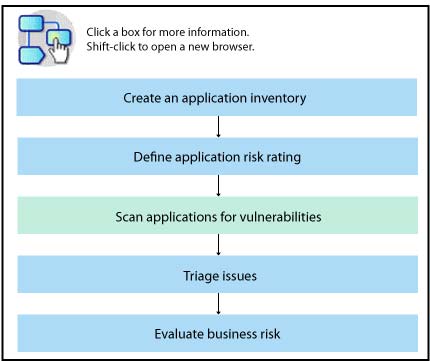
Configuring a security scan using scan properties in AppScan Enterprise
Security scans should be performed in a preproduction environment, such as on a staging or Quality Assurance server. Doing so helps you contain the risks associated with performing security scans. Your preproduction environment should mirror the production environment as much as possible; the application should have the same executable files in both environments so that you know you are thoroughly testing your exposed applications. Security scans should also be integrated into your Software Development Life cycle (SDLC) process so that you can catch security issues before they make their way into your production environment.
Before you begin
- Ensure the application is in a development or testing environment.
- Establish a time window with the owners of the application (developers or QA) for scanning the application. The application must be up and running and stable for the time period you will be scanning it with AppScan® Enterprise Server. There should not be any changes being made to the application during scanning.
- Decide upfront whether you want to perform a Manual Explore or
an automatic crawl:
- A Manual Explore means you will be indicating the exact URLs for the scan to test in the configuration (the scan will not automatically crawl to discover new URLs). Use this method for web applications that require a lot of user interaction to navigate the application or if you would like to just test a specific area of your application.
- An automatic crawl means you will be configuring the scan to automatically discover more URLs to test in your web application. Use this method for an application that has a lot of static links and does not require a lot of user interaction.
 ) icon.
) icon. icon). Select 'Cookie' as the
icon). Select 'Cookie' as the  ) to launch Manual Explore. You can also use Manual
Explore to manually select URLs if you want to restrict your scan
to a Manual Explore. The web application will launch in a separate
browser window. Simulate any manual navigation or form fill in this
window; then close the window and save your form results.
) to launch Manual Explore. You can also use Manual
Explore to manually select URLs if you want to restrict your scan
to a Manual Explore. The web application will launch in a separate
browser window. Simulate any manual navigation or form fill in this
window; then close the window and save your form results.