Migrating to the current version of AppScan Source
This topic contains migration information for changes that have gone into this version of AppScan® Source. If you are upgrading from an older version of AppScan Source, be sure to note the changes for the version of AppScan Source that you are upgrading and all versions leading up to this current version.
Migrating from Version 9.0.2
- New rule attributes may result in findings classification changes in existing scans
- Automatic lost sink generation
New rule attributes may result in findings classification changes in existing scans
After
Version 9.0.2, Attribute.Likelihood.High and Attribute.Likelihood.Low rule
attributes were introduced. When these attributes are used, AppScan
Source can more
accurately determine if findings are definitive and/or suspect. As
a result, if you scan source code in AppScan
Source Version 9.0.2
or earlier, you may find that some findings classifications will change
when the same source code is scanned in product versions after 9.0.2.
This will be most noticeable for findings related to highly exploitable
web sources - or for property or environment sources that are less
exploitable.
These rule attributes are used by default. You can disable them, as follows:
- Open <data_dir>\config\ipva.ozsettings in
a text editor (where <data_dir> is the location of your
AppScan
Source program data, as described in Installation and user data file locations).
Locate the
allow_likelihoodsetting in the file. This setting will look similar to:
In this setting, modify the<Setting name="allow_likelihood" value="true" default_value="true" description="Allow the processing of the Likelihood attributes to help determine trace confidence based on the source API" display_name="Allow Likelihood" type="bool" />valueattribute. If the attribute is set totrue, this setting will be on. If it is set tofalse, AppScan Source will not use these rule attributes during scans. - Save the file after you have modified this setting and start or restart AppScan Source.
Automatic lost sink generation
After Version 9.0.2, automatic lost sink resolution was introduced for traces that end in getters/setters and methods that return boolean values. This is done by automatically inferring markup for these application programming interfaces (API). As a result, if you scan source code in AppScan Source Version 9.0.2 or earlier, you may notice changes in findings results that contained unresolved lost sinks when the same source code is scanned in product versions after 9.0.2.
Automatic markup generation is on by default. You can disable it if you want to use other means of lost sink resolution such as custom rules, as follows:
- Open <data_dir>\config\ipva.ozsettings in
a text editor (where <data_dir> is the location of your
AppScan
Source program data, as described in Installation and user data file locations).
Locate the
automatic_lost_sink_resolutionsetting in the file. This setting will look similar to:
In this setting, modify the<name="automatic_lost_sink_resolution" value="true" default_value="true" description="This setting tries to perform automatic lost sink resolution by assuming taint propagation for getters, setters and APIs which return boolean with no arguments." display_name="Auto Lost Sink Resolution" type="bool" />valueattribute. If the attribute is set totrue, this setting will be on. If it is set tofalse, AppScan Source will not automatically generate markup for these methods. - Save the file after you have modified this setting and start or restart AppScan Source.
Migrating from Version 9.0
AppScan Enterprise Server authentication: Migration considerations for replacement of the IBM® Rational® Jazz™ user authentication component with IBM WebSphere® Liberty
- Migrating from an Enterprise Server that only has local Jazz users: In this upgrade scenario, the former Jazz users will appear in the AppScan Source Database as AppScan Enterprise Server users, however, they will not be valid. These users can be removed from the Database - or they can be converted to AppScan Source users. Contact HCL Support for information on enabling former Jazz users in AppScan Source.
- Migrating from an Enterprise Server that was configured with LDAP: During the Enterprise Server upgrade, you have the option of configuring the Enterprise Server with LDAP again. If you do this, existing users will still work in AppScan Source.
- Migrating from an Enterprise Server that was configured with Windows™ authentication: If your Enterprise Server was configured with Windows authentication, existing users will work in AppScan Source, provided the new Enterprise Server Liberty is configured to use Windows authentication.
Migrating from Version 8.7
- Changes to findings classifications
- Default settings changes that will improve scan coverage
- Restoring AppScan Source predefined filters from previous versions
Changes to findings classifications
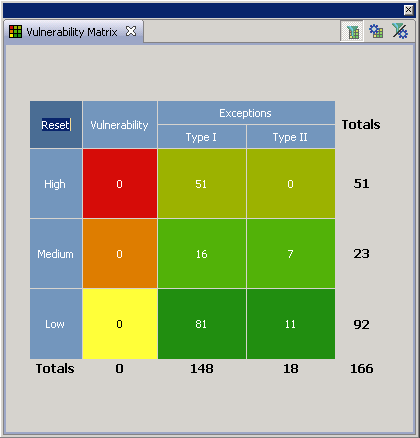
After Version 8.7, findings classifications changed. This table lists the old classifications mapped to the new classifications:
| Findings classifications prior to AppScan Source Version 8.8 | Classifications as of AppScan Source Version 8.8 |
|---|---|
| Vulnerability | Definitive security finding |
| Type I Exception | Suspect security finding |
| Type II Exception | Scan coverage finding |
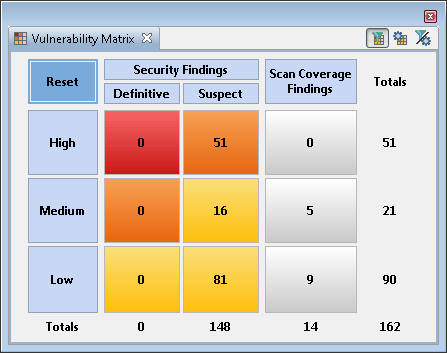
An example of these changes can be seen in the Vulnerability Matrix view.
As of Version 8.8, the view looks like this:
Default settings changes that will improve scan coverage
As of AppScan Source Version 8.8:
- The default value of
show_informational_findingsin scan.ozsettings has changed fromtruetofalse. - The default value of
wafl_globals_trackingin ipva.ozsettings has changed fromfalsetotrue. This setting enables AppScan Source to find dataflow between different components of a framework-based application (for example, dataflow from a controller to a view).
The change to show_informational_findings will
result in assessments not including findings with a severity level
of Info by default.
Restoring AppScan Source predefined filters from previous versions
In AppScan Source Version 8.8, predefined filters were improved to provide better scan results. If you need to continue using the predefined filters from older versions of AppScan Source (archived filters are listed in AppScan Source predefined filters (Version 8.7.x and earlier)), follow the instructions in Restoring archived predefined filters.
