint.
- By default, OIDC_LOGIN_ENABLE_REDIRECT=1 is enabled and will redirect to the
correct URL, but will only do so if the site can be used for Web Login with
OIDC. This allows administrators to enable a site for both HTTP bearerAuth and
for password or passkey authentication, while another site on the same server
supports Web Login with OIDC.
To disable the redirect entirely, explicitly set the notes.ini to 0.
Other configuration settings
By default, the cookies used to maintain OIDC authentication state have a lifetime of 2 minutes. This default can be changed by setting the OIDC_LOGIN_COOKIE_DURATION_SEC notes.ini to a value between 30 and 900 seconds to force end users to authenticate with their OIDC provider more quickly or to give them more time.
By default, up to 15 seconds of clock skew between the Domino server and OIDC providers is tolerated. This default can be changed by setting the OIDC_LOGIN_CLOCK_SKEW_SEC notes.ini to a value between 0 and 600 seconds.
In addition to the notes.ini variables discussed in the HTTP Bearer authentication documentation, two notes.ini variables can be used to enable additional tracing on the server console:
- DEBUG_OIDCLogin=(0,1,2,3,4)
- DEBUG_OIDC_LOGIN_REDIRECT=(0,1)
Limitations, known issues, and notes
- Per current security best practices, only the Authorization Code Flow with PKCE can be used for Web Login with OIDC SSO.
- Domino will always request "scope=openid email"
- PKCE S256 and nonce will always be used and cannot be disabled.
- The id_token received must conform to the requirements set forth in OIDC.Core with the exception that Domino will fail over to check for the "upn" Claim if no "email" Claim is found.
- Web proxies spraying requests across multiple Domino servers should be configured with session affinity to ensure that a single OIDC login attempt is not sprayed across two Domino servers.
- Web Login with OIDC is only supported on Windows and Linux servers.