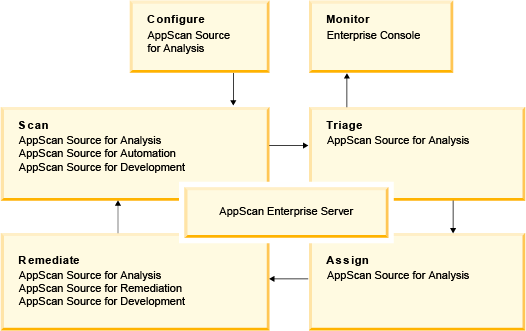
Workflow
After installation, deployment, and user management, the AppScan® Source workflow consists of these basic steps.
- Set security requirements: A manager or security expert defines vulnerabilities and how to judge criticality.
- Configure applications: Organize applications and projects.
- Scan: Run the analysis against the target application to identify vulnerabilities.
- Triage and analyze results: Security-minded staff study results to prioritize remediation workflow and separate real vulnerabilities from potential ones, allowing triage on critical issues to begin immediately. Isolate the issues you need to fix first.
- Customize the Knowledgebase: Customize the AppScan Source Security Knowledgebase to address internal policies.
- Publish scan results: Add scan results to the AppScan Source Database or publish them to the AppScan Enterprise Console.
- Assign remediation tasks: Assign defects to the development team to resolve vulnerabilities.
- Resolve issues: Eliminate vulnerabilities by rewriting code, removing flaws, or adding security functions.
- Verify fixes: The code is scanned again to assure that vulnerabilities are eliminated.