Option 1: Configuring single sign-on based on Security Assertion Markup Language token
You can configure single sign-on based on a Security Access Markup Language (SAML 2.0) token and an external Identity Provider server.
- Application User
- A person who uses several applications in one domain and wants to single sign-on to these applications.
- Service Provider
- The application that requests the authentication service. In this case, it is BigFix Inventory.
- Identity Provider
- The service that authenticates the application users. BigFix Inventory supports only Active Directory Federation Services.
A web user authenticates to a SAML Identity Provider, which produces a SAML assertion. A SAML assertion is an XML-formatted token that is used to transfer user identity and attribute information from the Identity Provider of a user to a trusted Service Provider as part of a single sign-on request. The Service Provider consumes the SAML assertion to establish a security context for the web user.
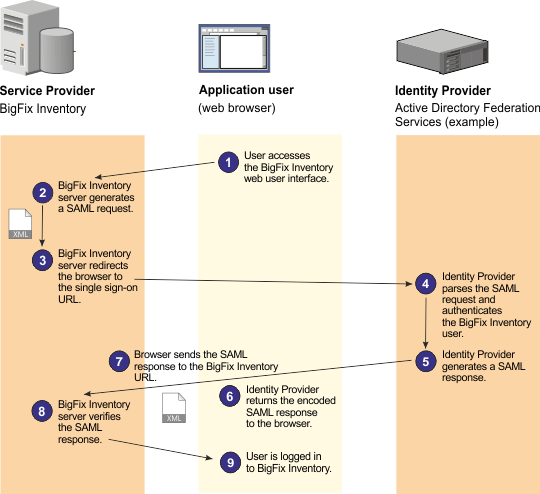
Procedure
The following scenario presents a typical workflow of configuring BigFix Inventory to work with Active Directory Federation Services. However, you might want to use other software products for enabling single sign-on in your infrastructure.