Set up Vault
Vault is the open source secret engine that BigFix uses to secure, store and tightly control access to tokens, passwords, certificates, encryption keys for protecting secrets and other sensitive data using a UI, CLI, or HTTP API.
About this task
For more information about Vault, see https://www.vaultproject.io/ by HashiCorp.
- Users can set up their own Vault instance and provide details and appropriate
access keys to store recovery keys and obtain information about the recovery
key.
A secret engine named 'bigfix' of type KV version 2 must be created. A user with write permission must be created with the userpass auth method. An ACL policy of:
path "bigfix/data/*" { capabilities = ["create", "update",] } path "bigfix/metadata/*" { capabilities = ["list","read"] }
or
-
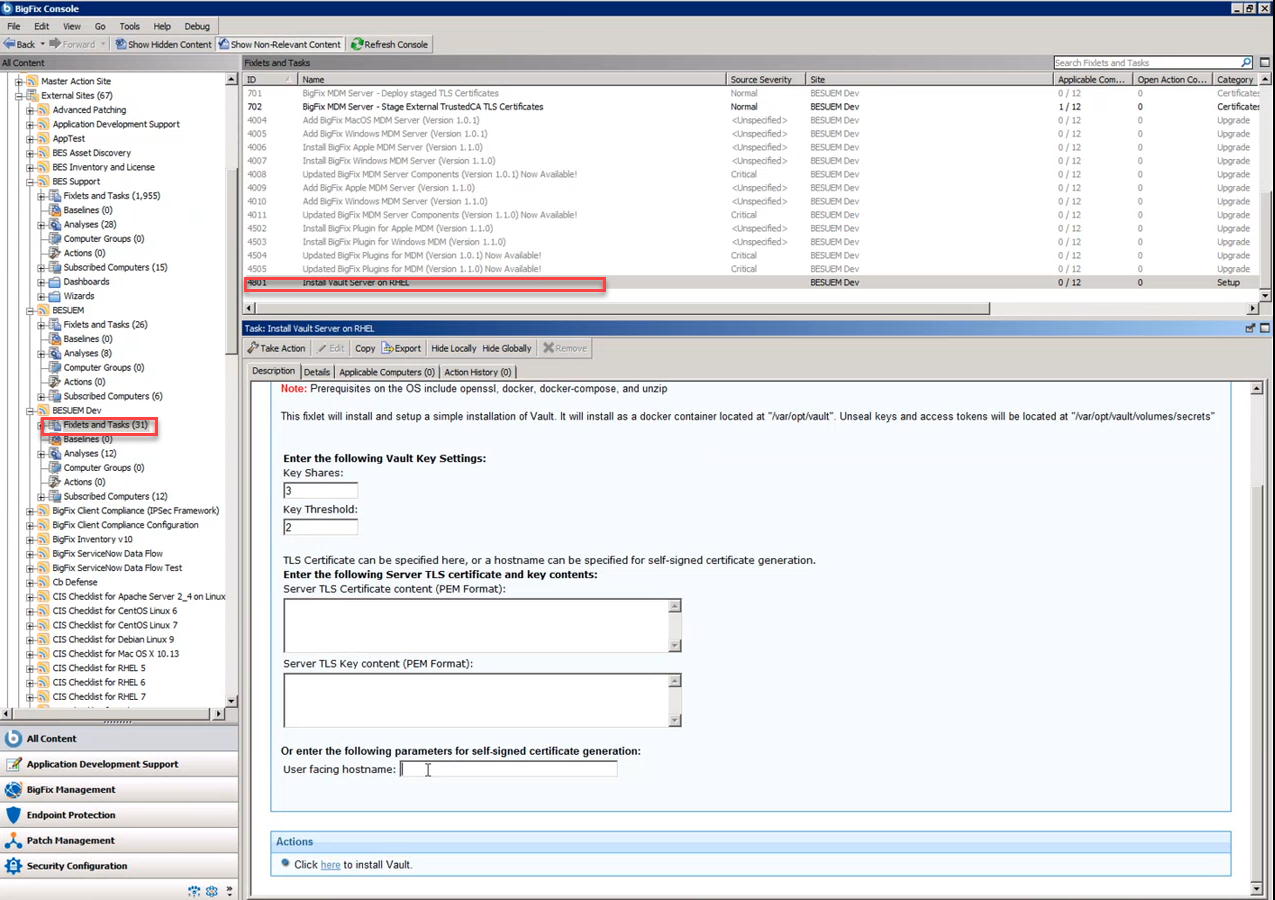
Deploy Vault on a specified system and set up with default security configuration, by running the Fixlet from BESUEM site to install Vault server. This automates the setup of the Vault with default security settings (specified unseal key, automatically unsealing, self-signed certificate or specified). On Linux, Vault is deployed as a docker container, and on Windows Vault is deployed as an application and a scheduled task launches upon system start up. Unseal and access keys are logged, and users must save those keys somewhere, configure them in the WebUI for plugin configuration, key escrow status retrieval. Users can provide SSL certificate or user-facing host name. More information can be found in the Fixlet description.