Setting up the Domino credential and certificate stores
The Domino server that runs the Exchange Connector (ExConn) task must contain a credential store, as well as a certificate store configured properly for free time lookups in Microsoft 365.
Procedure
- If you don't have a credential store on the server that runs ExConn, create one according to the procedure that applies to your environment in Using a credential store to store credentials.
-
If you don't have a certificate store on that server, create one as
follows:
-
Obtain two Digicert Global Root certificates from Microsoft and add them in
certstore.nsf. You can import these certificates in one of the following
ways:
- (Recommended) If you have administrative access to the console on the
CertMgr server, you can use the CertMgr console command to import
Digicert Global Root CA and Digicert Global Root G2 (which exist in the
Domino directory) into certstore.nsf as follows:
- Run the following
commands:
load certmgr -ImportRootFromUrl https://login.microsoft.comload certmgr -ImportRootFromUrl https://graph.microsoft.comCertMgr adds the trusted root documents in certstore.nsf,
- Skip to step 4c.
- Run the following
commands:
- Alternatively, you can manually copy the pem encoded certificates for
the trusted roots and paste them into certstore.nsf on the CertMgr
server as follows:
- Locate "Digicert Global Root CA" and "Digicert Global Root G2" in the cacert.pem file in the Domino data directory.
- Copy and paste the trusted roots to certstore.nsf as follows:
- In the navigation pane of certstore.nsf, click Trusted Roots and then click Add Trusted Root.
- From step 3, copy the first certificate from the BEGIN
CERTIFICATE line to the END CERTIFICATE line, and then
click Paste Certificate.
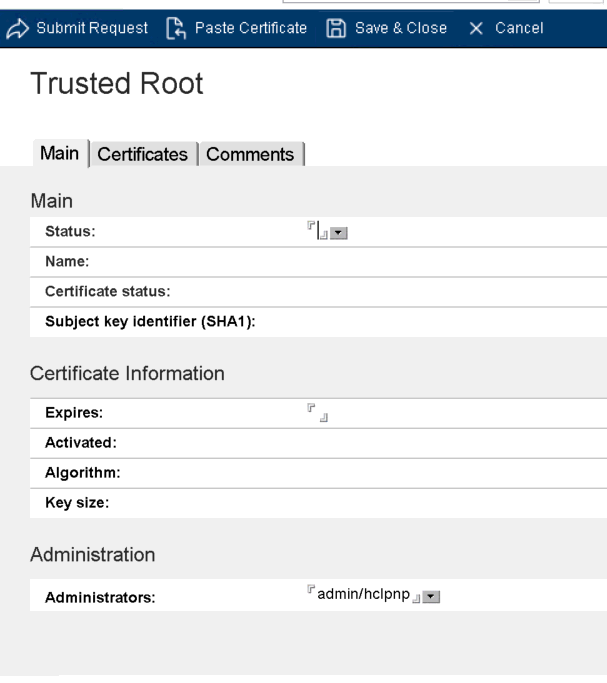
- Click Submit.
- Repeat for the second certificate.
- (Recommended) If you have administrative access to the console on the
CertMgr server, you can use the CertMgr console command to import
Digicert Global Root CA and Digicert Global Root G2 (which exist in the
Domino directory) into certstore.nsf as follows:
-
Add TLS credentials as follows:
- Restart the Domino server.
What to do next
Do the steps in Adding an application in Microsoft Azure AD