SAML-authentication configuration
MCM and BigFix Mobile supports Security Assertion Markup Language (SAML) authentication to enroll devices to protect sensitive data and ensure secure access to corporate resources.
SAML is a standard protocol for exchanging authentication and authorization data between parties, such as a user, a service provider, and an identity provider. By using SAML, organizations can enable single sign-on (SSO) authentication for their users, allowing them to log in once and access multiple applications without needing to enter credentials for each application.
Authentication Work flow
As an example, if you are using Okta as your identity provider, you can force users to enter their Okta credentials to proceed with the enrollment process.
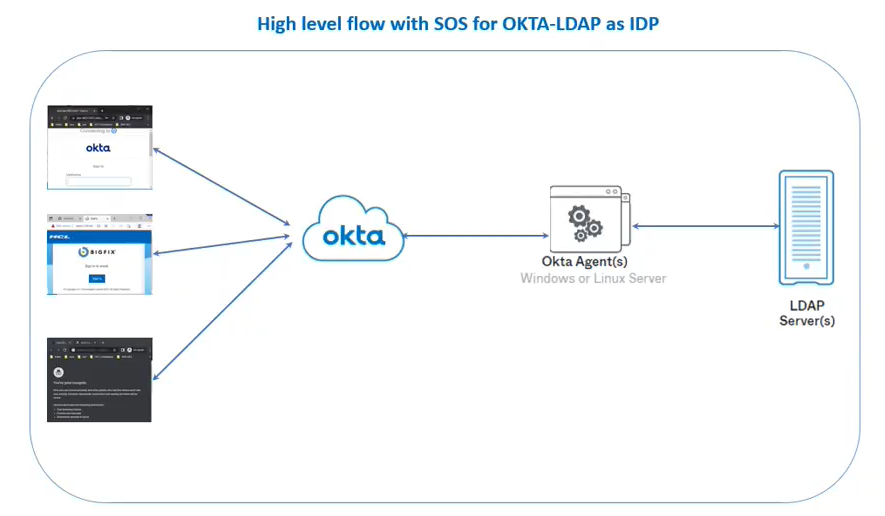
In this scenario, users would log in to a central identity provider, Okta, which would then authenticate the user's identity and issue a SAML assertion. The device would also be authenticated and authorized by the MDM system. Once both the user and the device have been authenticated, the user would be granted access to the requested application or resource.
Supported operating systems and versions
- Windows 10, Windows 11
- Android
- macOS
- iOS
- iPadOS
Prerequisites
-
Active Okta subscription: To integrate Okta with MCM and BigFix Mobile, you need an active Okta subscription with access to the necessary features and functionalities required for MDM integration.
-
Active Directory or LDAP: Okta integrates with Active Directory or LDAP to import user and group information and synchronize it with the MDM solution.
-
If your identity service is AD/LDAP:
-
Okta must be integrated with LDAP using okta agent. For information on how to integrate Okta with LDAP server, refer to the Okta documentation at https://help.okta.com/en-us/Content/Topics/Directory/directory-integrations-main.htm.
- LDAP users must have mail and UID configured in LDAP server for okta integration to work. For more information, refer to official Okta documentation at OKTA_Documentation_For_Reference.
-
- If your identity service is Azure AD, Okta must be integrated with Azure using okta agent. For information on how to integrate Okta with Azure AD, see Integrating Azure Active Directory using SAML.
Configuration
Complete the following steps to configure SAML authentication.Enrollment flow
If the user is accessing BigFix MCM enrollment page for the first time, the user will be re-directed to Okta login page for authentication. Once authenticated, the user can continue with the enrollment flow.
If the user has already logged in, the user can continue to enroll, as SSO authentication is enabled through SAML. For more information, see SAML-authenticated enrolment flow.