Setting up a Relying Party Trust for Web servers on ADFS 3.0
Use this procedure to set up a Relying Part Trust in ADFS 3.0 for Domino web servers that participate in SAML authentication.
Procedure
- From ADFS, select .
- Navigate to the Relying Party Trusts folder.
- Select .
- Click Start to run the Add Relying Party Trust wizard.
-
In the Select Data Source window select Import data about the relying party from a
file, select the ServiceProvider.xml file that you exported from
the corresponding Web server IdP configuration document. Then, click Next.
Note: When you import from the ServiceProvider.xml file, values for Steps 6 - 10 are populated automatically. If you select Enter data about the relying party manually, you enter these values yourself.
- In the Select Display Name window, enter a Display name to represent the service provider, for example, Domino Renovations Web Site. Click Next.
- In the Choose Profile window, select AD FS profile and click Next.
-
In the Configure Certificate window, click Next.
-
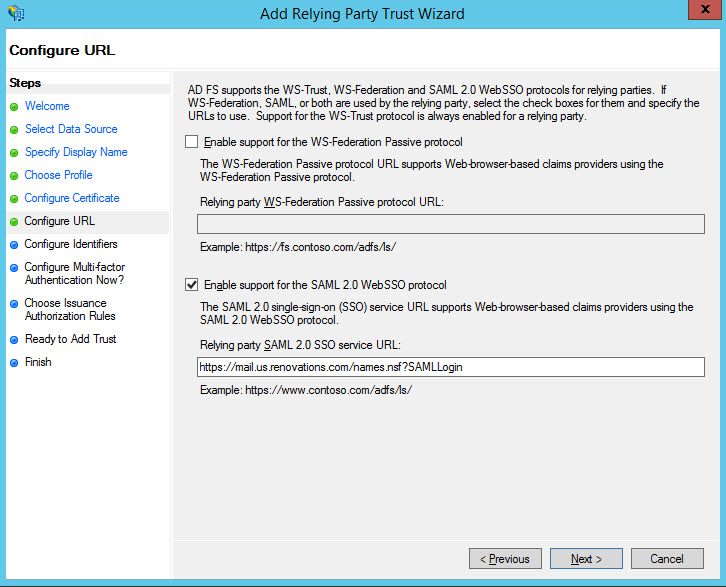
In the Configure URL window, select Enable support for the SAML 2.0 WebSSO
protocol. For Relying party SAML 2.0 SSO service URL, enter the
following URL:
https://<host>/names.nsf?SAMLLoginwhere <host> is the DNS host name of a Domino web server that will participate in federated login. For example:https://mail.us.renovations.com/names.nsf?SAMLLogin- The host name must match a host name that is specified in the Host names or addresses mapped to this site field in the web server IdP configuration document you create.
- You can specify only one web server host per Trust document. If there are multiple Web server hosts behind a load balancer or sprayer, specify the load balancer or sprayer host name here. If there is no load balancer or sprayer, repeat this procedure and create a separate Trust document for each web server.
- Each web server with a Trust document requires a corresponding IdPcat configuration document .
-
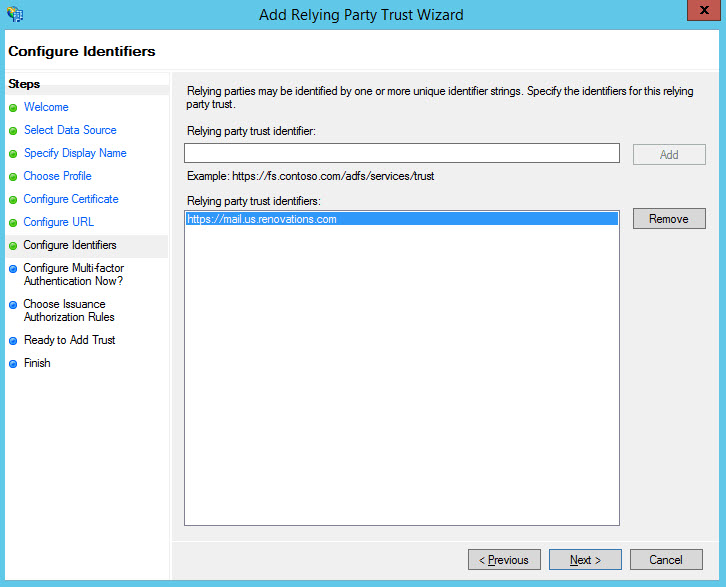
In the Configure Identifiers window, in the Relying party trust
identifier field, enter a URL to identify the web server, then click
Add and Next.
This URL must match the one that you specify in the Service provider ID field of the web server IdP configuration document. For example: https://mail.us.renovations.comNote: This URL is used only as an identifier and not for HTTP connections.
- Click Next to skip the Configure Multi-factor Authentication Now? window.
- In the Choose Issuance Authorization Rules window, select Permit all users to access this replying party and click Next.
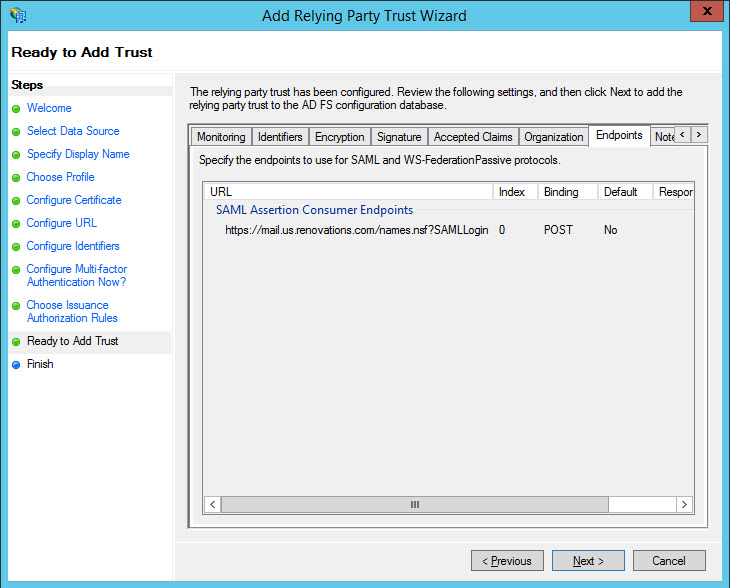
- In the Ready to Add Trust window, click Next.
- In the Finish window, select Open the Edit Claim Rules dialog for this replying party trust when the wizard closes and click Close.
- If the Edit Claim Rules dialog does not open when the wizard closes, right-click the name of the Relying Party Trust that you created, and select Edit Claim Rules...
- In the Edit Claim Rules dialog, click Add Rule.
- In the Select Rule Template dialog, for Choose Rule Type, select Send LDAP Attributes as Claims, and click Next.
-
Complete the Configure Rule dialog box:
- For Claim rule name, enter EmailAddressToNameID.
- For Attribute store, select Active Directory.
- For LDAP Attribute, select E-Mail-Addresses.
- For Outgoing Claim Type, select Name ID.
- Click Finish.
- In the Edit Claim Rules dialog, click Apply and OK.
-
In the folder: