Creating ADFS service principal names (SPNs)
To enable Integrated Windows Authentication (IWA) on ADFS, create service principal names (SPNs) to associate ADFS with a login account. SPNs allow clients to request authentication without having login account names.
About this task
If there are already SPNs for ADFS because IWA is already enabled, skip this procedure.
This procedure assumes that you use a single ADFS server. If you use multiple ADFS servers in a federation server farm, see the Microsoft document Manually Configure a Service Account for a Federation Server Farm.
Procedure
- On the Active Directory domain controller, log in to the Windows domain as the Windows administrator.
-
Run the following commands to create two SPNs, a fully-qualified name and a short name:
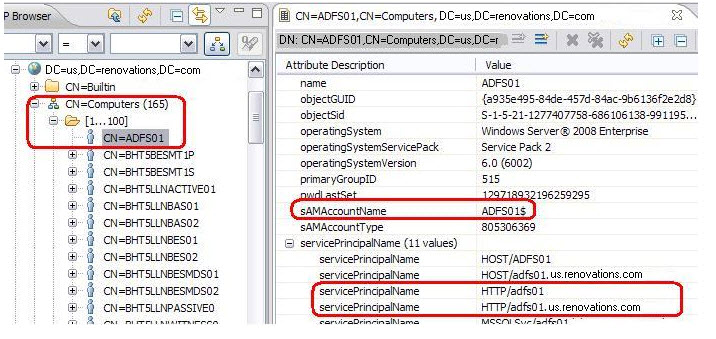
wheresetspn -s HTTP/<dns_name> <account_name> setspn -s HTTP/<adfs_server_name> <account_name><dns_name>is the fully qualified domain name of the ADFS server<adfs_server_name>is host name name of the ADFS machine<account_name>is the local service account.Note: TheHTTP/portion of the SPN is correct even though HTTPS is used to access the service. -
Run the following command to verify that the SPNs are properly created:
setspn -L <server>$
Example
For example, if the domain name is us.renovations.com, the ADFS machine host
name is adfs01, and the account name is admin, the following
commands create the required SPNs:
setspn -s HTTP/adfs01.us.renovations.com admin
setspn -s HTTP/adfs01 adminADFS01. The computer account name is ADFS01$ and the account
record shows the new service principal names.