1. Issuing a Multi-Factor Authentication Certificate
To allow the use of time-based one-time password (TOTP) authentication, use the
mfamgt server command to issue a Multi-Factor Authentication
Certificate for the the organization unit (OU) or organization (O) of those users that will
be using TOTP.
Before you begin
Procedure
-
At the console of a vault server, issue the following command:
For example:mfamgmt create trustcert <OU or O to allow> <certifier ID file> <certifier password>mfamgmt create trustcert "*/O=mfatest1" cert.id sr$1ulv7bYTNote:- Make sure the certifier ID for the OU or O you want to create a Multi-Factor Authentication Certificate for is located in the Domino data directory. This ID file can be removed again from the Domino data directory once the Multi-Factor Authentication Certificate is successfully completed. Make sure you have it stored safely somewhere else before deleting.
- If you use the Domino Administrator to issue the command, you can use the Password Commands option to display a box in which to enter the password, which masks the characters in the password with asterisks. For more information, see Sending commands from the Domino Administrator console.
- Replicate the Domino directory changes to all servers in the domain.
-
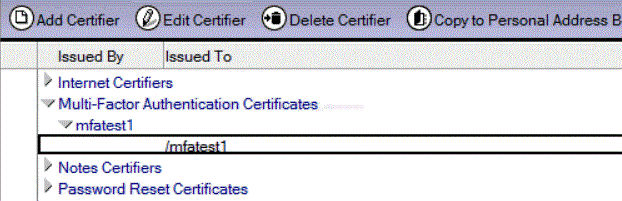
Open the Domino directory on any server in the domain, select the
Certificates view, and verify that you see a
Multi-Factor Authentication Certificate similar to the following one:
-
Issue the
show idvaultcommand and verify that output lists the MFA trust for the correct organization, as shown in bold in the following example:> show idvault [0FE0:0006-0860] ID Vault /renovationsvault (IBM_ID_VAULT\renovationsvault.nsf) [0FE0:0006-0860] Control Vault Name: /renovationsvault [0FE0:0006-0860] Control Vault Servers: server1/renovations [0FE0:0006-0860] Control Vault Servers: server2/renovations [0FE0:0006-0860] Vault Operations Key: VO-fogb-yzjy/server1/renovationsvault [0FE0:0006-0860] Servers: server2/renovations [0FE0:0006-0860] Servers: server1/renovations [0FE0:0006-0860] Vault Name: /renovationsvault [0FE0:0006-0860] Description: renovationsvault [0FE0:0006-0860] Administrators: renovations admin/renovations [0FE0:0006-0860] Servers: server1/renovations [0FE0:0006-0860] Servers: server2/renovations [0FE0:0006-0860] Administration Server: server1/renovations [0FE0:0006-0860] Administration Server: server2/renovations [0FE0:0006-0860] /renovations trusts this vault [0FE0:0006-0860] /renovations trusts /renovations for MFA [0FE0:0006-0860] /renovations trusts renovations admin/renovations to reset passwords [0FE0:0006-0860] /renovations trusts server1/renovations to reset passwords [0FE0:0006-0860] /renovations trusts server2/renovations to reset passwords [0FE0:0006-0860] Setting renovationsvaultVaultSetting uses this vault